These days, spinning up a new WordPress website is quick and easy, but securing it is not so straightforward.
In this post, we will cover some of the most critical things that you need to consider when setting up security for your WordPress website.
This guide is divided into three sections:
- WordPress settings
- SSH configuration
- HTTP Headers
Each section corresponds to a different component that can potentially be abused in order to hack your website.
WordPress Settings (website level)
You can configure a number of settings in the WordPress installation itself to enhance security.
Let’s take a look at these settings one by one.
1. Block XML-RPC
XML-RPC is a feature in WordPress that enables executing code remotely and transmitting data over the internet. It was a useful feature when it was first introduced, but these days it has become obsolete.
It is best to turn this feature off if you’re not using it, as it can be exploited for brute-force attacks. Read our in-depth post on how to disable XML-RPC to understand its security implications.
2. Block Access to Directories
Directory listing (also known as directory browsing or indexing) is a web server feature that displays the contents of directories when no default index file is present.
While this functionality can be necessary for certain WordPress plugins and themes to operate correctly, exposing directory contents to public access can provide attackers with valuable information about your site's structure and potentially sensitive files.
To disable directory browsing, the configuration depends on your web server:
For Apache and LiteSpeed servers (approximately 45% of websites), you can prevent directory listing by adding Options -Indexes to your .htaccess file. This simple and effective method works across most Apache-based configurations.
For Nginx servers (approximately 35% of websites), you need to modify your server block configuration. You can disable directory listing by removing the autoindex on instruction if present, or explicitly setting autoindex off within the relevant location block:
location / {
autoindex off;
}
Regardless of your web server choice, disabling directory browsing is a recommended security practice that should be implemented alongside other security measures. This helps prevent unauthorized users from discovering potentially sensitive information about your WordPress installation's file structure and contents.
3. Disable PHP Execution
Many sites allow users to upload content to their sites. However, this can be a security risk as an attacker can upload a PHP script with malicious code that can infect your server.
Disabling PHP execution in certain WordPress directories can be an effective way to prevent malicious code execution. Read our tutorial on disabling PHP execution in certain directories to enhance the security of your web server.
4. Follow the Principle of Least Privilege
Implementing proper user access control is crucial for WordPress security, especially since many vulnerability exploits require specific user privileges (like administrator access) to be successfully executed. Creating individual user accounts with carefully restricted permissions, rather than sharing admin credentials, not only provides better accountability but also significantly reduces the potential impact of compromised accounts.
Follow the principle of least privilege: each user should only have access to the minimum capabilities required for their specific role. For example, content editors might only need access to create and edit posts, while developers might require additional plugin and theme management permissions.
This segmentation is particularly important because many WordPress vulnerabilities can only be exploited when an attacker gains access to an account with elevated privileges, such as administrator rights.
Regular audits of user permissions and roles should be conducted to ensure that access levels remain appropriate over time. Remove or downgrade unnecessary administrator accounts, revoke access for inactive users, and maintain a clear record of who has what level of access.
Additionally, consider implementing temporary elevated privileges when needed rather than permanently granting high-level access.
Additionally, files and directories in WordPress installations require careful management to maintain security without breaking functionality. While it might be tempting to set overly permissive permissions (like 777) to quickly resolve access issues, this practice significantly increases security risks by allowing any process on the server to read, write, or execute files.
Instead, you should implement the principle of least privilege for filesystem permissions: files should typically be set to 644 (owner can read/write, group and others can only read) and directories to 755 (owner can read/write/execute, group and others can only read/execute), with more restrictive permissions where possible. Critical files such as wp-config.php should be even more tightly controlled, ideally set to 600 or 640.
5. Use Strong Passwords or Passkeys
Here is a fun question: how long do you think it takes for a hacker to break simple passwords? One day? One hour? Think again! Hackers can use modern hacking tools and advanced algorithms to try out millions of passwords every second. According to Password Monster, a simple password can be cracked in less than a second.
