Did worse come to worst and you strongly suspect your WooCommerce store got hacked? We’ll check, going through the key signs, then fight the fire to get you back online (safely) ASAP and show you how to emerge stronger.
Let’s get this solved!
10 signs your WooCommerce store was hacked
Hacks aren’t always big red and bold letters saying: “Give us money or your site gets it!”
Often, they can be more subtle. Here’s what to look out for (not including the fact that your security scanners might be screaming):
- Your site is suddenly moonlighting as a pharmacy or casino - Did your homepage start advertising miracle pills or poker chips overnight? Unless you’re intentionally branching out, this is a clear sign someone’s been messing around.
- Your customers are asking about “that strange email” - If your customers are getting emails with sketchy links, and you know you didn’t send them, it’s time to investigate.
- Random pop-ups and redirects - You know what your products are, so it’s all the stranger when your WooCommerce homepage or product pages start redirecting to scammy sites or offering a “lottery” to get free iPhones.
- New Admin accounts - You check your admin panel and see new users like "H4x0rMast3r" or "Admin2You" with full access.
- Your site is SLOW - If pages are taking forever to load, it might not just be heavy traffic—it could be a hacker's script or malware eating up your resources. Similarly, if your server bandwidth is maxed out (and you’re not running a holiday sale), it could be a sign of an attack.
- Google’s taking note - If Google suddenly lists your site as "This site may harm your computer," you spot links to shady content in your search snippets, spot rankings rapidly dropping, or flat-out get a blacklist or manual penalty notice, it could be a sign of your WooCommerce store getting hacked.
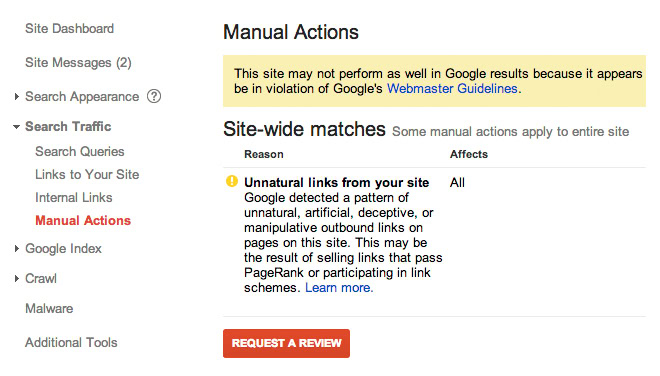
- You can’t log in (but someone else definitely did!) - If your admin password no longer works, and you definitely didn’t forget it, it’s a red flag.
- Weird files in your folders and suspicious custom code - If you’re finding new files or strangely-named and recently-created files in your directory folders, they could’ve been placed there by attackers. Also, check for injected code in theme files, plugin files, or even WooCommerce templates.
- Unusual database behaviors or cron jobs - If your database suddenly grows in size or queries take much longer than normal, it could indicate spam injections, backdoors, or malicious scripts hogging resources. Similarly, check for rogue scheduled tasks in your WordPress admin or hosting control panel.
- Suspicious error logs - Review server logs for frequent errors or strange requests, especially targeting admin pages or .php files. Watch out for repeated failed login attempts – another sign of foul play.
If you’ve spotted one (or more) of these signs, it’s time to do an in-depth dive to determine with certainty if your WooCommerce site has been hacked – and clean it up.
Fight the fire: WooCommerce hack recovery checklist
Step 1. Put your WooCommerce site in maintenance mode to investigate and recover
It’s time to activate your site’s maintenance mode and temporarily disable the checkout process. Go into WooCommerce > Settings > Payments and hit those “disable” switches. This step ensures no weird transactions sneak through while you’re fixing things.
Then, restrict access to the site. Use .htaccess or your hosting panel to block everyone except your IP address with code such as the following (replace the “Your.IP.Address” with your actual IP address):
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REMOTE_ADDR} !=Your.IP.Address
RewriteRule ^(.*)$ - [R=403,L]
</IfModule>
Lastly, double-check your work. Open your site in an incognito browser or from a different device to make sure the maintenance mode is active. Look for any loose ends—like sensitive pages still accessible—and tighten them up.
