The thought of your WordPress site being hacked is terrifying. A single attack can cause system downtime, data loss, and reputational damage – it's a nightmare scenario.
But it doesn't have to be.
At Patchstack, we've seen firsthand the devastating impact of WordPress vulnerabilities. That's why we created this guide: to equip you with the knowledge and strategies to defend against cyber threats.
In this comprehensive WordPress security guide, you will learn:
- Why you need to secure your WordPress site.
- Why and how WordPress sites get hacked.
- Practical ways you can easily improve your WordPress security.
This guide has been written by security experts at Patchstack, a WordPress security company focusing on vulnerabilities as the core security issue.
At Patchstack, we have seen many WordPress websites hacked, taken over, and their private information stolen – all because they overlooked a single vulnerability within their website.
That’s all it takes.
If one loophole in your website is discovered and exploited, you risk losing your digital presence.
WordPress security is a vast topic, as there are many techniques for securing your website and hosting server against malicious attacks.
In this guide, we will aim to cover every method there is to secure a WordPress website.
Before we begin, we should mention that it is not necessary to implement every single technique discussed in this article. You can use this guide as a reference to create a security policy for your websites. With that said, the following methods are highly recommended by our team, while others will depend on your use case:
- Use a vulnerability management solution (like Patchstack).
- Use a web application firewall to block IPs known to exploit sites.
- Have multiple website backups.
- Keep your WordPress core, theme, and plugins up to date.
- Use the latest version of PHP and other server software, such as Apache, LiteSpeed, and Nginx.
- Use strong passwords and usernames with two-factor authentication.
- Secure your WordPress admin login URL.
- Protect SSH access (if applicable)
Why do you need to secure a WordPress website?
You might be under the impression that only big businesses with thousands of customers get hacked and that hackers won’t spend time or effort hacking smaller websites as it is not worth their time…
…but this couldn’t be further from the truth.
In our State of WordPress Security In 2024 report, we highlighted that a large number of cyber-attacks are automated – malicious robots crawl the internet throughout the day looking for vulnerabilities, and they don’t discriminate between big or small businesses.
With so many malicious bots continuously scanning WordPress websites for vulnerabilities, it is vital to invest in website security.
It is essential for agencies and website owners to understand that without a proper security policy, they risk losing their time, investment, data, domain, and much more.
What are the most common WordPress security issues?
As mentioned above, hackers have built bots and scanners that can find and automatically try to hack into your WordPress websites. These bots carry out many types of attacks. One of the most notorious involves brute force attacks on the login page, in which bots keep entering vast numbers of username and password combinations on your website’s login page in the hope of cracking the combination.
Once the bot gains access, it will notify its hacker, who will gain immediate access to your WordPress dashboard to carry out further attacks. Choosing strong, unique passwords will stop these brute-force bots from succeeding. Better yet, consider 2FA.
Another common attack on WordPress websites is a DDoS attack, in which a set of compromised servers or websites try to send vast numbers of requests to a WordPress website to waste the victim website’s server resources and eventually render the website unreachable. The best solution to this kind of attack is blocking the attacking IPs at a network level.
However, the most common attack is gaining access to a WordPress website by exploiting a vulnerability in a theme or plugin.
At Patchstack, we see that most compromised websites had a vulnerable plugin that wasn’t updated as soon as a patch was available. That is why it’s vital to have a vulnerability monitoring service that offers vPatching. This service can help detect issues with the plugins you are using and fix them even before an official patch is released, keeping your website secure and protected at all times.
Why do WordPress sites get hacked?
WordPress is used on millions of websites, so it’s no surprise that many hackers invest their time finding vulnerabilities to access WordPress websites.
WordPress also has a large open-source community that builds plugins, themes, and other scripts to extend WordPress’ functionality. Since thousands of plugins and themes are being built and are continuously updated with new functionalities, there are bound to be vulnerabilities within the code that hackers can use to attack WordPress websites.
To combat these hackers, an active community of security researchers invests its time in finding security loopholes within the WordPress core, plugins, and themes before they are exploited.
At Patchstack, we have always actively encouraged security research. As part of this effort, we established the Patchstack Alliance – a global team of security experts combined with a bug bounty program that encourages further in-depth research into any current WordPress security issues.
Will my site be protected from all the vulnerabilities?
Many people ask us at Patchstack, “Is there a guarantee that my website will be safe?” The answer is no, but you can take security precautions to block the most common attacks. These make it much harder to access your website, and you can secure your data by having backups that you can easily restore if your website does ever get hacked.