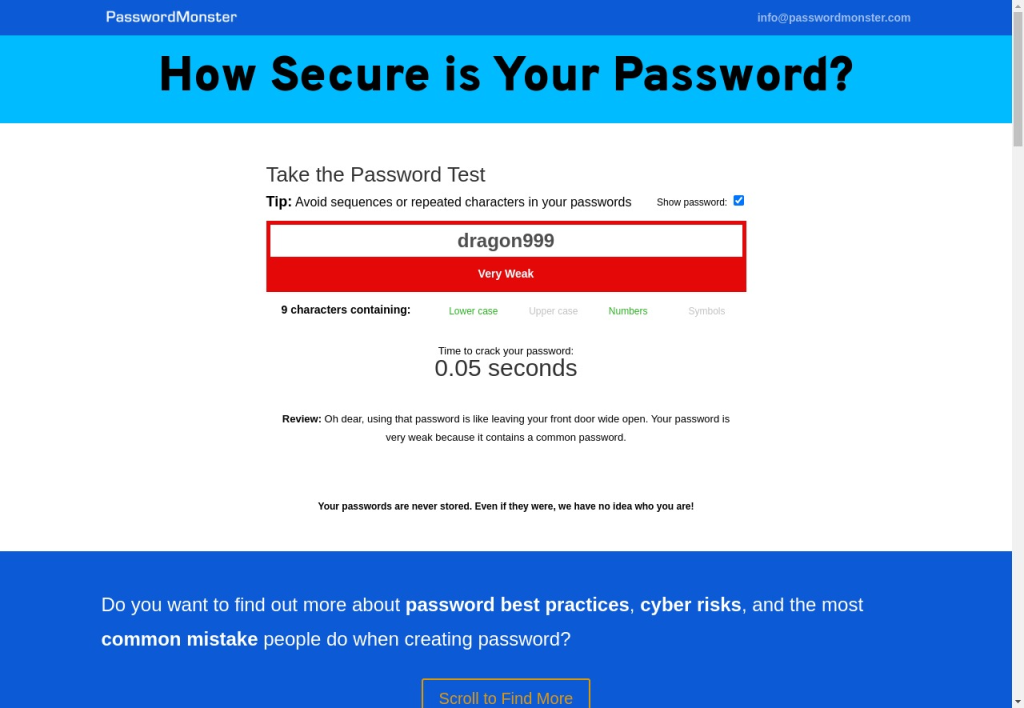
Use complex and unique passwords for all your accounts, especially the WordPress admin account, FTP accounts, and database accounts. A strong password should be a mix of uppercase and lowercase letters, numbers, and special characters.
We also recommend using multifactor authentication wherever possible to reduce the risk of account takeover in case account credentials become compromised.
6. Change the WordPress Login URL
We know that, at any single point in time, hundreds or even thousands of robots are crawling the internet, all looking for a simple misconfiguration or an insecure password on a website. Even if you’re using a strong password, these robots repeatedly try to break into your server by sending the wrong login credentials to the default /wp-login page, which wastes server resources. To avoid such attacks, read our post on how to change the default WordPress login URL.
7. Rename Admin Account to Something Unique
It is strongly recommended to change the default login username to something unique, as the default ‘admin’ username is often targeted by hackers. By changing the ‘admin’ username to something less predictable, you can reduce the risk of brute-force attacks.
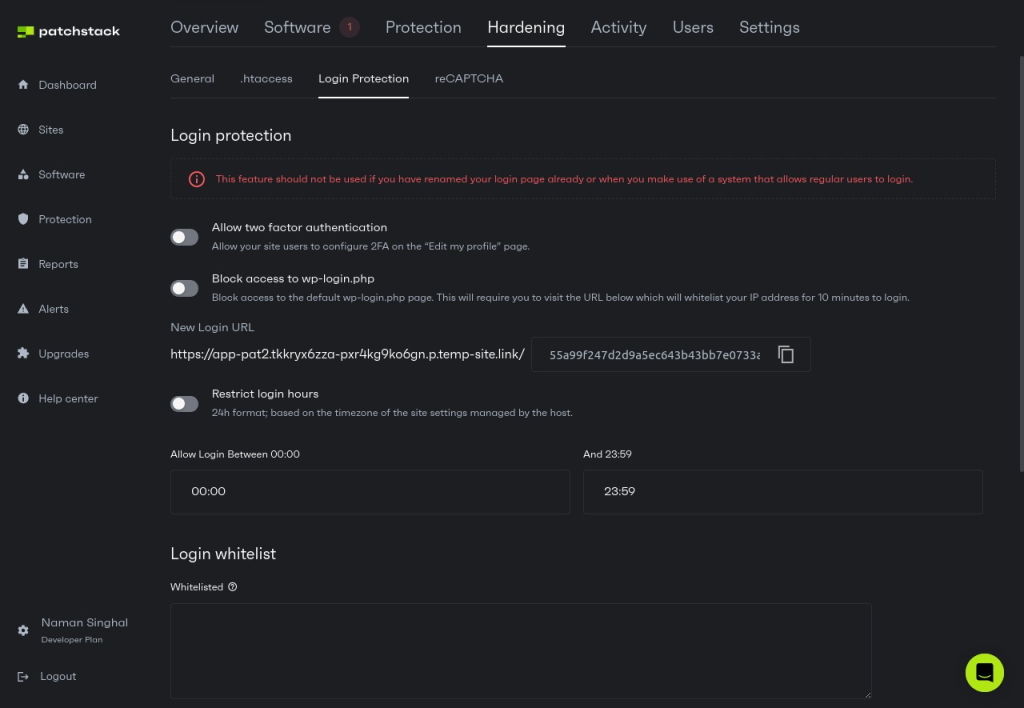
8. Limit Login Attempts
As previously mentioned, vast armies of bots repeatedly try to log in to servers 24/7. By limiting the number of login attempts, you can protect your site from brute-force attacks. Although this method uses IP blocking and can be performed using many different tools, Patchstack users can take advantage of several additional features, such as:
- Customizing the number of failed attempts before an IP is blocked.