And with that, you’re officially in repair mode!
Step 2. Scan your site and identify the exact issue
First off, even if your security scanner plugin alerted you to the issue, you won’t stop there. It’ll show you what’s happening at the application layer, but if a hacker could access your WordPress, they could have also tampered with the plugin.
Head to your hosting control panel and run a server-level malware scan. Many hosting providers offer built-in security tools, and if they don’t, reach out to their support team who are usually open to helping in your investigation.
Next, check your logs. Review your website’s error logs, access logs, and any WooCommerce-specific logs to find unusual behavior like numerous failed login attempts, requests to access admin files, or unexplainable activity spikes.
The logs hold the story—you just have to piece it together.
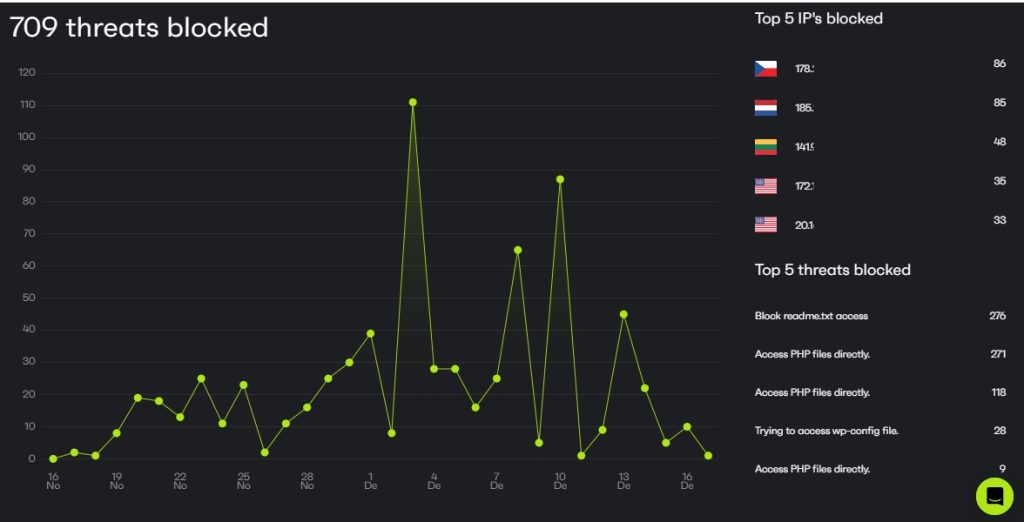
Inspect your database. Take a closer look at key tables like wp_users, wp_options, and wp_post. Look for any strange admin accounts, settings that don’t look familiar, or spammy links sprinkled into your content.
Mind you, hackers love to hide backdoors. These can be extra PHP files or snippets of malicious code tucked into themes, plugins, or even your uploads folder. Use your scanner to sniff them out, but also manually check suspicious-looking files—especially in places like /wp-content/themes/, /wp-content/plugins/, and /wp-content/uploads/.
Finally, check your Google Search Console for any security alerts.
Once you’ve gathered all the clues, it’s time to compile your list of “offenders.” The goal here is to know what the hackers have changed so you know what needs fixing.
Important: Make sure you have the skills for a cleanup
Here’s the thing, this isn’t a regular part of every webmaster’s knowledge.
And if you don’t clean up the hack thoroughly (including all the backdoors), attackers will be able to access your WooCommerce site again.
In some cases, it’s best to look for security providers offering hack cleanup services, just so you’re sure it’s done properly. If you’re already using security solutions or a good hosting company, contact them to see what they can help with.
Step 3. Create a safe backup for post-recovery investigation
Before you dive headfirst into fixing everything on your hacked WooCommerce site, take a deep breath and make a backup—yes, even of the compromised version.
Backing up the hacked site might feel counterintuitive, but it’s a crucial step. It allows security experts (or your future self) to analyze what went wrong—how the hackers got in, what they did, and whether there are any lingering threats.