The role of the hosting provider in WordPress security
WordPress hosting is big business, and since we trust hosting providers with our digital assets, it only makes sense to know what level of security your WordPress hosting provider has.
There are many types of hosting services, and although it’s beyond the scope of this article to go into detail about each one, there’s one particular aspect to look out for.
If you are using (or considering using) a hosting service that calls itself a specialist WordPress hosting provider or a “Managed WordPress Hosting” provider, then that should be a good indication that your hosting service provides the support, speed, and security needed for WordPress websites.
A good WordPress hosting service should provide some level of security and offer features such as:
- Timely server software updates.
- Automated backups.
- DDoS attack mitigation or easy integration with third-party services.
- Secure connections, SSL certificates, and SSH/SFTP access.
- Using secure hosting networks/servers.
- Uptime monitors with logs of incoming traffic.
- Real-time support.
Essential WordPress security practices
Keeping WordPress updated
The best method to avoid vulnerabilities is to have an up-to-date version of all WordPress-related software. This includes WordPress core, themes, plugins, and any other third-party code or scripts that you may be using.
In our blog post about the WordPress Core 6.5.5 security update, we discussed how WordPress websites can be hacked if you are using a vulnerable version. If you are using an older version of WordPress that is no longer supported, you are leaving many backdoors open for attackers to take over the website.
This is also true for plugins and themes. Some websites have a great many plugins installed, and have older theme files on their WordPress websites. It is best to remove unwanted plugins and themes if they are no longer needed (not just to disable them, but to fully uninstall them).
If you have multiple WordPress websites, updating and testing everything on every website can take much of your time. That is why it’s a best practice to use a service that automates checking outdated plugins, themes, and WordPress core and gives you a single dashboard from which you can update all your websites easily.
Our WordPress security app, Patchstack, provides a central dashboard from where you have complete control over multiple WordPress websites.
Patchstack automatically scans and notifies you immediately if any outdated software version is installed on your WordPress website. You can also turn on the auto-update feature in Patchstack to automatically apply any new updates to the WordPress core, themes, and plugins as soon as they are available.
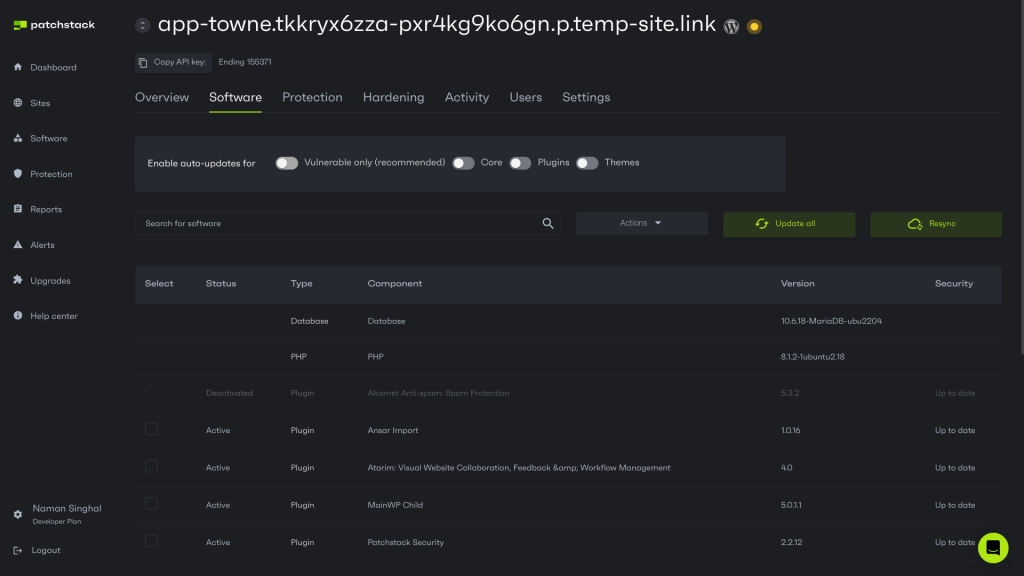
Use complex passwords and usernames
In a previous post, we explained how to protect WordPress against brute-force attacks. We mentioned that using common usernames, such as “admin,” and passwords, such as “drowssap,” will make it much easier for brute-force attacks to succeed.
The "admin" username is a prime target for brute-force attacks because it is the default administrative account in many WordPress installations.
To mitigate this risk, create a new administrator account with a unique username, then delete the original "admin" account.
