Welcome back to the Patchstack Weekly security update! This update is for week 14 of 2022 and I will talk about the first 5 steps to a secure WordPress.
This week has a lot of vulnerability news to cover, and I will be sharing it as a 3-2-1 punch of 3 plugins that received no patch for security bugs, 2 premium plugins that patch critical security bugs, and 1 public exploit already being shared for a Local File Inclusion vulnerability.
In this week's knowledge share, I will talk about the first 5 steps of WordPress security. These steps are not the only steps you should take for security, they are the steps you should be taking when you are first setting up a WordPress website from scratch, to ensure it is secure from day 1. I will add a bonus step for bare basic security maintenance.
Vulnerability news
3 plugins with no patch for high-risk vulnerabilities
Please be on the lookout for the following plugins, each is affected by an unauthenticated SQL Injection vulnerability and unfortunately, none have received a public patch at this time.
- Users Ultra plugin - Unauthenticated SQL Injection (SQLi)
- Master Elements plugin - Unauthenticated SQL Injection (SQLi)
- Donations plugin - Unauthenticated SQL Injection (SQLi)
2 plugins patch critical security bugs
The following premium plugins have patched high severity (CVSS 9.8) security bugs in their projects recently. Users will need to make sure they have applied the patch made available ASAP, since these are premium plugins you may need to manually update the plugin.
Which could mean you need to check if the plugin has an auto-update button to click, if not, then you will need to download the updated software from the vendor, upload it to your site yourself, and replace the old version of the plugin with the new one.
- Flo Launch plugin - Missing Authentication Allows Full Site Takeover
- Tatsu plugin - Unauthenticated Remote Code Execution (RCE)
1 public exploit is being distributed
Cab fare calculator plugin - Unauthenticated Local File Inclusion (LFI)
The Cab Fare Calculator plugin developers patched an unauthenticated local file inclusion vulnerability which users should update as soon as possible.
There is public proof of concepts already published for this vulnerability, which requires no authentication to perform … the silver lining is: that it has restrictions where only files ending in .php that exist in the local filesystem will be included.
Weekly knowledge
Five steps to a secure WordPress from scratch
This is basically a short version of your WordPress security starter pack.
Set up HTTPS
- Right from the start, when you are setting up your hosting environment, make sure you enable and set up HTTPS before starting your installation! This is free with LetsEncrypt and will not only help security by encrypting your traffic but help with SEO rankings as well!
Now you can run the installation script, and when you choose your first admin user's password you will be sending it over encrypted channels. And while you're choosing that password, that is the next point I will bring up!
Choose unique, strong passwords
- Your passwords should be hard to guess, and should not be used on any other of your accounts online. If that sounds difficult to remember, then try using a password manager to help you keep track. We have written a full guide for good passwords here.
- Even better, use 2-factor authentication! Although you will need to install a plugin for 2FA, so let's move on to the next step, installing security-related plugins.
Install a security plugin
- There are a lot of security plugins available in the WordPress.org plugin directory. But, let's make this step easy: Patchstack has your back, with the free Patchstack plugin. It offers a handful of useful security settings, including 2FA, hiding your login screen, and provides security notifications if you are running a known insecure plugin.
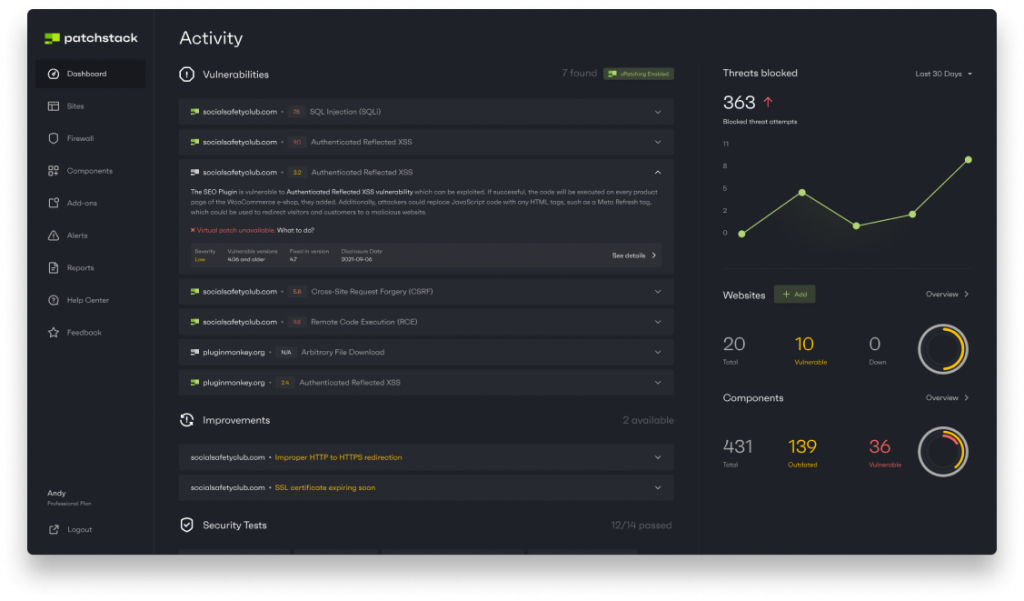
Knowing if one of your WordPress websites is running components with known insecurities will help empower you to remove the vulnerabilities before they are exploited. This will also help you with the next step: which is something you will need to do regularly.
Keep your site and its components up to date
- You may not need all the new features and functionality of every release. But you absolutely need the security updates.
- If you want this to be simple, you can turn on all auto-updates. This works, but if you have the Patchstack plugin installed and set up (like I recommended in the last step) then you will see notifications when your site is running a known insecure plugin so you'll get to choose and get auto-updates for vulnerable plugins only.
This will get you off to a great start running a secure WordPress website. Once you have your components updating, and user accounts locked down, it will be smooth sailing. But, there will be some occasional maintenance needed.
This brings me to the final point in this short article, what you should do every so often, monthly, quarterly, maybe yearly to help review and manage your site's security.
Perform periodic cleanups
- Disable any unused user accounts, maybe someone left the organization or they no longer contribute to your site.
- Ensure you have only a few (or none) admin users. And that these accounts are secured with 2FA or other high-security mechanisms.
- Remove all unused plugins and themes.
- Verify that your active plugins and themes are still getting regular updates. If a plugin hasn't been updated in a few years, it might be time to reconsider its value on the site.
There is so much more you could talk about when it comes to WordPress site security, but this list is a great start.
One more extra step for a secure WordPress
It is helpful to talk with your webmaster or hosting provider about security, it will help you understand what they do and what you are responsible for. You may be surprised how much security your hosting provider or webmaster may already be doing for you.

A growing list of hosting providers has partnered with Patchstack. GridPane, Cloudways, Plesk, Pagely, and more use Patchstack's WordPress vulnerability intelligence to power their customer's WordPress website security.
If your hosting provider is not a Patchstack partner, you can always use the free Patchstack WordPress plugin for notifications and maybe mention to your hosting provider that they should partner with Patchstack for vulnerability intelligence. It never hurts to ask.
Thanks and appreciation
This week's thanks go out to the developers of the Flo Launch, Tastu, and Cab fare calculator plugins. Thank you for the work in squashing your projects security bugs.
A special thank you to the Patchstack Alliance team members, who are working hard to find, report, and communicate security bugs for the WordPress ecosystem.
I will be back next week with more security tips, tricks, opinions, and news on the Patchstack Weekly security update!