To create a backup of a compromised WooCommerce site safely, do the following:
- Use a secure backup tool
- Store the files in an isolated location, like an external drive or a cloud account unconnected to your WooCommerce hosting
- Avoid overwriting your existing clean backups
- Label the backup clearly (e.g., “Hacked_Site_Backup_Dec_2024”)
- Resist the urge to open it on your regular system without proper precautions!
Step 4. Remove malware
Once you’ve identified the infected files, remove or quarantine them.
If you’re unsure which files are legitimate and which aren’t, consult your hosting provider or a professional malware removal service.
Run another scan after you’re sure that you got them all – just to be on the safe side.
Step 5. Change all your passwords
Update every single password connected to managing your WooCommerce site:
- Your WordPress admin account
- Database
- Hosting control panel
- FTP/SFTP accounts
- Email accounts
- API keys
- Third-party integrations
- The passwords for any user accounts on your WooCommerce store (especially with higher permissions)
When creating new passwords, think “strong” and “unique.” These days, it’s easiest to use a password management tool because it auto-creates what looks like nonsense but is in fact a pretty strong string of code used as a password.
Don’t forget about your WooCommerce customers! If there’s any chance their accounts were compromised, prompt them to reset their passwords, too. (It might not be the most pleasant email to send, but it beats explaining why someone ordered 50 kettlebells with their saved payment method.)

Step 6. Restore your site from a clean backup
A clean backup is your digital reset button. But, as with all things in life, timing and method are everything.
First, ensure you’re using a verified clean backup. This should be a version of your site from before the attack, ideally one stored offsite (e.g., in cloud storage or on an external drive) and untouched by the attack.
If you’re not sure which backup is clean, consult your logs or a professional. Restoring from a compromised backup is like putting a band-aid on a broken dam—it’s not going to end well.
Once you’ve identified the right backup, follow your hosting provider’s restoration process. This usually involves overwriting your current site files and database with the clean version. Be meticulous: take care to check that every file is replaced and every sneaky hacker script is gone.
If you’re restoring manually, double-check that permissions, configurations, and file structures are intact.
Step 7. Update all your WooCommerce site components (and keep them updated!)
In 2023, plugins were responsible for 97% of all new security vulnerabilities. Plus, the easiest way for an attacker to gain access to your site is to launch a mass attack against all sites online, targeting specific vulnerabilities: if your plugins haven’t been patched or updated in time, you’ll get attacked.
From your WordPress core to the smallest plugin, every outdated component is a potential weak spot.
Start by updating the WordPress core. If your site was running on an older version, hackers may have used vulnerabilities to slip in.
Then, update your plugins and themes. WooCommerce itself is a common target, so ensuring it’s fully updated is non-negotiable. Check for updates to all your plugins, even the ones you’re not actively using.
If you have outdated plugins or themes you no longer need, delete them entirely—deactivating isn’t enough to eliminate risk.
The problem: attacks happen fast
So unless you’re able to update a plugin as soon as there is a vulnerability (and hoping that the plugin developer has issued a security fix that fast), you could still get attacked. In the Bricks incident, it only took a few hours for the vulnerability to become mass-exploited.
This is where virtual patching helps: applying a highly-targeted security rule that blocks the exploit of that specific vulnerability.
And with the world’s most robust WordPress vulnerability database, Patchstack is the first to know, alerting and protecting you 48 hours before a vulnerability goes public!