It is also recommended to use a complex combination of passwords and usernames for each user on your WordPress website to make it more challenging for hackers to attack your site.
If you’re unsure how to change your WordPress password, you can refer to our guide on how to change (or reset) a WordPress password.
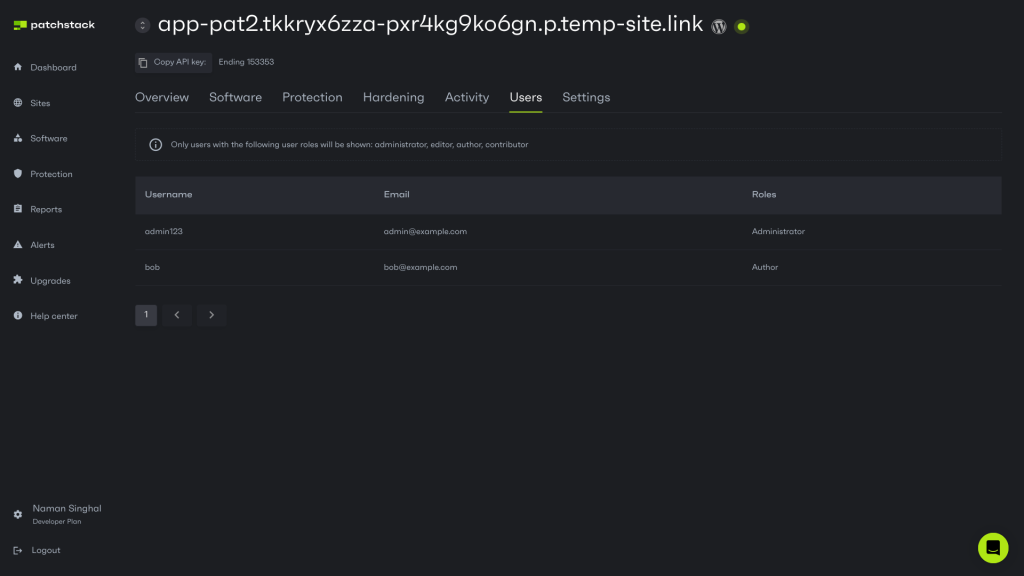
Use the principle of least privilege
Simply using a complex password is not enough to protect your website. To more fully harden your WordPress security, we strongly recommend implementing the principle of least privilege.
The principle of least privilege dictates that users should only have the minimum level of access necessary to perform their tasks.
In WordPress, this means carefully assigning user roles and permissions. Instead of giving everyone administrator access, use editor, author, or contributor roles as appropriate. For plugins that offer additional user roles, review these carefully and assign them judiciously.
Patchstack can assist in this process by monitoring user activities and alerting you to suspicious behavior, such as multiple failed login attempts or unexpected privilege escalations.
Harden SSH settings
Secure Shell (SSH) is a critical component for any hosting environment, and improperly configured SSH servers can lead to security breaches. If your hosting provider offers SSH access to your servers, then you are responsible for protecting it.
First, you should always use SSH keys instead of passwords, as SSH keys are significantly more secure and resistant to brute-force attacks. You can generate a strong key pair and disable password authentication on your server without additional charges.
You should also never use the root account for SSH access. Instead, we recommend creating a separate user account with sudo privileges. This adds an extra layer of security by requiring an additional step to perform system-level changes.
We also suggest changing the default SSH port (22) to a non-standard port, which can help reduce automated scanning attempts. However, this is security through obscurity, and should not be relied upon solely.
To further protect your SSH service against brute force attacks, we recommend using an advanced service such as fail2ban. This service monitors log files and automatically blocks IP addresses that show malicious signs, such as multiple failed login attempts.
Force user logout in WordPress
In our guide to forcing user logout in WordPress, we discussed why forcing user logout in WordPress is a powerful security measure – especially when you either suspect unauthorized access or need to implement system-wide changes.
We mentioned that by changing the session tokens, you invalidate all existing sessions, forcing users to log in again. This can be particularly useful after detecting a security breach, updating user roles, or implementing new security policies.
While it is a powerful feature, it's important to use it judiciously, as it can disrupt user activities if used too frequently.
If you want to protect your website, Patchstack's security suite offers additional features that complement this logout functionality. For instance, you can restrict access to the WordPress dashboard to specific IP addresses and only during certain times of the day.
Security headers
Security headers are a critical yet often overlooked aspect of WordPress security. These HTTP response headers instruct browsers on handling your site's content, significantly enhancing protection against attacks.
