One company tells you that you need an antivirus. Another says you’re good with their all-in-one plugin. Your hosting provider keeps going on about server-side things they’re doing. And, at the end of the day, you’re still left with a glaring question:
What does it actually take to sleep at night, knowing you’ve done everything to protect your WordPress website(s)?
The answer isn’t as complex as you might think. To help illustrate the different layers with entry points hackers use to attack sites, we’ll use the Swiss Cheese model or - as we like to call it - the security layer cake.
Get your fork! It’s time to understand the critical areas you need to protect, and just how you can do it.
The security layer cake explained
Don’t think of security as a flat surface. Instead, think of it as a layer cake comprised of the key layers: network (the first point where external traffic “sees” your site), server (the point where external traffic “touches” your site), and application layer (where the external traffic interacts with your site).
Each layer has its weaknesses, which is why you need specific solutions to mitigate them. If you have an ear infection (or a hack), a generalized antibiotic (or an all-in-one security tool) might help with some symptoms.
However, it’s much better to get an antibiotic specialized in treating ear infections, so the exact symptoms are nipped in the bud.
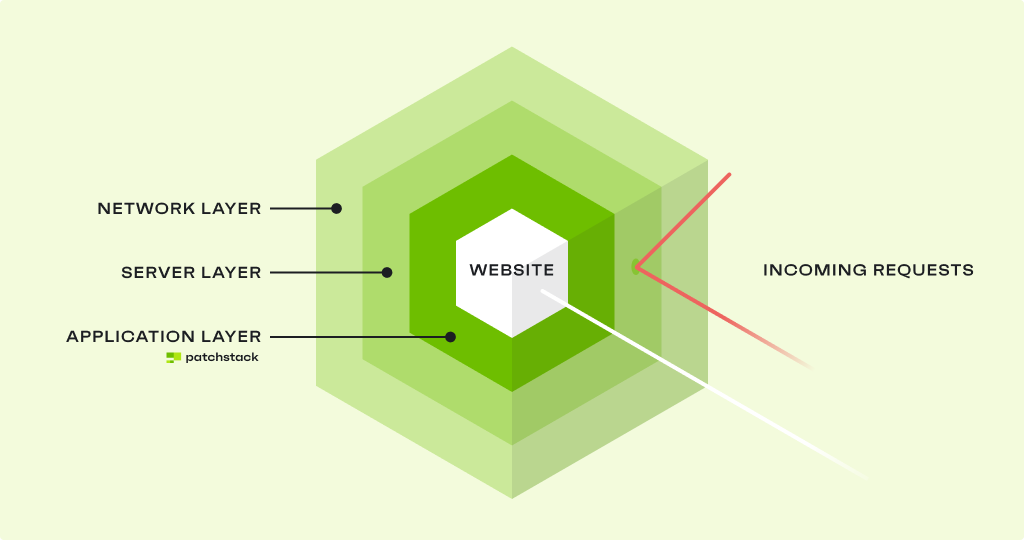
First stop: Network layer security (and its role in protecting your WordPress site)
The network layer is the first point of contact between other IP addresses and your site. It’s where all this incoming traffic is filtered to make sure it’s legitimate.
Typically, this is where bots trying to launch DDoS attacks are stopped in their tracks, and where you can implement geoblocking or get rid of IP addresses known to be malicious.
At this point, the main tool you need to protect your site’s network layer is a traditional firewall like Cloudflare.
What is the role of firewalls in WordPress security?
Traditional firewalls will help you:
- Mitigate DDoS (Distributed Denial of Service) attacks
- Filter out bot traffic
- Set up simple IP and page-based restrictions
- Force SSL/TLS encryption to ensure all traffic is passed through the secure HTTPS protocols
Are firewalls enough to protect your WordPress site?
Think of this traditional firewall as a wide net: it wants to catch as many threats as possible. The issue is, if it’s too close-knit, it generates a lot of false positives.
Instead, it optimizes for the lowest level of false positives, meaning that the true detection rates for each threat are reduced.
This means that firewalls are a must, but they’re not enough to protect your WordPress site. They should be a part of your stack that blocks exploits against the network layer, but you’ll still need specific solutions for your application-level security.
