As an increasing number of businesses shift to online, the number of cyber attacks is also increasing proportionally.
Protecting a website from cyber attacks can be difficult – but it doesn’t have to be.
For most website owners, finding a web application firewall that works with their server stack and website is an arduous task that requires extensive research.
If that sounds like you, don't worry!
In this article, we will share some of the easiest ways to protect your website from a wide range of cyber-attacks using a powerful cybersecurity tool: web application firewalls.
By the end of this article, you will have a firm understanding of different types of web application firewalls and which one is right for you.
But first, let's understand what a managed web application firewall is.
What is a managed web application firewall?
Before discussing managed firewalls, let’s quickly understand what a firewall is. In simple terms, a firewall is software or hardware that can protect your website from attackers. These are divided broadly into two categories – managed and self-managed.
A managed web application firewall is a firewall that is managed and updated by someone else. You don’t have to research and update the firewall rules according to new vulnerabilities. The research and updates are made by the company that provided you with the firewall.
And similarly, as the name suggests, a self-managed firewall requires you to do all this yourself.
A user-friendly managed WAF can do several things to protect your website. Here are some benefits:
- A managed WAF keeps up with the latest software releases and bug fixes. WordPress plugin and theme vulnerabilities are the number one reason websites get hacked. For example, Patchstack’s managed web application firewall receives daily updates to prevent plugin and theme vulnerabilities.
- A managed service is streamlined to your needs. Apart from being protected from OWASP’s top 10 vulnerabilities, you can also write your own rules. If you notice something suspicious about your website’s traffic, you can try to correct it with custom rules.
- Round-the-clock monitoring means you will be alerted whenever there’s something critical to investigate. With Patchstack, for example, you can get alerts via Slack or email.
- You can adopt modern security practices more efficiently, including two-factor authentication and ReCaptcha. Besides, a managed WAF is aware of compliance requirements so that you don’t break the rules without being aware of them – for example, GDPR cookie and privacy policy.
- Regular security scans and reports will give you a better understanding of web security. Even if you start as an amateur web designer, you can gain actionable insights into cybersecurity.
A managed firewall allows you to avoid hiring a cybersecurity expert to protect and update your website. This is particularly useful for small and medium businesses that don’t have the budget to hire a full-time security specialist.
Why do you need a managed web application firewall?
You need to do a lot of work to keep your website safe. You can’t just install a web application firewall and forget about it. You need to have round-the-clock monitoring and management.

Why? Hackers constantly find new and improved ways to target websites, often through content management systems like WordPress and plugins. This section will discuss some of the most common cyber attacks and web security risks.
Top 10 web application security risks
Suppose you’re looking to learn about web application firewalls and website security and don’t know what to look for. In that case, the Open Web Application Security Project (OWASP) is an excellent place to start your research. OWASP is an online community that has become a trusted source of content on application security.
Over the years, the OWASP “Top 10” guide has become a standard reference material for cybersecurity experts to know what your web application security needs to protect you from. Here are the top ten vulnerabilities according to OWASP:
- Injection: This flaw comes from how you accept user input. If the user inputs code (or partly code), like HTML or SQL, and your web server runs it without realizing it’s code, you can give the user unintended access to your website.
- Broken authentication: Your website and software (plugins, themes) must authenticate each user's access. If this is not implemented correctly, a hacker can use broken authentication to gain access while pretending to be a genuine user.
- Sensitive data exposure: This is pretty straightforward and a development flaw. Web applications and APIs sometimes fail to protect sensitive data, such as financial information. If hackers know of a popular application that is vulnerable, such as a WordPress plugin, they could steal or modify weakly protected data, which can lead to credit card fraud or identity theft.
- XML External Entities (XXE): This form of injection uses XML. A hacker adds or modifies the XML to interfere with an application's processes. It’s about access again, allowing the attacker to see files on the application server. It can also be used to interact with back-end systems that the application can access.
- Broken access control: Even authenticated users have restricted access. However, if access control is broken and not enforced properly, hackers can use such flaws to do damage. They can gain unauthorized rights or mess around with data, steal details of user accounts, modify user data, or change access rights.
