Are you worried that a password breach may have compromised your credentials?
No matter whether you answered ‘yes’ or ‘no’ to that question, you should still implement multi-factor authentication to your WordPress sites.
In this post, you’ll learn exactly what WordPress multi-factor authentication is, and why implementing it is a no-brainer. At the end of the article, you’ll also discover a new and emerging way to get rid of passwords altogether – while making your website even more secure.
Let’s dive right in with a simple question!
What is MFA?
Most websites on the internet ask you to set up a username and password when creating an account. These credentials are then used to verify your identity when you try to log in to your account.
However, there is a problem with this approach: a good and unique password is hard to memorize, and most people tend to recycle passwords, or worse, write them down.
In our previous post about brute force attacks, we explained different ways hackers can gain access to your passwords. One way to solve this problem is by presenting users with an additional challenge to authenticate their identity after they have verified their password. This is called multi-factor authentication (MFA).
Two-factor authentication (2FA) is a type of MFA which verifies the identity of the user twice – first via a password, and second via an additional chosen method.
Different types of MFA
SMS/Email
The most common way to implement 2FA is by sending a random string of text or numbers to a user on their mobile or email. Even if a malicious actor can get access to the password of your user account, they probably won’t have access to your email or mobile phone.
This introduces some additional security in the login process. However, this is not the most secure method of implementing MFA as users often use the same passwords on their email accounts, and determined hackers can still get access to your SMS by using a sim swap attack.
TOTP
This takes the concept of temporary passwords one step further by introducing Time-based OTP. This is a short sequence of numbers that changes every 30 seconds – even if you get access to a TOTP, it will be useless within a couple of minutes.
This sequence of numbers is generated according to a mathematical algorithm, and you can use a dedicated hardware device or a software utility, such as Authy, Google authenticator, Microsoft authenticator, etc. to generate tokens.
All TOTP devices follow an industry standard, and produce the same number at the same time – you can use any of them. As a bonus, if you use TOTP, you won’t have to wait for an SMS or email to be delivered as it is always available – even when you don’t need it.
But this is a double-edged sword. When setting up a TOTP, users are often presented with a QR code or a phrase. If this QR code or phrase gets compromised, the hacker will be able to generate authentication tokens.
Email Link
Although entering a random string of numbers introduces security, it also adds friction to the login process. When logging in, users will need to read numbers and type them in to authenticate themselves. It might only take a couple of seconds, but it can get annoying. And the worst part is, if the token expires, users will have to do the whole thing again.
To slightly improve this login flow, many websites send an email with a link to verify the identity. Now instead of typing in the numbers, you can quickly click on the link, which takes less than a second, and is a much simpler task to do for most people.
Hardware Tokens
You can get specialized devices that when plugged into a computer, will generate a sequence of numbers that will authenticate your login attempt. This is arguably the most secure way to implement 2FA.
You can buy Google Titian or Yubikey to secure your accounts. But you should keep in mind that if you lose your hardware token then you won’t be able to log in to your account either.
How to install multi-factor authentication to WordPress
Implementing two-factor authentication on your WordPress website will greatly improve your security. There are many different plugins available in the market that can help you implement MFA on your WordPress website:
- Two Factor Authentication
- WP 2FA – Two-factor authentication WordPress plugin
- miniOrange’s Google Authenticator
Most of these applications work similarly, so instead of providing step-by-step instructions for each, we will provide a general overview of the setup process and you can follow to implement WordPress multi-factor authentication on your website.
Step 1: Install the MFA Plugin
The first step is to go to your WordPress dashboard and install the MFA plugin that you want to use. Many security plugins come bundled with the MFA functionality. If you have one of those installed, then you can just use that instead of installing another plugin.
Step 2: Configure the MFA Device
The next step is to configure the MFA functionality on your website with the device that you want to use for authentication. In this example, we will use TOTP-based authentication with the 1password password manager to store our tokens. If you’re using Google Authenticator or a similar mobile application, then the process is much the same.
