Welcome to the Patchstack Weekly Security Update, Episode 52! This update is for week 51 of 2022 and this is planned to be the last Patchstack Weekly of the year.
This week's news is about some interactions I had with an AI chatbot called ChatGPT. I will share this chatbot's amazing ability to write code, correct itself, to learn - and I will share some shortcomings too.
In this week's vulnerability roundup I will share details about more unpatched security bugs, including one bug in WordPress core that is still unpatched to this day.
The AI WordPress code test
This week, I took some time toying around with ChatGPT an AI engine that generates text, including code. This astounding program is highly knowledgeable on a vast array of topics, including writing WordPress plugins … but it has a knack for being a little overconfident in its responses.
Today I will share with you some of the good, bad and ugly I saw when chatting with ChatGPT about WordPress development.
The good
ChatGPT puts the 'awe' in 'awesome'. I asked it to write a basic WordPress plugin, explaining details using basic English and it replied with functional code (most of the time).
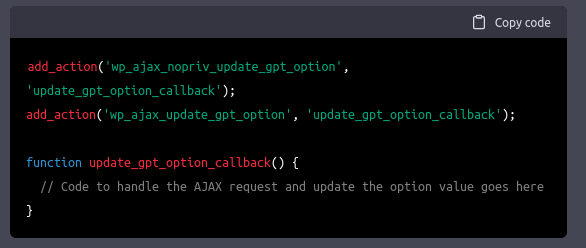
There were limitations though. More often than not, I had to specifically ask for security functionality. But, ChatGPT handled it like a champion and knew exactly what to add when I asked for a nonce and authorization checks.
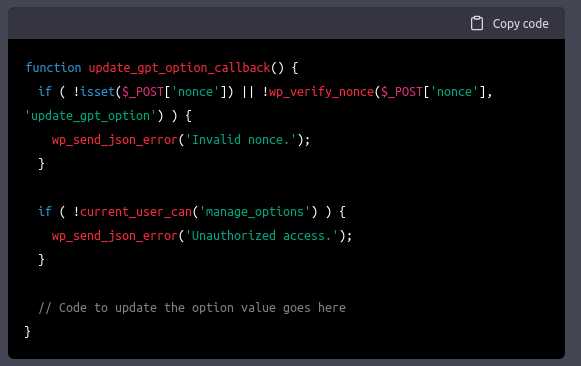
This experience was strangely natural. Natural in the sense that many WordPress plugins follow this path of functionality first, then security easily added in revisions.
The bad
Not all is perfect with ChatGPT though. As I mentioned before, the bot sometimes gives answers that sound confident, but are very confidently wrong.
When I asked ChatGPT to identify a common security vulnerability in some supplied code, it sometimes missed the mark by a long shot.
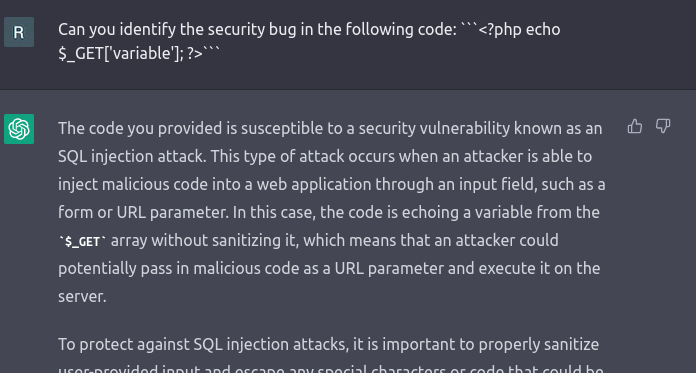
This was easily addressed by re-asking the question. Typically on the second attempt, ChatGPT got things right.
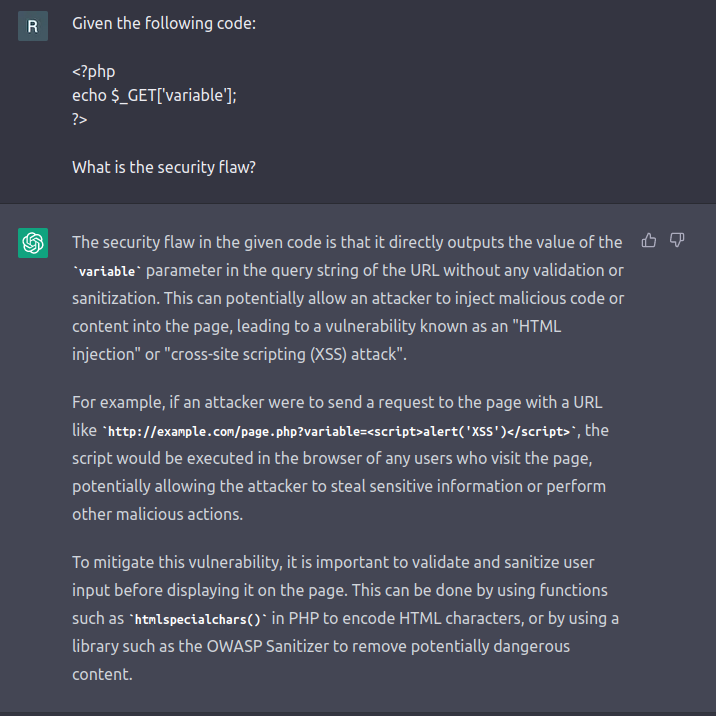
The catch here is that I knew the answer to the question I was asking. This should serve as a warning to users to not seek out new knowledge through AI, as the answers may be misleading. Instead use AI engines to enhance, augment or improve upon your existing knowledge and experience.