- Security misconfiguration: OWASP says this is the most common issue. Applications come with default configurations, which could be insecure. Or misconfigured detailed error messages give attackers the information needed to compromise your website. Your web application firewall can run scans and audits periodically to detect misconfigurations or missing security patches.
- Cross-site scripting (XSS) differs from injections because it targets users, not your website’s applications. A vulnerability in a web application allows hackers to run scripts on the victim’s browser, and the user is then at risk of being redirected to malicious sites and having their data stolen.
- Insecure deserialization: Once again, it’s about giving hackers a way to run malicious code on your website by editing data run by your web server. You can use a WAF to detect such attempts to gain back-door access.
- Using components with known vulnerabilities: All web application components, such as libraries, have the same privileges as the application. So, even if one application component is vulnerable, it can lead to devastating attacks. Always uninstall plugins, themes, and other applications known to have vulnerabilities or are no longer actively developed.
- Insufficient logging and monitoring: OWASP reports that the time to detect a security breach is over 200 days and is often found by external researchers. But if you’re diligent in logging and monitoring activity on your website, you might be able to notice an attack before it becomes a problem. A managed WAF often provides regular and automated security reports. You should take the time to go through it.
What’s more troubling is that hackers target small businesses just as much as larger companies. Nearly half (47%) of the small firms they surveyed had suffered a cyberattack, and there has been a sharp rise in ransom demands.
You need both Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) capabilities in your WAF. An IDS analyzes traffic and alerts you when it detects an attempted cyberattack. An IPS analyzes traffic coming to your server but has the right to stop data from being delivered if it detects an attack.
Different types of managed WAFs
In the following sections, we will explain different types of managed web application firewalls to help you understand which one is right for you.
What is a cloud-based firewall?
One of the easiest ways to understand a cloud-based firewall is to imagine a security guard who collects all your deliveries for you. After collecting the deliveries, the guard inspects them and forwards them to you. This allows you to receive deliveries without needing to interact with strangers.
Similarly, a cloud-based WAF analyzes all HTTP traffic to a web server and filters out any traffic it thinks is malicious. When a visitor tries to access your website, the connection is first made with the firewall’s server, which then accepts or denies connection requests based on predefined rules.
In our previous post, we explained how to protect against DDoS attacks and provided an in-depth analysis of some popular cloud firewall offerings from major industry players.
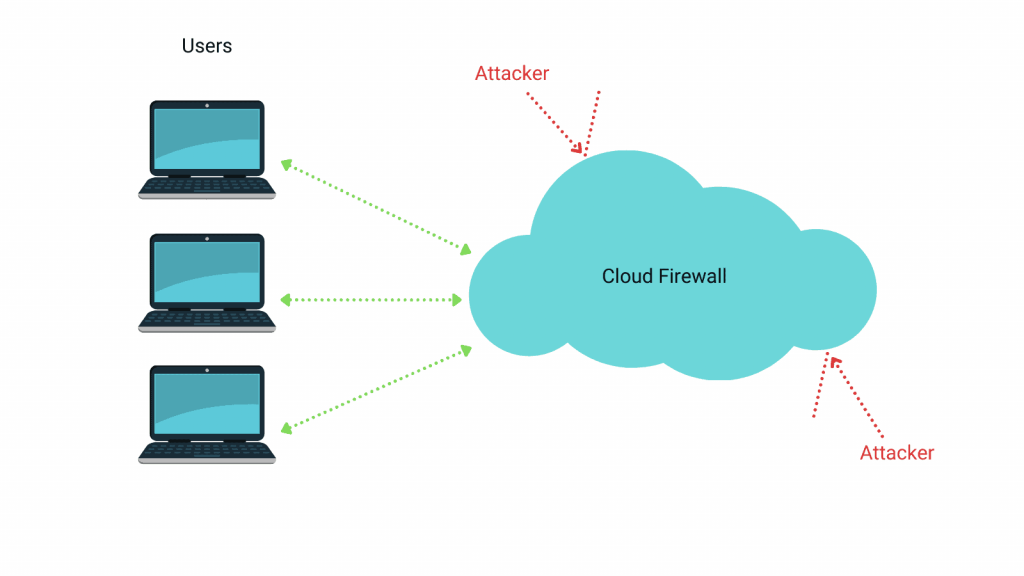
How does a cloud-based firewall work?