- Whitelisting certain IP addresses regardless of failed attempts.
- Customizing the cooldown period after blocking an IP address.
- Restricting all logins during certain hours.
9. Password Protect Sensitive Paths
Although we strongly recommend blocking access to all sensitive information at a firewall level, it isn’t always possible to do so. If you need to serve some sensitive information over the public internet, then you can add an extra layer of security by adding HTTP authentication to these sensitive paths on your website.
For example, many people use phpinfo for diagnostics and troubleshooting errors, but this page also contains sensitive information about website architecture. It is therefore strongly recommended to restrict access to this page using HTTP authentication. The exact steps for doing this will vary depending on your server configuration – look for your cloud provider’s documentation for the precise process.
10. Move wp-config to Parent Directory
The wp-config.php file is a critical WordPress configuration file that contains highly sensitive information, including database credentials, authentication keys, and security salts. By default, this file is located in the WordPress root directory, which may be publicly accessible in many server configurations. Moving wp-config.php to a non-publicly accessible directory (one level above the document root) enhances security by preventing direct URL access to this file, even if other security mechanisms fail.
It's important to note that simply moving the file to a parent directory isn't the key security factor - what matters is placing it in a location that cannot be reached through the web server's public interface.
While the standard practice is to move it one level above the WordPress root directory, the essential requirement is that the chosen location must be outside any publicly served directory while still remaining readable by PHP processes. This configuration helps protect against both direct access attempts and certain types of local file inclusion (LFI) attacks.
This security measure is particularly effective because it works at the filesystem level - even if an attacker manages to exploit a vulnerability in WordPress or bypass other security controls, they won't be able to retrieve the wp-config.php file through standard HTTP requests.
11. Disable File Editing
By default, WordPress allows administrators to edit PHP files of plugins and themes inside the WordPress dashboard. This makes it easy to modify your site’s appearance and functionality on the fly, but hackers can sometimes abuse this privilege to inject malicious code into your website. Disabling file editing helps prevent any unauthorized modifications to these files.
12. Use Custom Database Prefix
Changing the WordPress database table prefix from the default 'wp_' is often suggested as a security measure, but it's important to understand that this practice primarily falls under "security through obscurity". This approach doesn't address fundamental security vulnerabilities or provide robust protection against SQL injection attacks. Instead, it simply makes the database tables slightly harder to identify by automated scripts or manual attempts to exploit known WordPress database structures.
The effectiveness of changing the table prefix is limited to two specific scenarios:
- First, in environments where multiple databases coexist (such as shared hosting environments or systems with honeypots), a non-standard prefix forces attackers to spend additional time identifying the correct WordPress tables, among many others.
- Second, in situations where an attacker has gained the ability to execute SQL commands but doesn't have direct database access, custom prefixes can complicate automated attacks that rely on predicting standard table names.
However, it's crucial to recognize that changing the table prefix is not a substitute for proper security measures. While it may add a small layer of complexity for potential attackers, it doesn't protect against properly crafted SQL injection attacks or other serious security threats.