Implementing proper security headers can help you defend against cross-site scripting (XSS), clickjacking, and many other common web-based attacks.
Read our previous posts to learn more about various security headers:
- How to Avoid Caching Sensitive Information In WordPress - Patchstack
- How To Prevent Image Hotlinking in WordPress - Patchstack
Use secure WordPress hosting with updated software
We mentioned earlier that many WordPress hosting providers do offer some level of security for your WordPress websites and hosting servers. One essential security feature that a hosting provider should have is the ability to easily create, schedule, or automate backups and restore your website’s older versions if your site is compromised.
Some noteworthy WordPress hosting providers that provide good security, along with optimized servers, include:
- WP Engine
- Pagely
- Plesk
- One.com
- Hostinger
- A2Hosting
- Convesio
- Gridpane
Note: The above list is not exhaustive, and we recommend that you conduct your own research when choosing a hosting provider that will fulfill your security needs.
Use an uptime monitor
Some hosting companies do provide a built-in uptime monitoring service. However, installing an independent uptime monitoring service on your website is still a good idea because if your entire hosting provider goes down, the built-in monitoring service won’t notify you about this outage.
It is important to note that if your website is offline, that doesn’t mean it is hacked or under attack. It could be that your hosting server is experiencing an outage. But in any event, it is a good idea to be warned as soon as your website goes down so that you can investigate the cause and take necessary action.
Read our post on how to add uptime monitoring on a WordPress website to learn what it takes to configure an effective monitoring setup.
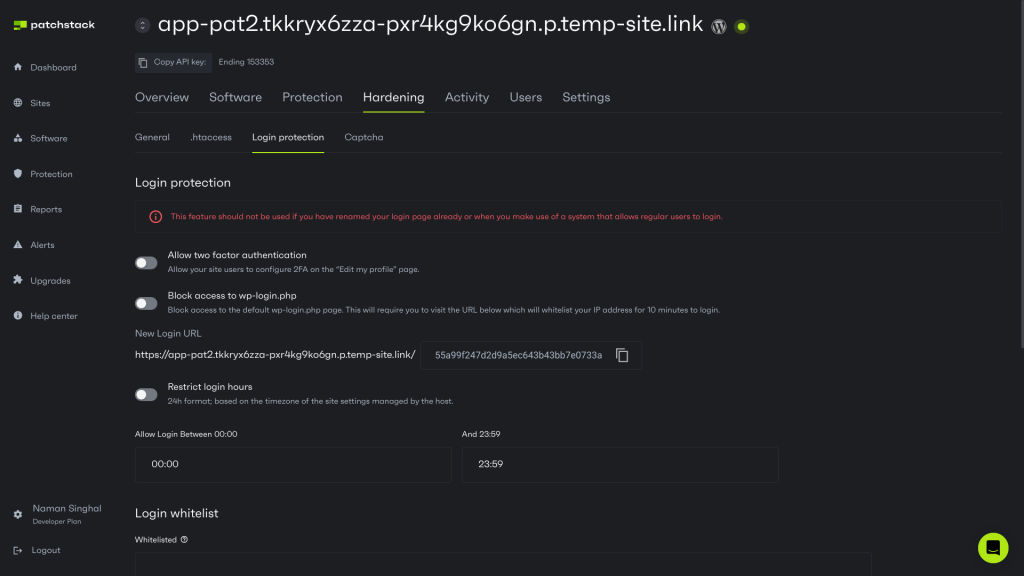
Change the default WP-login URL
As mentioned, automated bots continuously try to gain access to WordPress websites by conducting brute-force attacks on the /wp-admin or /wp-login.php URLs. Disabling the default login URL and using a custom URL to log in to your WordPress dashboard protects you from many automated attacks.
It is important to note that you shouldn’t simply redirect your default login URL to a custom URL. Instead, you should restrict access to the/wp-admin and /wp-login.php URLs to protect your website. If you use Patchstack, you can enable this feature under Hardening > Login Protection with only a few clicks. You can read about this feature in our post, "How to Change the Default WordPress Login URL".
Use a vulnerability monitoring service for early detection
Blocking hacking attempts is a vital strategy, but fixing or patching vulnerable software even before the vulnerability is disclosed to the public is an even stronger approach to website security.
Patchstack offers a 48-hour early warning service that continuously monitors WordPress websites for vulnerabilities and notifies you if outdated or vulnerable software is installed.
The best part is that if your website does have any vulnerabilities, Patchstack notifies you and blocks malicious attacks using its vPatching functionality, even if you haven’t updated it.