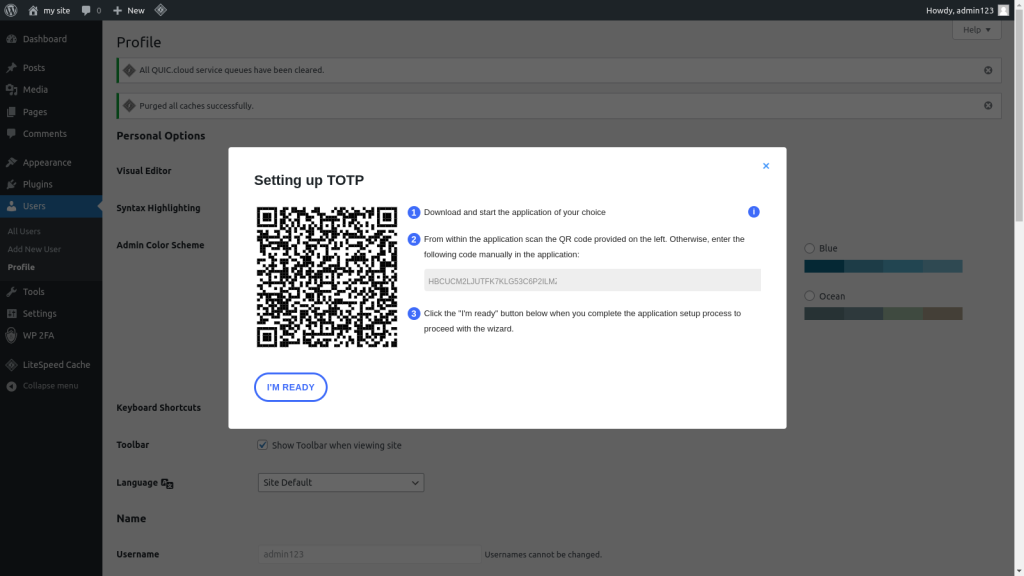
When you enable the 2FA functionality, you will be presented with a QR code and a secret text. You can either type the secret text or quickly scan the QR code with your smartphone to store it. If you’re using a password manager, you can edit the login details to add a field for a One time password, and then paste the given text.
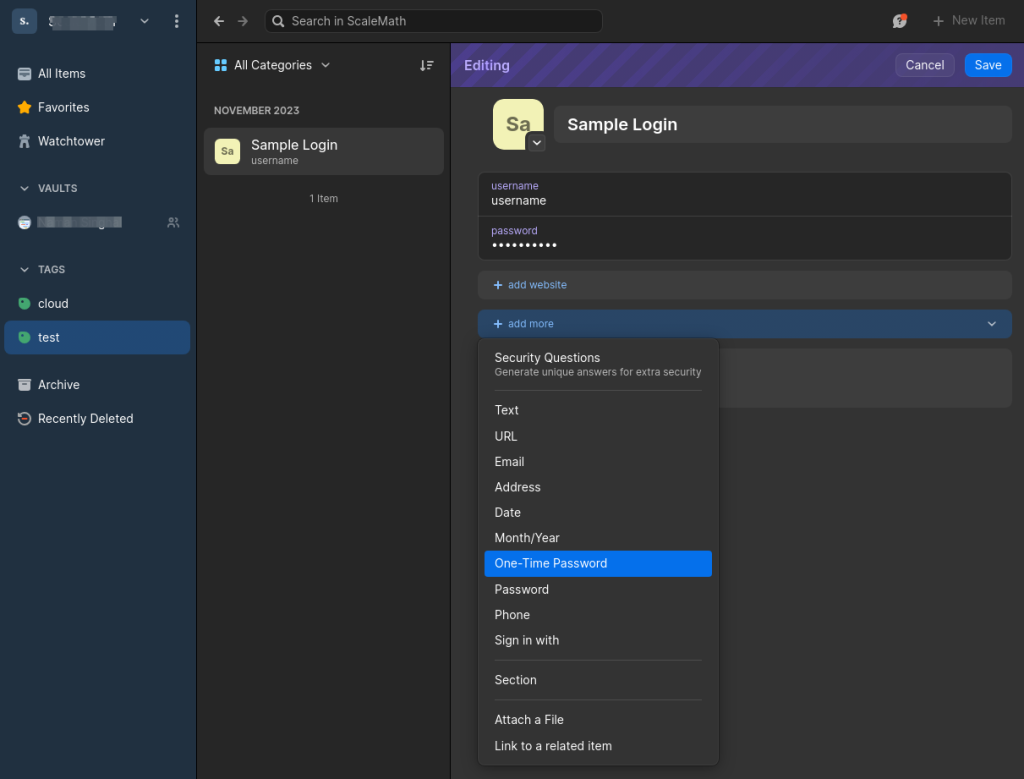
After you have completed the above steps, your TOTP device will start showing authentication tokens immediately. To finish the confirmation process, you’ll need to enter this token in your WordPress dashboard. Once you submit the correct token, the MFA functionality will be enabled on your website.
