On the 6th of January 2022, WordPress.org released a security update and recommended users to “update your sites immediately”. This WordPress core 5.8.3 security update addresses 4 different security vulnerabilities which affect WordPress core versions between 3.7 and 5.8.
For many, WordPress automatically updates the core to the latest version. Check if your WordPress version is 5.8.3 - if not, update immediately!
Stored XSS through post slugs
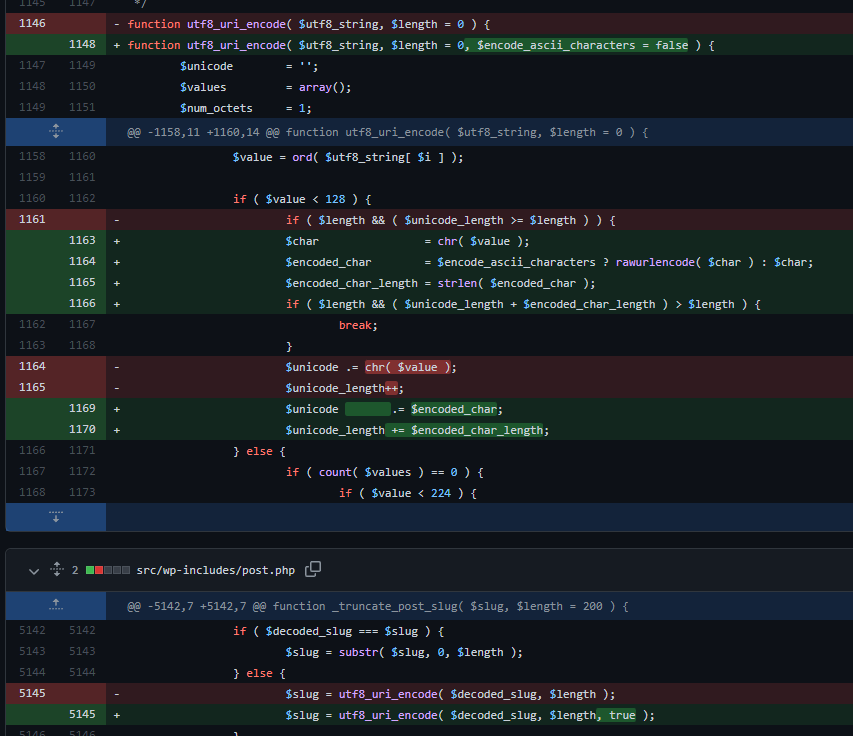
Based on the changes of the code which can be found here, it seems that the _truncate_post_slug function located in /wp-includes/post.php has been changed.
It now passes a true value to the third argument of the function utf8_uri_encode which can be located in /wp-includes/formatting.php. This function has been modified to accept this third argument which, if set to true, will encode ascii characters such as <, “ and ‘.
Potential impact
In theory, it could allow a user with higher privileges, such as authors, to perform XSS by crafting a malicious post slug in posts. We do not expect this vulnerability to be actively exploited as it requires higher privileges than the usual subscriber user role.
What to do?
For many, WordPress automatically updates the core to the latest version. Check if your WordPress version is 5.8.3 - if not, update immediately. In case there is a very strong reason why an update can’t be done, consider signing up for Patchstack here.
See more from Patchstack database: WordPress Core 5.8.3 Security Update - Stored XSS
Object injection in multisite installations
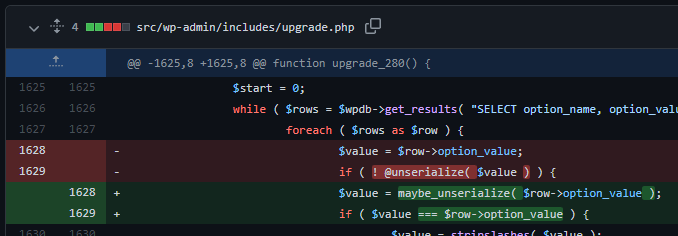
Based on the changes of the code which can be found here, it seems that the upgrade_280 function located in /wp-admin/includes/upgrade.php has been changed.
This upgrade function is used during the upgrade/install process from a much older multisite WordPress version to WordPress 2.8. This function loads all WordPress options and then unserializes the value of the option using the unserialize function. However, as the option value could contain user-supplied data, it could in theory cause an object injection vulnerability to occur.
This function has been modified to unserialize data using the function maybe_unserialize, which only unserializes data that is actually serialized. In addition to that, they now also check if the option value matches the unserialized value after potential unserialization to make sure it is not a serialized value.
Potential impact
We do not expect this vulnerability to be actively exploited as it only affects very old WordPress installations and only affects the upgrade/install process from a WordPress version that is older than 2.8 and is upgraded to a WordPress version that is newer than 2.8.