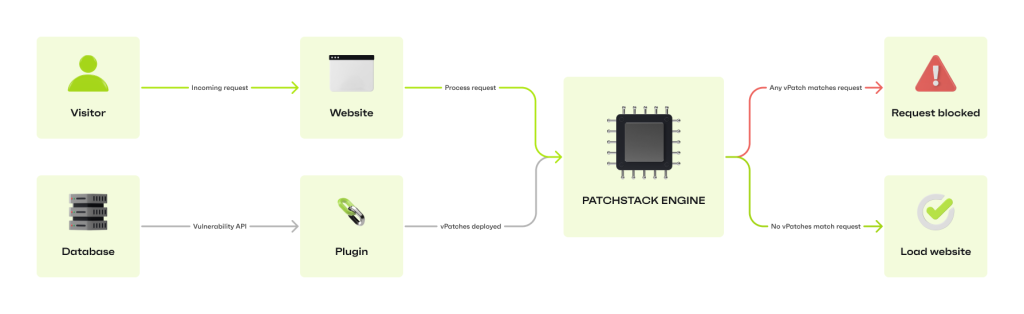
Since Patchstack’s virtual patches are security rules, they don’t affect your site or plugin code, allowing you to retain full functionality until you can test and apply the update safely.
Step 8. Check and remove unauthorized accounts
After recovering your site, it’s critical to root out the unauthorized accounts hackers may have created and revoke their access.
Start with your WordPress user accounts. Go to Users > All Users in your WordPress dashboard, and review every account listed. Pay special attention to administrators—there shouldn’t be any accounts you don’t recognize. If you spot an account you don’t remember creating, it’s likely an intruder’s handiwork.
This is also a good time to apply the Principle of Least Privilege: only give users on your WooCommerce site the access levels they absolutely need to do their jobs.
Does a blog writer need Editor permissions? No. Does anyone but the person managing your site need Admin access? Absolutely not!
For WooCommerce-specific roles, such as shop managers or customer accounts, comb through the list for anything unusual. Hackers sometimes use these roles to gain limited access, which they can escalate later.
If you allow customer registrations on your site, filter by recent registrations to catch any accounts created during the breach.
Once you’ve identified unauthorized accounts, delete them immediately. Before doing so, note down any details like the email address or creation date—this could be useful if you’re investigating the breach further.
For extra caution, audit the database directly. Use a tool like phpMyAdmin or your host’s database manager to inspect the wp_users table for hidden accounts that don’t appear in the WordPress dashboard. Sometimes, hackers insert these accounts directly into the database to avoid detection.
After removing unauthorized accounts, reset passwords for all legitimate users. Then, enforce 2FA for all admin and shop manager accounts.
Step 9. Inspect orders and customer data
Start by reviewing your most recent orders. Look for anything suspicious, such as:
- Orders from unfamiliar or unusual locations.
- Orders that were placed in bulk but have unusual or incomplete customer details.
- Any strange items or discrepancies in the products ordered.
Pay attention to payment gateways. If your payment processor supports logging, review the logs for any unexpected transactions or failed payment attempts that could indicate fraudulent activity.
Next, dive into customer accounts. Look for signs that customer data has been altered or exposed. Some red flags include:
- Customer profiles with strange or incomplete email addresses.
- Unusual shipping or billing addresses tied to accounts that seem suspicious or foreign.
- Duplicate or mass registrations that could indicate automated bot activity.
If you suspect any customer accounts have been compromised, notify the affected customers immediately. You might need to ask them to reset their passwords or update their payment information, particularly if you believe sensitive data (like credit card details) may have been exposed.
If you’ve been collecting data like credit card details or personal identification numbers, ensure they’re encrypted and stored securely. If the breach exposed this data, it may be required by laws like CCPA and GDPR to notify them.
Be transparent. Customers know that breaches happen, but you can prevent a lot of nasty consequences by communicating the issues directly with them, instead of losing their trust forever (and paying hefty fines) because you’ve swept a breach under the rug.
It’s also a good idea to check your site for any unauthorized changes to order statuses or stock levels.
Final step: Learn from the WooCommerce site hack and strengthen your security
Once the dust has settled and your WooCommerce site is back up and running, it’s time to take a moment to reflect.
How did the hackers get in?
Start by conducting a post-mortem of the attack. How did the hackers get in?
- Was it a weak password?
- An outdated plugin?
- Or a vulnerability in your hosting environment?
Understanding the "how" behind the breach is crucial, as it helps you pinpoint weak spots and avoid repeating the same mistakes. Consider consulting a security expert to help you analyze the attack vector in detail.