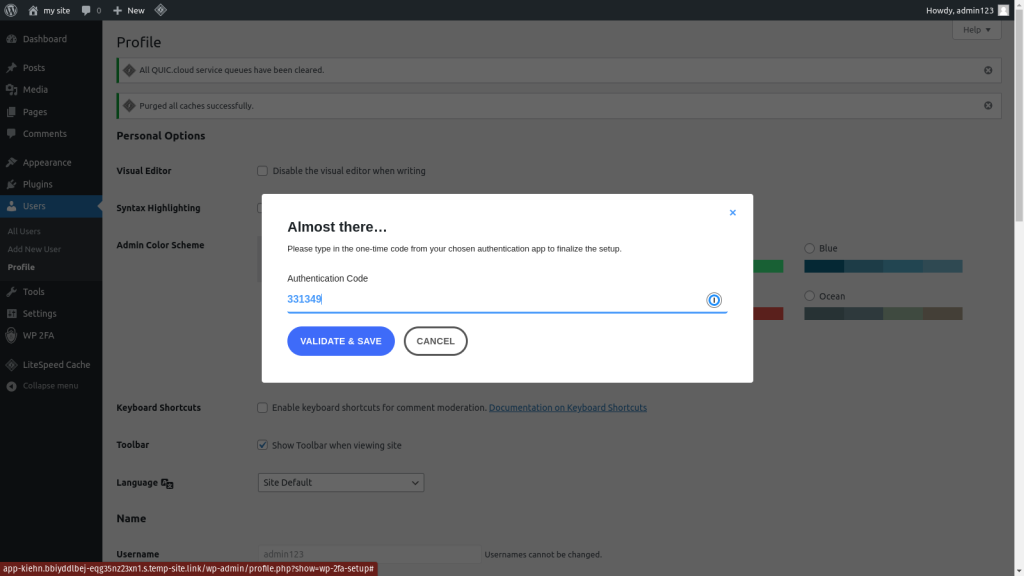
Step 3: Test the Login Functionality
Open a different browser or an incognito window and try to log in to your WordPress dashboard. Once you enter your login credentials, you will be presented with a field to enter your 2FA token. Enter the token displayed on your authentication device to log in securely.
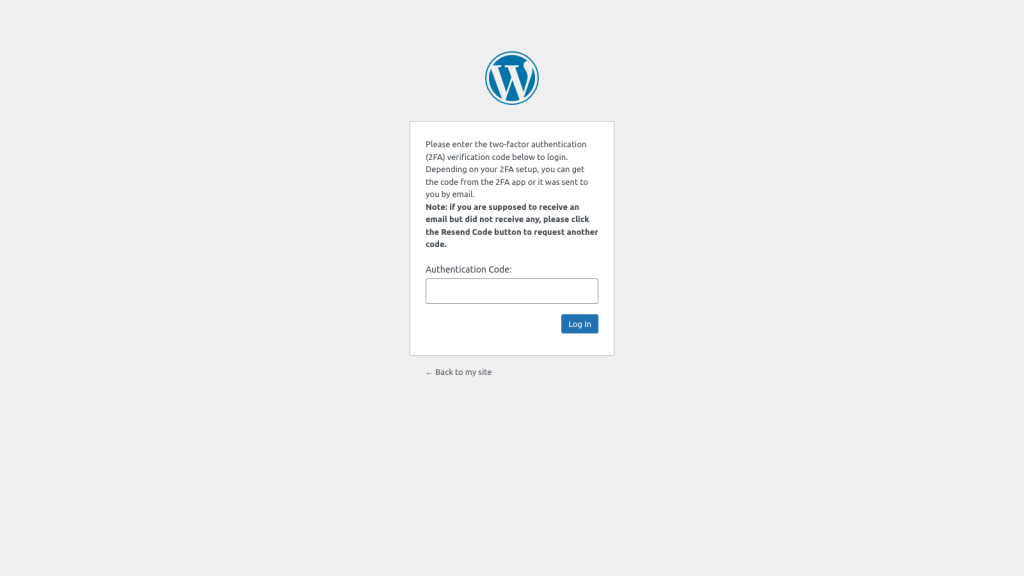
FIDO Passkeys: A Better Alternative to MFA
Although using various types of hardware and software-based security tokens increases the security of your website, it also makes the login process more difficult. When users use 2FA, they will have to secure a token generator in addition to all their existing passwords.
This complicates the login process, and many users intentionally don’t use these features because it slows them down. A better alternative would be to remove the passwords altogether and authenticate users using something else.
This is where Passkeys come in – an alternative way to authenticate users without the need for passwords.
This technology uses functions such as facial recognition and fingerprint verification that are built-in to many devices, instead of using passwords. This is much more secure as users do not have to re-use passwords, and the login functionality becomes immune to phishing attacks.
If you’re looking for a better alternative to 2FA, then you should check out Solid Security. It is a security suite for WordPress that uses the newer login functionality with the passkeys to make your website more secure. Moreover, it uses Patchstack under the hood to notify you about any vulnerabilities in your WordPress website.
Final Thoughts about multi-factor authentication to WordPress
It’s clear that using WordPress multi-factor authentication will make your WP site much more secure and resistant to various cyber-attacks. If possible, we encourage you to use passkeys to streamline your login process and deter attackers. If you want to learn more about passkeys, we recommend you check out Passwordless Authentication by Google and Auth0’s Take on Passkeys.
If you want to further improve your WordPress security, you can continue learning about how to limit login attempts on WordPress.
If you are serious about your WordPress security, you should check out Patchstack, a vulnerability management tool for WordPress. It is built by a talented team of expert security professionals who track and monitor security incidents in all things WordPress.
The best part is that Patchstack users get a 48-hour early warning to update their websites in the event of a vulnerability, even on the FREE plan. Start using Patchstack today and make sure your website is secured.