A Web Application Firewall (WAF) uses sophisticated techniques to analyze traffic, detect threats, and apply security rules. Here's a breakdown of its core functionality:
- Traffic Analysis: All firewalls inspect all incoming and outgoing traffic and examine requests, headers, body content, and URL parameters.
- Rule Application: Most firewalls allow you to configure manual rules that automatically block or allow explicitly permitted traffic. If such rules have been defined, incoming traffic is checked against them.
- Threat Detection: During inspection, firewalls use different techniques to identify attackers. For example, they use:
- Signature-based detection to identify known attack patterns
- Anomaly-based detection to spot deviations from normal traffic patterns
- Behavioral analysis to identify suspicious user activities
- Threat Mitigation: If the firewall detects a threat, it blocks or challenges suspicious requests based on rule evaluations. It can also implement rate limiting to prevent brute force attacks and DDoS attempts. Additionally, you can send custom responses to blocked requests (e.g., redirects and custom error pages).
- Logging and Reporting: After assessing the request, the firewall records detailed information about all traffic and security events. This can generate real-time alerts for security personnel or compose comprehensive reports for analysis and compliance.
What is an endpoint web application firewall?
If the cloud-based firewall is the security guard for your building, then an endpoint web application firewall can be considered a personal bodyguard. While a security guard can block many threats, they might also dismiss legitimate requests because they don’t understand your use case. In this case, you might hire a personal bodyguard who would know the ins and outs of your business.
Similarly, an endpoint WAF is a firewall that runs within an application. It has access to all the software, plugins, and themes you have installed on your server. It differentiates between users based on their permission level, making it more flexible and adaptable than other options.
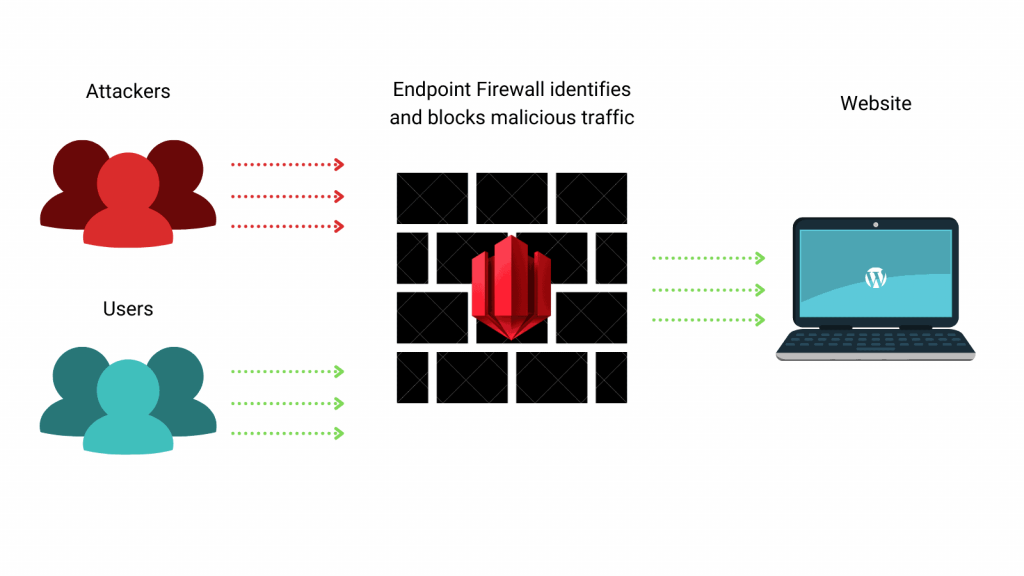
Advantages of an endpoint WAF
Although cloud-based firewalls and endpoint firewalls seem similar, they have a few key distinctions:
- Endpoint WAF tends to have fewer false positives, meaning it’s less likely to identify real traffic as an attack.
- Endpoint WAFs know your installed software and are more prepared to block targeted attacks.
- Your website will not be affected if an endpoint WAF’s server is down. While it won’t update new rules, it will continue functioning within your website.