Real database security should focus on fundamental practices such as properly sanitizing inputs, using prepared statements, implementing strong access controls, and keeping WordPress core, themes, and plugins updated. The table prefix modification should be viewed as a minor complementary measure rather than a primary security control.
13. Update Regularly
Although it might not sound very helpful, updating regularly is one of the simplest ways to protect your website against known vulnerabilities. Regularly update your WordPress core, themes, and plugins to their latest versions, as newer updates often include security patches for known vulnerabilities.
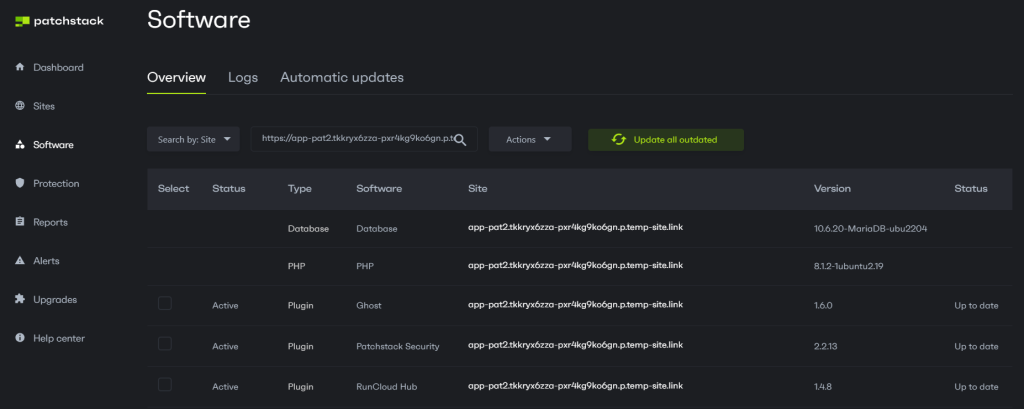
If you’re using Patchstack, you can get notified as soon as any new vulnerability is discovered.
Although not all vulnerabilities are equally important, Patchstack Priority recommends whether a vulnerability requires immediate attention and, if so, enables you to quickly update all your websites from a single screen in the Patchstack dashboard.
14. Use Only Reputed Plugins
At Patchstack, many people ask us one simple question: “Is WordPress Safe?”
The answer is ‘Yes’, but it is not as straightforward as you might think. The core of WordPress is open source and regularly audited by security experts, but third-party plugins are not! In 2021, we found that 99.42% of vulnerabilities originate from plugins and themes, which is quite concerning.
We have always been a strong advocate of using plugins from reputable sources, as poorly coded plugins can make your site vulnerable to attacks. As a result, we have reviewed and scored the best plugins in some of the most popular categories, and we recommend taking a look at the following related posts:
- The Best WordPress Backup Plugins and Services in 2024
- The 5 Best WordPress Image Optimization Plugins
15. Use Patchstack for Monitoring Vulnerabilities and Firewall
Patchstack is the world's leading vulnerability processor (CNA) for WordPress, and it maintains the largest database of WordPress-specific security vulnerabilities.
As a comprehensive vulnerability management and mitigation platform, Patchstack allows WordPress developers and agencies to proactively secure their applications through early detection and rapid response capabilities, and is backed by the European Innovation Council and is a member of the Open Source Security Foundation.
Patchstack offers a 48-hour early warning system for newly discovered vulnerabilities and provides real-time virtual patching (vPatching) technology. Even on the free plan, it can help protect your site from various types of attacks, including SQL injection, cross-site scripting (XSS), and brute force attacks.
Let’s see why WordPress experts recommend Patchstack for website protection:
- Vulnerability Management: Patchstack provides a security dashboard where users can manage alerts, remotely update vulnerable components, create custom protection rules, and export customized security reports.
- Vulnerability Detection: Patchstack alerts users immediately about security vulnerabilities found in their WordPress applications. Users also benefit from a 48-hour early warning for new vulnerabilities found by the Patchstack Alliance ethical hackers community.
- Vulnerability Prioritization: Patchstack prioritizes vulnerabilities based on their potential to be exploited. This feature helps users focus their attention on the most critical issues first, avoiding alert fatigue.
- Vulnerability Mitigation: Patchstack automatically mitigates vulnerabilities with high-precision virtual patching rules. These rules do not alter any code or functionality and have no false positives, ensuring the applications remain safe without disrupting their operation.