Second stop: Server layer security for WordPress
After the network layer “vets” the traffic (AKA: visitors), they’ll get into contact with your servers, which serve the site to them. This is your WordPress website’s infrastructure and, just like any infrastructure, it needs robust protection.
What does server-layer security include?
Server layer security for WordPress typically includes the following:
- Software and OS update management
- Server isolation
- Regular backups
- File integrity monitoring and server-side malware scanning
Your hosting provider’s duties
Your server’s operating system is the very foundation of your site. Typically, this is something managed by your managed hosting provider, and it should include regular updates to your software and operating system (OS).
In the second step, there are actual protective measures like server isolation. Your hosting provider should be isolating servers from one another, so if there is a breach on one server, it doesn’t affect the rest of them.
This is also why you should avoid shared hosting. If one website is affected by an attack, it could jeopardize your website, too.
What can you do to strengthen your server layer security for WordPress?
First, perform regular backups. If there is an attack, having a backup will help the malware cleanup team restore the site from the latest saved version, saving you weeks (if not months) of recreating content.
You should do file integrity monitoring at the server level. This means you’ll be checking all the files in your WordPress and website installations to ensure there have been no unauthorized changes to your code.
On the other hand, you should also do malware scanning at the server level. Unlike file integrity scanning (which checks the versions of your files against baselines), malware scanning looks for known malware signatures and patterns. If it finds them, it will quarantine and block them from affecting the rest of your website.
Wait, I can’t do malware scanning with a plugin?
We don’t recommend using plugins as your primary malware scanning method. They’re useful in certain cases, but if there is an attack and the hacker gains access to your WordPress website, they could tamper with the plugin.
Server-side malware scanning is much safer (and more robust).
Ultimately, the best way to strengthen your server-level security is to choose a trusted managed WordPress hosting provider (if you’re not doing it on your own) like Kinsta, Pagely, or WP Engine.
The best providers should be clear on the measures they implement to provide server-level security, as well as offer regular backups, file integrity monitoring, and malware scanning.
Third stop: Application layer security for WordPress
Networks and servers are present on every website. However, application layer security specializes in WordPress security, i.e., all the apps, themes, and plugins you have in your installation.
Wait, isn’t WordPress secure?
WordPress is secure – out of the box. But with the high level of customization come the risks: whenever you install a new plugin, you’re not just trusting yourself anymore.
Now, you’re also trusting that plugin developer (and their team).
Since WordPress is widely used, it’s a popular target for attacks. Hackers don’t even have to check the sites: they can mass-launch attacks against all the sites using a plugin with a specific vulnerability.
Ultimately, the application layer in WordPress is the #1 spot where all the preventable hacking incidents happen.

What’s the role of vulnerabilities in WordPress security?
Unlike brute-force attacks where an attacker is trying to force an action on the site, vulnerabilities are logic flaws in the plugin or theme code that make for a sneaky attack.
The attacker uses those logic flaws to “convince” your site that their request is legitimate, essentially fooling it into giving them access.
This is what makes vulnerabilities so hard to prevent at any other layer than the application, and why we need specialized tools that constantly monitor for vulnerabilities.
At the same time, 97% of all security bugs found in 2024 were plugin vulnerabilities.
It’s a widespread issue, and the size or reputation of your site doesn’t matter. All that matters is having the plugin with the right vulnerability installed.
How to protect your application layer in WordPress
First, select only the plugins you need. Typically, our WordPress developer clients have one stack and stick to it. The plugin developers should also be reputable, known for communicating promptly, and have a history of regular security updates.
Once you’ve installed the plugins and themes, keep them regularly updated.
We know, WordPress doesn’t check for compatibility with plugin updates so there’s always a chance of breakage. Still, you can test them in a staging environment before applying them to the live site – but do not wait to apply a critical security update!
Finally, or firstly, use a vulnerability management tool to reduce the time from the moment the vulnerability is discovered to the moment you’re able to apply an update.
It takes hackers less than a few hours to launch an attack. If you don’t apply the update the moment the plugin developer issues it and you’re not using a mitigation tool, you’re still at risk.