Have a solid backup solution
It is highly recommended that you have a multi-tiered backup policy to be better prepared for any potential loss of a website and its data. You should create multiple website backups and store them in multiple locations.
For example, have a backup of your website files and database on your hosting server and an offsite backup on a cloud server or storage service such as (Dropbox, Amazon S3, or Google Drive).
Many hosting providers offer a backup service, but if your provider does not offer this functionality, you can follow the steps described in our post, “How to Back Up a WooCommerce Store”.
If you want recommendations for backup plugins and services, read our post on the best WordPress backup plugins and services in 2024 (ranked by security).
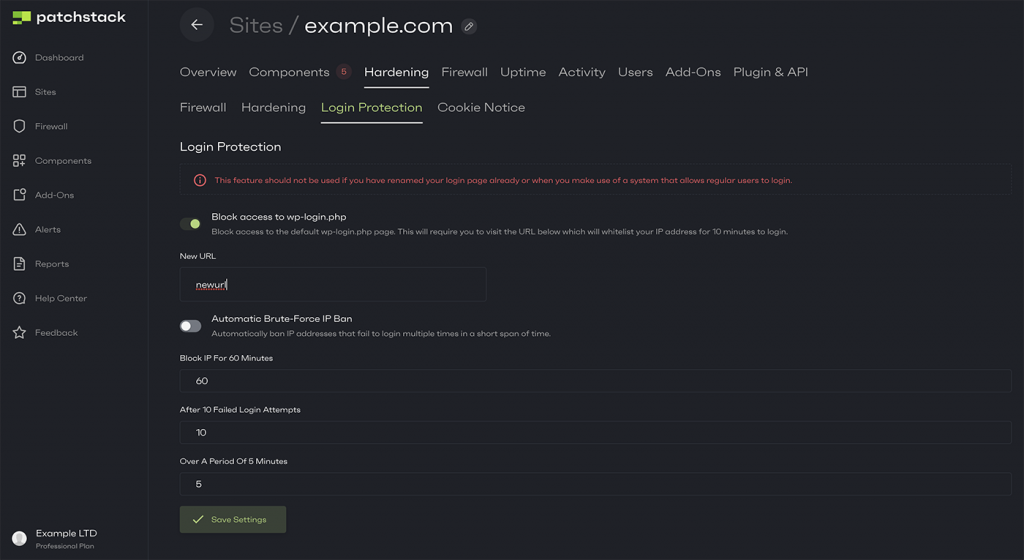
Block brute force attacks and attacking IPs
Brute-force attacks have become a nuisance for WordPress websites, and the only way to prevent them is to block the attacking IP addresses. However, it is almost impossible to block them manually as brute force attacks can come from a large number of IPs.
If you’re using Patchstack, you can block attacking IPs with only a few clicks.
In the Patchstack dashboard, you can manually enter IPs to block them. However, even if you don’t add all IPs manually, Patchstack will automatically block them on your behalf if it detects potential issues such as repeated attacks.
Read more about this functionality in our article, “How to Block IPs, Countries, & Regions for WordPress”.
Limit login attempts
There are many methods to secure the login page of your WordPress websites, but limiting the number of allowed login attempts is a sure way to deny access to automated bots. These bots are not intelligent and only try to guess passwords one at a time – which takes many attempts (at least, in most cases!).
If you are an advanced user, you can set firewall rules on your login page to block anyone who fails to log in after a certain number of attempts.
For example, you can block an IP address if it fails to log in after three attempts. However, you can implement this feature with only a few clicks using Patchstack. Read our post discussing how to limit login attempts on WordPress to learn more.
Add Recaptcha on the login page
One very effective way to block robots is to use a CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) service, a specialized test that distinguishes between humans and robots. A CAPTCHA can be implemented on the login page and any contact forms to block automated spam inputs.
Many different types of CAPTCHA services are available, but at Patchstack, we use Google’s offering - reCaptcha.
If you are using Patchstack, you can add reCaptcha to your site with only a few clicks, as described in our post, “How to Use CAPTCHAs on WordPress to Protect Your Site From Bots & Spammers”.