SSH Settings (server level)
Although configuring your WordPress settings goes a long way, it is not the only way hackers can attack your website. Secure Shell (SSH) is a cryptographic network protocol used for secure data communication. If an attacker is able to get SSH access to your server, they can take over complete control – and lock you out of your own website.
Needless to say, it’s crucial to harden your SSH settings to prevent unauthorized access. However, not all hosting providers give SSH access to their servers, so if you are completely sure that your hosting provider does not allow SSH access to your server, then you can skip this section.
16. Block Public SSH
The first and arguably most important step is to block SSH connections originating from unknown computers. There are several different ways to do this:
- Use a Firewall: If your hosting provider has configured a network firewall, you can define rules to allow SSH traffic only from certain IP addresses, such as your home or office network. However, not all people have access to a static IP address, which makes this method difficult to implement.
- Use Bastion Host: A bastion host is a special-purpose computer on a network specifically designed and configured to withstand attacks. If you have the technical knowledge, you can block public SSH access to your servers from the Internet and only allow SSH connections from the Bastion Host. This way, you can spend all your resources on securing and monitoring one specific server; this adds an extra layer of security as the bastion host is the only system exposed to the Internet, and the rest of the systems are in a private network.
- Use the Session Manager provided by your Cloud provider: Many cloud providers, such as AWS, provide services to automatically connect to an instance via SSH in a secure manner. You can completely turn off all SSH traffic on your firewall and use fully managed services such as AWS Session Manager to manage your Amazon EC2 instances, either through an interactive one-click browser-based shell or through the AWS CLI.
17. Change SSH Port
By default, SSH listens on port 22, so an easy way to reduce the risk of attack is by changing the default SSH port to a non-standard port. By changing the SSH server to a random port, you will make it difficult for hackers to target your server, and most low-level bots won’t even try to attack you.
18. Use SSH Keys
Although it should be obvious, we will say it again: passwords can be guessed! However, SSH keys are nearly impossible to crack, so if you have enabled SSH access on your server, it is recommended that you turn off password authentication and only use key-based authentication.
19. Don’t Use root Account
When logging in to your server via SSH, it is recommended to use a regular user account with limited access. The root account on any server has the highest level of access – these privileges allow you to run commands that require administrator access, install software, and perform system-wide changes. If misused, it can lead to data loss, system crashes, and security breaches.
HTTP Headers (Nginx level)
HTTP headers are small bits of text that let the client and the server pass additional information with an HTTP request or response. An HTTP header consists of its case-insensitive name followed by a colon (:) and then its value. They can be used to increase the security of your website by enabling certain security features and disallowing certain types of behavior.
To enhance the security of your website, you should definitely configure the following headers according to your requirements:
- Content Security Policy (CSP): CSP is a security standard introduced to prevent XSS attacks. It allows you to create a whitelist of trusted content sources and instructs the browser to only execute or render resources from those sources. Even if an attacker can inject a script tag, the browser won’t execute the script if the source isn’t whitelisted.
- Cross-Site Scripting (XSS): XSS is a type of security vulnerability typically found in web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. To prevent XSS attacks, you should sanitize user input, use CSP, and use HTTP headers such as X-XSS-Protection.
- Cross-Origin Resource Sharing (CORS): CORS is a mechanism that allows many resources on a web page (e.g., fonts, JavaScript, etc.) to be requested from another domain outside the domain from which the resource originated. It’s a useful security feature, but it can be exploited. Therefore, it’s important to only allow trusted sites to request your resources.
To learn more about HTTP headers and how they are used in cyber attacks, we recommend this excellent article on CSRF Attacks and Vulnerabilities.
Additionally, you should check out this amazing article by Servebolt which explains How to Add HTTP Security Headers in WordPress.
Final Thoughts
In this article, we have covered a number of ways to harden your website and protect it from hackers. However, you should always remember that security isn’t a one-time thing, but a continuous process. Always keep yourself updated with the latest security practices and monitor your site regularly for any suspicious activities.
Patchstack logs provide a historical record of actions taken with different themes and plugins. This feature allows users to track changes, monitor activities, and identify potential security issues in their WordPress applications.
Secure your website today with Patchstack! With features such as vulnerability management, detection, prioritization, and mitigation, along with community-powered threat intelligence, Patchstack offers comprehensive protection for your WordPress applications.
Sign up for Patchstack now and safeguard your website against potential threats.