With frequent breaches, credit card fraud, and assorted ways attackers can compromise sensitive payment information (and the companies like eCommerce websites processing them), it’s no wonder the PCI-DSS got a new edition: PCI-DSS 4.0.
However, with the update comes a plethora of new information. If you’ve been racking your brain trying to figure out what you (or your clients) need to do to stay compliant in eCommerce, read on!
We’ll show you the key areas to cover, explain the newest additions, and provide an actionable checklist for PCI-DSS 4.0 eCommerce compliance.
Note: When implementing your PCI-DSS compliance plan, work with a PCI Certification authority that can analyze your unique case to ensure you stay compliant. This article provides general guidelines and isn’t a substitute for legal or regulatory advice.
Is my eCommerce website subject to PCI-DSS 4.0 regulations?
The Payment Card Industry Data Security Standard (PCI-DSS) helps organizations that handle credit card and payment information protect their customers.
Now, the term “organizations that handle payment information” is quite vague, so you might be wondering – does my business need to comply?
The answer is: yes, but the exact level of PCI-DSS compliance depends on the amount of transactions you process per year.
There are 4 compliance levels:
- Level 1: Merchants handling 6M+ card transactions annually.
- Level 2: Merchants handling 1-6M transactions annually.
- Level 3: Merchants handling 20K to 1M transactions annually.
- Level 4: Merchants handling fewer than 20K transactions annually.
So even if you have a new eCommerce store and haven’t processed a single transaction, you still need to comply with PCI-DSS.
What are the main changes in PCI-DSS 4.0?
While the official documentation elaborates on the main changes in the 4.0 version, the following caught our eye in particular:
Customized approach to implementing PCI-DSS
Instead of prescribing solutions, the 4.0 version now gives more flexibility in establishing and customizing your processes – as long as you still meet the same security requirements and prevent breaches.
MFA and password security
PCI-DSS 4.0 includes strengthened requirements for password security and Multi-Factor Authentication (MFA), including its use for all access to the cardholder data environment.
Addressing vulnerabilities
PCI-DSS 4.0 now requires you to continuously monitor and address vulnerabilities, regardless of the severity level (high, medium, and low). There’s also a renewed focus on vulnerability management (but more on that in a second).
Continuous monitoring and regular risk assessment
One thing is clear: PCI is more than aware that cybersecurity isn’t a set-it-and-forget-it scheme. Instead, the new directives require continuous monitoring and regular assessments to make sure you’re doing everything in your power to prevent cybersecurity incidents.
Risk assessments are a must, too.
The key step is mapping your attack surface, i.e., all the vectors hackers could use to gain access to your eCommerce site. From there, you can understand which layers need additional protection.
Securing the third-party supply chain
No site is an island, and that’s especially true when you’re building a WooCommerce site with payment gateway integrations, plugins for added functionality, and other aspects.
PCI-DSS 4.0 is more aware of how vulnerabilities in one part of the supply chain can lead to compromising the entire chain and end users.
Incident response
Finally, PCI-DSS 4.0 clarifies the requirements for dealing with breaches and security incidents. It’s best to work with security experts on implementing it, but the goal is to be able to respond quickly and accurately to any threat or compromise.
Do I need to comply with PCI-DSS if I use a payment gateway?
Now, here’s the kicker: if you’re not processing CC information yourself, that doesn’t absolve you of the need to comply with PCI-DSS.
In these cases, the responsibility is shared between you and the payment gateway.
Note: When implementing your PCI-DSS compliance plan, work with a PCI Certification authority that can analyze your unique case to ensure you stay compliant. This article provides general guidelines and isn’t a substitute for legal or regulatory advice.
What PCI-DSS directives is the payment gateway responsible for?
In a scenario where you use a payment gateway, they’d likely be responsible for adhering to the following PCI-DSS directives:
- Secure processing of payments (Processing transactions securely, encrypting cardholder data, handling tokenization)
- PCI DSS compliance (Ensuring full compliance, undergoing frequent audits to maintain their PCI-DSS certification)
- Fraud detection and prevention (Using tools and systems to prevent fraudulent transactions, offering additional mechanisms for verification like 3D Secure)
- Data storage (Following PCI standards for storing and encrypting cardholder data)
- User authentication
On the other hand, your site is responsible for everything else up until the point of the handoff.