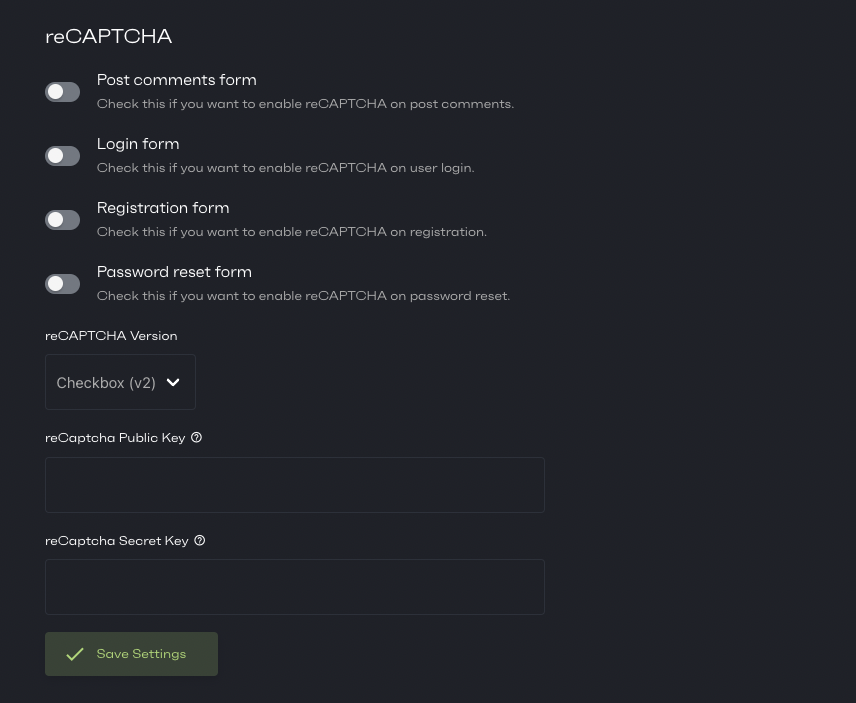
Use Two-Factor (2FA) authentication
Two-factor authentication adds another layer of verification to authenticate logins to your WordPress website. Adding Two-Factor Authentication (2FA) on your WordPress website will greatly reduce the chances of unauthorized access to your dashboard.
There are many ways to perform 2FA, such as sending a one-time code to your email address or mobile phone, or using an authenticator app with time-based OTPs.
If you are using Patchstack, you can easily enable 2FA on your site by navigating to “Hardening >Login Protection” and enabling the toggle next to 2FA. To learn more about this, check out our guide on multi-factor authentication in WordPress.
Use a web application firewall
A web application firewall is a software component that blocks malicious web requests on any website. We recommend adding a firewall to your WordPress website as it will protect it against many known attacks.
If you are using Packstack, you can use our advanced firewall and protection rules by enabling different protection modules on your website. Our vPatching functionality safeguards your WordPress website even if no patch is available for a security vulnerability.
Use SSL and migrate to HTTPS
Deploying SSL certificates and using the HTTPS protocol to access your website will encrypt any information shared between a client (visitor) and your server. This makes it harder to crack information and do man-in-the-middle attacks.
Using the HTTPS protocol will secure visitors if they access your website through unsecured networks, such as public WiFis that are not password protected.
Almost all hosting companies provide free SSL certificates by Let’s Encrypt, but if your hosting provider does not provide a free SSL certificate, you can refer to our guide to learn how to install SSL certificates on WordPress.
Disable file editing within the WordPress dashboard
The WordPress file editor is enabled by default, and allows anyone with admin rights to edit the theme files by navigating to Appearance > Editor. Although this is useful, it can also allow users to run unauthorized code on the server – which is a security risk.
You can easily avoid this security risk by disabling Editor access within the WordPress admin.
Add the following line of code in your WordPress wp-config.php file to disable this functionality:
// Disallow file edit
define( 'DISALLOW_FILE_EDIT', true );Disable PHP file execution
Some folders in the WordPress directory, specifically those under wp-content (where your themes, plugins, and images are uploaded), have very open permissions. If an attacker can upload a malicious PHP script on your website and execute it, then it can be a significant security risk.
You can’t entirely revoke permissions to write in these folders because doing that will stop you from uploading and installing plugins and themes. You can, however, stop PHP code from executing in these folders.
To prevent PHP from being executed, you must create .htaccess files and upload them to the folders where you want to prevent PHP files from being executed.
The uploads folder under the wp-content folder is where all the media files are uploaded, and hackers can often trick you into uploading a file that is named as though it is an image, but is actually a .php file containing malicious code.
Create a .htaccess file with the following code and upload it to wp-content/uploads to stop all .php files from executing in that particular folder:
<Files *.php>
deny from all
</Files>If you need more detailed instructions, check out our in-depth guide, which explains how to disable PHP execution in WordPress.