What to do?
For many, WordPress automatically updates the core to the latest version. Check if your WordPress version is 5.8.3 - if not, update immediately! In case there is a very strong reason why an update can’t be done, consider signing up for Patchstack here.
See more from Patchstack database: WordPress Core 5.8.3 Security Update - Object Injection
SQL injection vulnerability in WP_Tax_Query
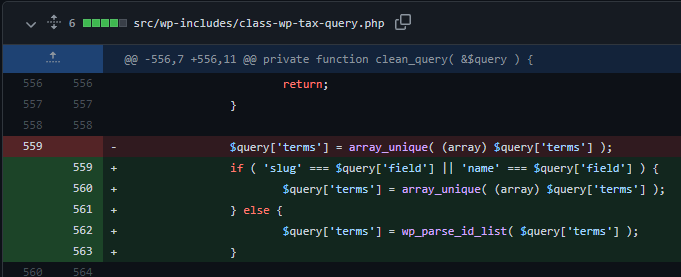
Based on the changes which can be found here, it seems that the function clean_query has been changed. Previously it would extract all unique terms from the $query[’terms’] array variable, however, this has been changed to only extract the unique values of the array if the field name of the query equals slug or name. If this is not the case, it will get the absolute integer value of all unique array values.
Potential impact
We do not expect this vulnerability to be actively exploited as it requires multiple pre-requisites. If however, we do see any attempts to exploit this vulnerability, we will follow up with more information.
What to do?
For many, WordPress automatically updates the core to the latest version. Check if your WordPress version is 5.8.3 - if not, update immediately! In case there is a very strong reason why an update can’t be done, consider signing up for Patchstack here.
See more from Patchstack database: WordPress Core 5.8.3 Security Update - SQL Injection
SQL injection vulnerability in WP_Meta_Query
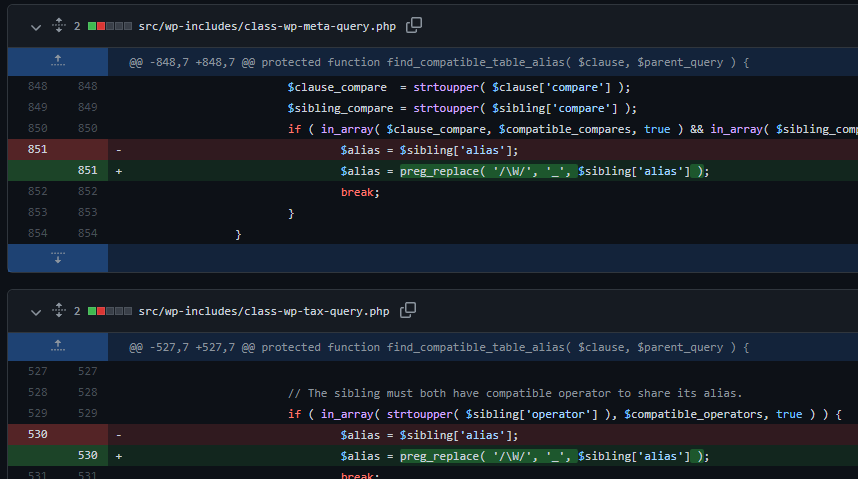
Based on the changes which can be found here, it seems that the function find_compatible_table_alias in both /wp-includes/class-wp-meta-query.php and /wp-includes/class-wp-tax-query.php has been changed.
This function in both files has been modified to clean the $sibling['alias'] variable. More specifically, it replaces any non-word character (not part of 0-9, A-Z, a-z, _) with an underscore. This would prevent SQL injection by removing the possibility to inject characters such as ‘, “, (, ) and spaces.
Potential impact
We do not expect this vulnerability to be actively exploited as it requires multiple pre-requisites. If however, we do see any attempts to exploit this vulnerability, we will follow up with more information.
What to do?
For many, WordPress automatically updates the core to the latest version. Check if your WordPress version is 5.8.3 - if not, update immediately! In case there is a very strong reason why an update can’t be done, consider signing up for Patchstack here.
See more from Patchstack database: WordPress Core 5.8.3 Security Update - SQL Injection
Thanks to security contributors!
Credit to the researchers and developers who contribute to making WordPress (and a large portion of the web) more secure: Karim El Ouerghemmi (SonarSource), Simon Scannell (SonarSource), Ngocnb (GiaoHangTietKiem JSC), Khuyenn (GiaoHangTietKiem JSC), Ben Bidner (WordPress Security Team).
See the official WordPress.org announcement: https://wordpress.org/news/2022/01/wordpress-5-8-3-security-release/