However, you should also note that an endpoint WAF has some disadvantages. Since it’s installed within your website, it uses the same resources as your website. This could be a problem if your traffic grows exponentially and your server is unprepared for it. For this reason, endpoint firewalls are unsuitable for protecting against DDoS attacks.
Cloud-based WAF vs an endpoint WAF
In our Quick-Start Guide to Protecting Your WordPress Website, we explained that web security is fundamentally about creating multiple layers of protection, each addressing different aspects of potential threats. This layered approach provides a more comprehensive and robust defense against diverse cyber threats.
Implementing cloud-based and endpoint Web Application Firewalls (WAFs) creates a far more effective security strategy than relying on either solution alone.
Cloud-based WAFs excel at managing and mitigating large-scale threats at the network level, which can overwhelm servers and degrade performance. On the other hand, endpoint WAFs operate closer to the application itself, which makes them better equipped to identify and stop more sophisticated hacking attempts that might slip past network-level defenses.
We recommend implementing this layered approach using a combination of Cloudflare's free tier service as a cloud-based WAF and Patchstack as an endpoint WAF.
- Cloudflare's free offering provides robust DDoS protection and basic bot management, serving as a solid first line of defense.
- Patchstack complements this by offering deeper, application-level security, which includes protection against WordPress-specific vulnerabilities and zero-day threats.
Limitations of managed WAFs
While managed WAFs offer numerous benefits, they also have their limitations:
- One significant drawback of managed WAFs is the potential for false positives, which can occur when legitimate traffic is incorrectly identified as malicious. This can lead to unnecessary blocking of valid requests, potentially impacting user experience and business operations.
- Performance impact is another consideration when implementing a managed WAF. As all traffic must pass through the WAF for inspection, this additional layer can introduce latency, especially for high-traffic websites or applications with complex structures.
- Data privacy and regulatory compliance can also pose challenges when using a managed WAF. Since all traffic, including potentially sensitive data, passes through the WAF provider's infrastructure, organizations must ensure that this aligns with their data handling policies and relevant regulations.
This can be particularly challenging for companies operating in highly regulated industries or regions with strict data localization requirements. The lack of complete control over where and how data is processed may conflict with certain compliance standards or internal security policies. - Lastly, relying on a third-party service for critical security functions can be a double-edged sword. While it provides access to expertise and resources, it also introduces a degree of vendor lock-in and potential single points of failure. If the managed WAF provider experiences downtime or faces a security breach, it could have far-reaching consequences for all their clients.
Is a web application firewall all you need?
Implementing a Web Application Firewall (WAF) is undoubtedly a significant step in the right direction. Still, it's essential to understand that it's just one piece of a much larger security puzzle.
While a WAF provides robust protection against many common threats, proper website security requires a diverse approach that addresses vulnerabilities at various levels. This includes technological solutions, user education, regular maintenance practices, and ongoing updates.
We strongly recommend reading our post, "The Complete Guide To WordPress Security", to better understand the numerous elements contributing to website security.
Additionally, the Patchstack Academy provides a wealth of educational materials, tutorials, and up-to-date information on emerging threats and security trends.
Wrapping up
Throughout this post, we've explored the various types of WAFs, their functionalities, and the importance of implementing a multi-layered security approach. We hope this information has provided valuable insights into the world of web security and equipped you with the knowledge to make informed decisions about protecting your digital assets.
As we've emphasized, while WAFs are essential, they are most effective when part of a comprehensive security strategy. However, not all WAFs are created equal, especially when protecting WordPress sites.
This is where Patchstack stands out as the ultimate firewall option for WordPress.
What sets Patchstack apart is its unique ability to protect against vulnerabilities that developers still need to fix. This proactive approach to security means that your WordPress site is shielded from known threats, zero-day vulnerabilities, and emerging attacks.
Patchstack's advanced threat intelligence and continuous monitoring capabilities ensure that your site remains protected against the latest threats, often before they become widely known. This level of protection is invaluable, especially when new vulnerabilities can be exploited within hours of discovery.
Don't wait for a security breach to occur – Sign up for Patchstack today!