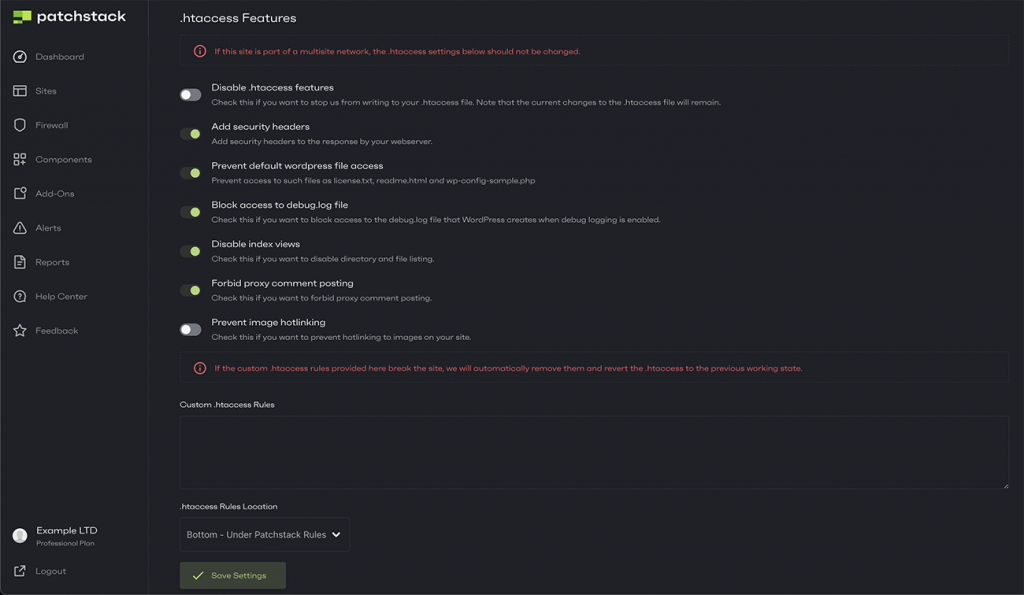
Disable directory indexing and browsing
If a server is improperly configured, WordPress subfolders may become accessible, allowing anyone on the Internet to access your server logs, backup files, etc.
To protect yourself, it is a good idea to entirely disable the chances of directories being viewed through browsers by adding the following line of code at the end of the .htaccess file in the root folder of your WordPress installation:
Options -IndexesYou can also disable file indexing by simply enabling the option “Disable index views” within Patchstack under Hardening > Firewall > .htaccess Rules, if you are using Patchstack to secure your WordPress website.
If you want to learn more about this topic, refer to our post on how to disable directory browsing in WordPress.
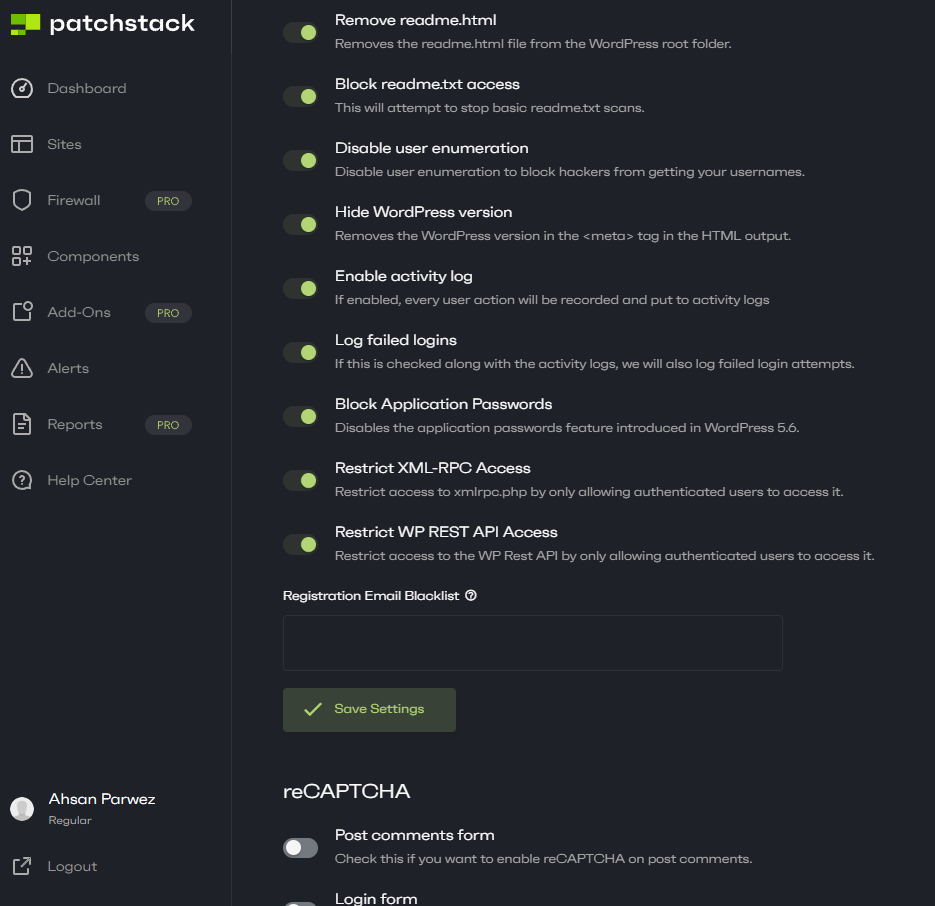
Disable XML-RPC in WordPress
XML-RPC is a WordPress functionality that allows you to interact with your WordPress website remotely. If you aren’t going to use this API, then we recommend turning it off by adding the following lines of code to your .htaccess file:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>If you are using Patchstack, you can also easily disable XML-RPC and WP-REST API on your WordPress website. This option is located under Hardening > Hardening Features.