Strengthen the layer(s) that failed
If hackers used a weak password to get in, you need to strengthen the access management layer with measures like enforcing 2FA and strong passwords.
If it was an outdated plugin, the issue occurred at the application layer.
A vulnerability in your hosting environment causes significant challenges at the server layer.
Ultimately, go through your entire site to map the attack vectors so you can mitigate them properly. Take it one layer at a time – you can also follow our guide to understand the best practices for each!
Monitor and audit your site to prevent future WooCommerce hacks
Not only are you required by PCI-DSS 4.0 to keep an audit and activity log of transactions and events on your site, but it’s also a security best practice.
Keep track of every action on your site, from login attempts to changes in product inventory. This might sound like overkill, but it’s an effective way to spot trends or unusual activity that could indicate something’s wrong.
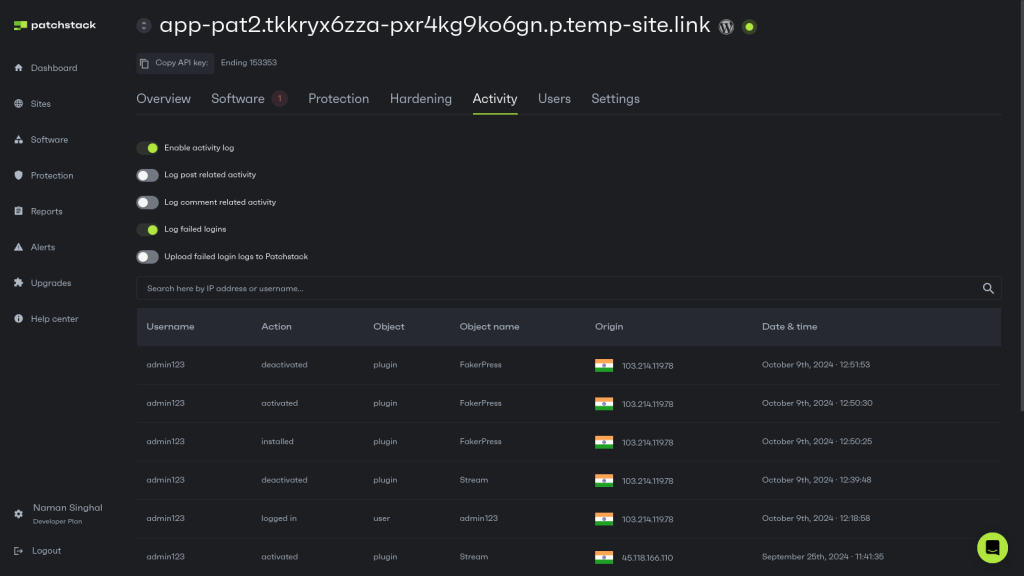
On top of monitoring, perform comprehensive security audits at least once per quarter (or more often if you’ve had a recent hack or significant site changes).
Review access logs, scan for malware at the server level, perform file integrity monitor checks, and ensure your backups are intact and accessible.
Follow the guidance in our ultimate WooCommerce security checklist!
During audits, revisit user roles and permissions:
- Are there any users with admin access who shouldn’t have it? (Including your team.)
- Are there unnecessary accounts that could be deleted?
You should also test your backup process regularly.
Finally, stay (and keep your team) up to date on security best practices. As technology evolves, so do the threats. Subscribe to security newsletters, read the relevant security blogs, and keep analyzing to make your security posture even better.
Recover from the WooCommerce hacks and emerge stronger
Hacks can be like digital tornadoes – everything suddenly spins out of control. But now you have the power to rebuild stronger than before.
By following the checklist I shared with you —from removing malware and cleaning up your site to learning from the experience and strengthening your security—you won’t just be fixing a problem.
You’ll be setting up a system ready to withstand future attacks.
Protect the weakest link in WooCommerce security: outdated components. Learn how Patchstack’s customers do it with 48-hour early warnings & real-time protection.