What PCI-DSS directives is my eCommerce site responsible for?
Your eCommerce website would most likely be responsible for the following parts of the PCI-DSS compliance:
- Website security (Ensuring the site is secure by implementing SSL/TLS and encryption throughout the checkout process, vulnerability management)
- Secure data handling (Encrypting and securing any temporary card or financial data, preventing XSS and SQLi attacks through secure coding practices)
- Integration with the payment gateway (Using webhooks, properly integrating the payment processor’s API, JavaScript library, and other components)
- Access control (Making sure no one but authorized staff can access payment processing, using the principle of least privilege when assigning user roles, enforcing 2FA and MFA)
- Monitoring and logging (Monitoring the website for suspicious activity, logging activities, transaction activities, and access)
- Training (Educating your staff on PCI DSS requirements)
How to stay compliant with PCI-DSS in eCommerce
If you’re in a situation where your eCommerce website uses a payment gateway, read on to learn how to protect the areas you’re responsible for!
1. Manage vulnerabilities to comply with PCI-DSS 4.0
One of the key updates announced in PCI-DSS’ 4.0 edition was vulnerability management. This means keeping your software up-to-date and monitoring for vulnerabilities.
Now, the server side of things should be handled by your hosting provider. However, if you run your eCommerce website on WordPress, i.e., WooCommerce, you should be aware of another level of vulnerabilities:
WordPress core, plugin and theme vulnerabilities.
Since WordPress is one of the most popular content management systems (CMS), it’s a frequent target of attacks. The open-source Core itself is often reviewed, but plugins and themes remain in the hands of plugin developers, leaving room for logic errors in the code that hackers love to exploit.

Since PCI-DSS mandates a secure environment for handling cardholder data, any failure to manage vulnerabilities could be treated as being non-compliant, resulting in fines.
The first thing we all do is manage updates.
However, hackers can exploit a plugin vulnerability in hours (and, in some cases, minutes). With plugin updates often breaking the sites’ functionality, it’s normal that you need more time to test them and back up your site before applying them.
During that time, your eCommerce website is staying exposed to potential attacks.
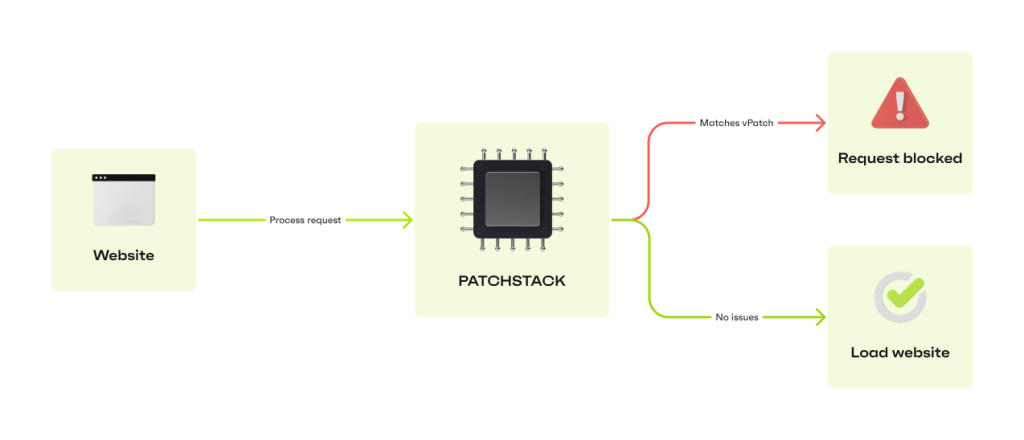
The best solution is prevention.
Patchstack first alerts you to vulnerabilities spotted in your plugins (for free). Then, with the real-time protection enabled ($5/mo/site), it applies a virtual patch to the vulnerability, preventing exploits.
Since the virtual patch doesn’t affect your website code and functions as a highly-targeted security rule, your store’s performance won’t be affected but you will be protected.
“A lot of the time, with auto-updates, it messes up something else on the site which causes us and our clients a lot of headaches. Of course, if you just leave the plugin without any protection, it opens a back door for a hacker to come in and do whatever they want to with the site. We had to find a way of protecting those plugins while still being able to have a functioning site, which is where Patchstack came in.”