WordPress vulnerability mitigation
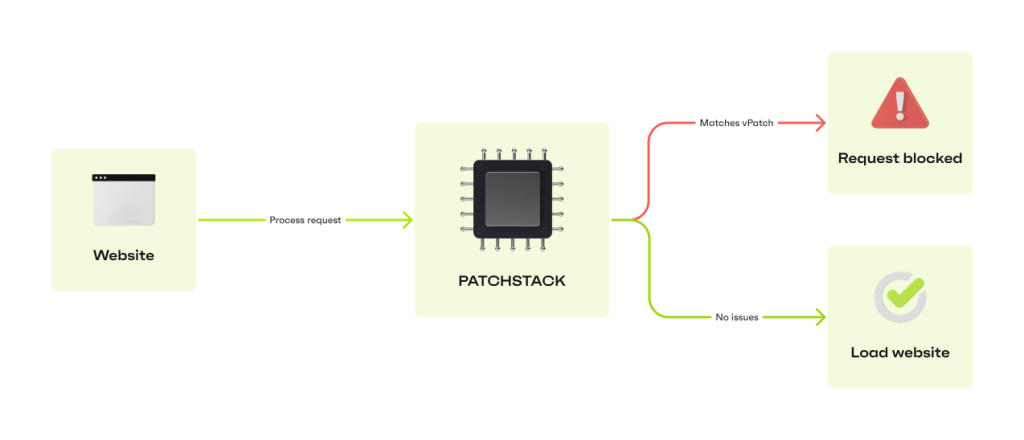
Patchstack’s vulnerability monitoring takes note of the plugins you have installed.
Once there is a vulnerability added to our database, we’ll send you a notification so you know to update the plugin.
Our team of security researchers and the community of ethical hackers is constantly on the lookout, so you’ll get the critical information with a 48-hour early warning!
If you want to lighten the update management load, get real-time protection.
Patchstack will automatically block attacks against the vulnerabilities with highly targeted mitigation rules (virtual patching) that don’t affect your site performance.
That way, you have time to test and apply the plugin update in peace, knowing you’re protected!
Final stop: The human factor
You could do everything right and still get hacked if Steve decides to make his password “pizza123.”
User permission security in WordPress
In your final layer of WordPress protection, you should use the principle of least privilege: don’t give users access to any functionality that they don’t absolutely require.
For example, someone writing for your blog doesn’t need Admin access - the Editor role is more than enough.
If you’re a developer creating WordPress websites for your clients, we know it feels wrong not to give the site owner Admin access. However, if they’re on your maintenance plan, it’s much safer for them not to be able to make significant changes.
Plus, if they’re not Admins, that’s one less account you have to worry about in the event of exploits.
Monitor your WordPress activity
If you collaborate with others on the same WordPress site(s), set up an activity log to monitor how specific users have changed the site. This helps you track down the changes, as well as spot any strange behavior that might alert you your site has been compromised.
For example, in Patchstack, you can review the latest changes in the Activity Log for signs of suspicious activity.
2FA or MFA
Enforce Two-Factor or Multi-Factor Authentication for everyone with user roles on your website.
Many vulnerabilities that lead to hacks require specific WordPress roles, so reduce the risk by asking your team to verify their login attempts.
reCAPTCHA and login protection
Use reCAPTCHA verification to prevent bot traffic in your comments, log-in pages, and contact forms.
Plus, move your login page from the default /wp-login. It’s most commonly used in attacks and while you won’t be 100% safe even if you move it, it’s best to reduce the risk as much as possible.
Introducing the newest WordPress Security 101 graduate: You!
Congratulations! Now you know exactly what it takes to make your WordPress site secure.
Changing the mindset from “all-in-one” to “layer cake” already goes a long way, but we also hope that our practical tips helped you know which steps to take next.
For your homework, take a look at your current security stack.
Are you missing any solutions or implementations from one of the layers we mentioned? Perhaps your hosting provider doesn’t offer regular backups, in which case we’d recommend integrating an external tool.
Or, if you haven’t thought about plugin vulnerabilities just yet, sign up for Patchstack now and get the fastest vulnerability detection and protection in WordPress!