Implement file integrity monitoring
File integrity monitoring is a tracking mechanism that allows you to monitor and track all the files on your server. By implementing advanced kernel-level filesystem tracking and sophisticated hash-based comparison techniques, you can detect unauthorized modifications across core WordPress directories, theme repositories, and plugin installations.
These monitoring mechanisms create an immutable baseline of system configuration, which can be used to identify changes, potential malware injections, or unauthorized file manipulations. Some hosting providers offer file integrity-monitoring servers with their hosting plan, but if your hosting provider does not offer this service, you can try third-party plugins such as Melapress File Monitor.
Implement activity logging
Activity logging lets you capture detailed logs of login attempts, content modifications, plugin installations, and user permission changes. Website administrators can get an invaluable forensic trail to detect threats and investigate incidents.
These granular logs provide immediate insights into potential security breaches and create a comprehensive historical record that can be crucial for understanding attack vectors and implementing proactive defense strategies.
For readers seeking a deeper dive into advanced activity logging techniques and best practices, we highly recommend checking out our previous in-depth post, which offers extensive insights and expert-level strategies for implementing robust WordPress security logging mechanisms.
Wrapping up
In this post, we have provided a comprehensive list of security tips and tricks that you can use to protect your website from a vast number of cyber attacks.
It is important to note that while implementing these techniques will significantly enhance your website’s security, we cannot guarantee that your website will never be hacked.
Most of the techniques mentioned above apply to any website on the Internet, but if you are using WordPress, you can implement all of these techniques with only a few clicks by installing Patchstack on your website.
FAQs related to WordPress security
Is WordPress secure?
WordPress is generally a secure platform, but like any website or software, it can be vulnerable to hacking attempts if it is not adequately secured. It is important to follow security best practices and use security plugins to protect your site and prevent security breaches.
Is WordPress easily hacked?
WordPress can be hacked if it is not adequately secured. However, if you follow security best practices, use the latest version of WordPress, and use a security plugin, you can significantly reduce the risk of hacking. Read our in-depth blog post “Is WordPress Secure?” to learn more about this topic.
What percentage of WordPress sites are hacked?
There's no definitive percentage of hacked WordPress sites. The estimated number fluctuates significantly based on factors such as website security practices (the use of strong passwords, regular updates, and security plugins), the WordPress version being used (older, unsupported versions are far more vulnerable), and the quality and security of installed plugins and themes.
While precise figures are unavailable, the trend in Patchstack’s state of WordPress security report shows a consistent and concerning rise in attacks targeting WordPress websites each year.
Do I need a WordPress security plugin?
While WordPress has built-in security features, a security plugin is highly recommended. A security plugin can provide additional protection against hacking attempts and help you detect and fix vulnerabilities in your site.
Does WordPress have built-in security?
WordPress has built-in security features such as password protection, user roles and permissions, and automatic software updates. However, it is still essential to follow the best security practices and use a security plugin to ensure the highest level of security.
An advanced security plugin is necessary to protect against advanced attacks, but you shouldn’t settle for plugins that only tweak minor settings. You should use a plugin focused on core WordPress security and login protection. Read our in-depth blog post, which discusses The Six Best WordPress Security Plugins, to know which is best for you.