- Christopher Thompson, Founder and CEO @ Property Portal Marketing
In that sense, Patchstack’s vulnerability mitigation directly helps you stay compliant with this aspect of PCI-DSS 4.0’s directives.
2. Use firewalls
You’re probably already familiar with firewalls, but PCI-DSS encourages their use, as well. Use them to protect cardholder data and filter out suspicious or spammy traffic.
Typically, we recommend using a firewall like Cloudflare to protect you at this network level.
3. Implement secure configuration and hardening
In addition to changing all system and app defaults like passwords and configurations, PCI-DSS also stipulates that you should use the best practices for system hardening.
In WordPress, hardening means protecting login pages, keeping a close eye on how you assign permissions, etc.
4. Maintain your configuration
Configuration also includes your servers.
If you use managed WordPress hosting, you should be able to get regular server software updates, server-side malware scanning, backups, and similar features to protect your servers and eCommerce sites against unwanted access.
5. Protect stored account data and cardholder data
Wherever possible, don’t store cardholder and financial or payment data.
However, in the parts of the process where you manage or store them, make sure you have strong encryption (e.g., TLS) to prevent intercepts. If you’re in charge of handling payments, use tokenization to replace credit card information with tokens.
Similarly, all API and third-party integration communications should be encrypted via TLS. Make sure the API endpoints are also secured with HTTPS!
When it comes to your encryption keys, store them safely and restrict access. Only the people directly managing the payment process should be able to access them. It’s not a matter of trust – your team could be the most trustworthy people on the planet, but everyone’s susceptible to mistakes and hackers know how to exploit the flaws in our behavior for their benefit.
6. Monitor behavior with activity logs
The key priority is monitoring access to cardholder data.
However, it’s also important to monitor all user activity on the site, so you know who has accessed which parts of it and what they attempted to do.
For example, in Patchstack, the activity log shows you the IP addresses, the users, and the actions they tried to perform. This way, even if it’s something completely benign, you’d be able to identify who made a change:
7. Perform regular audits
PCI-DSS compliance is not a set-it-and-forget-it – you need to make sure your systems are constantly meeting the requirements and new threats.
Regularly audit the following aspects to stay compliant:
- Vulnerability scans – Use tools like Patchstack that will scan your WordPress/WooCommerce site for vulnerabilities (and mitigate them).
- Penetration testing – Work with experts to identify the vulnerable layers of your eCommerce site security, so you know how to manage the risks.
- Code reviews – Contact security experts who can review your code to spot any gaps.
- Configuration reviews – Make sure your configuration, from the server and network to the front-end layer, is waterproof.
- Access control reviews – Periodically review the access levels you’ve given to different people on the team and reduce them as needed. Remember the principle of least privilege: only give people access to the things they absolutely need to perform their tasks.
- Log and monitoring reviews – Review your financial data access and activity logs regularly to make sure there isn’t any suspicious activity.
- Compliance audits – Work with certified providers to ensure your PCI-DSS compliance is up to par.
- Employee training and awareness – Hold training sessions for your team, so they know exactly how to stay compliant and think about security.
8. Monitor for breaches
If the worst comes to the worst, you need to know about it as soon as possible. That’s where Security Information and Event Management (SIEM) systems like Splunk or IBM QRadar come into play.
They aggregate information from multiple sources (e.g., firewalls, databases, applications, etc.) and alert you if there are events that might indicate a breach.
However, the other two things we recommend implementing are file integrity monitoring (monitors that scan your site for any anomalies or changes that shouldn’t have happened) and server-side malware scanning.
Similarly, monitor your firewall traffic, vulnerabilities, and activity logs for suspicious activity.
If there is an incident and you need to respond quickly, having a reliable stack and incident response plan will help you identify, quarantine, and remove the threat.
Who can validate my PCI compliance?
When implementing PCI-compliant systems, work with qualified experts certified by the PCI. You’ll find a list of professionals with different qualifications, depending on your compliance level on the official PCI site.
Note: This article isn’t a substitute for working with a PCI-certified professional. When implementing your plans, consult the regulatory authority or licensed professionals.
Security is the main priority
The stakes are high. Data breaches aren’t just costly; they can devastate your reputation and erode customer trust in a heartbeat.
PCI-DSS 4.0’s updated guidelines help you fortify your defenses, so you’re not just meeting the minimum standards but actively protecting your site(s) from emerging threats.
Tackle them head-on, starting from today!