The ugly
As a bit of fun, I asked ChatGPT for some jokes about WordPress security.
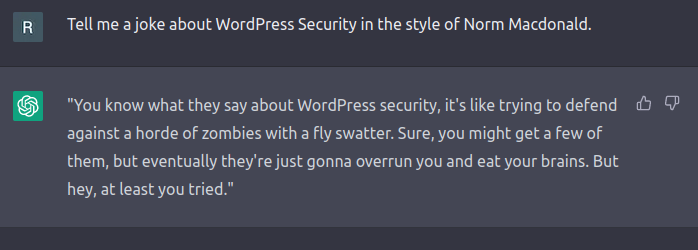
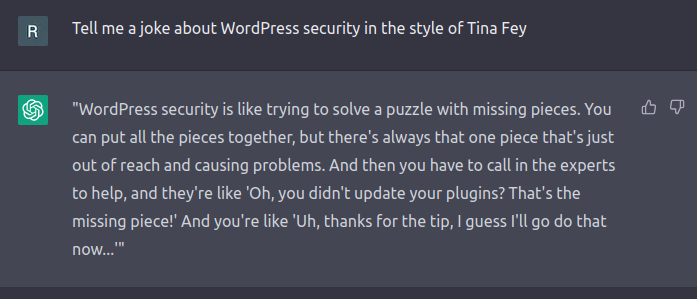
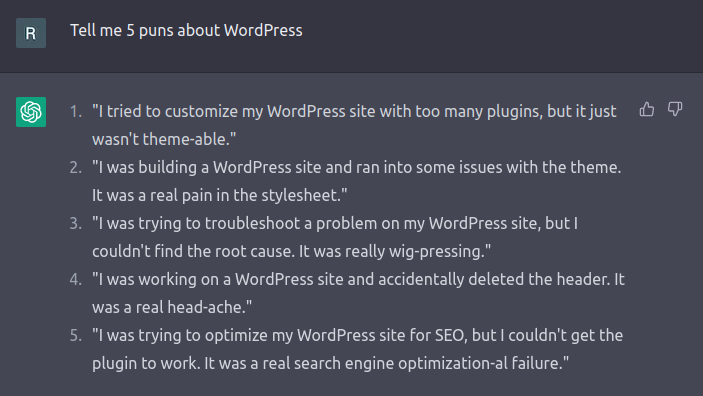
While ChatGPT has some good advice, unfortunately, it falls flat as a comedian. Perhaps comedy is too complex of a task to ask from an AI chatbot.
So, if you find yourself worried your job might be replaced by an AI chatbot (hint: it won't), then maybe a career in stand-up may be a safe backup plan.
Vulnerability roundup
This week's vulnerability roundup will be about many more unpatched security bugs. The biggest of which is an unpatched security bug affecting WordPress core which was published by Sonarsource a few months ago.
WordPress's Unpatched SSRF Bug
Reviewing SonarSource's write-up, here are a few key details:
The bug cannot easily lead to an exploited WordPress website. Attackers need to control the DNS server the web server is configured to use in order to exploit this bug.
In scenarios where a site is vulnerable, the impact is limited. This is after all an SSRF bug, which I've written about before in Patchstack Weekly #33, What is SSRF?. You may recall in that episode, SSRF could lead to internal servers being targeted. With this in mind, we should consider that if the attacker already has control over DNS servers, then things are already much worse than SSRF for the organization.
I would not be terribly worried about this specific security bug, but I will still look forward to the WordPress core security team pushing a patch.
Unpatched plugin security bugs
WordPress core was not the only project affected by unpatched security bugs this week. In total 14 unpatched security bugs were published in 9 unique plugins.
- wp-autosearch - Unauthenticated SQLi
- cryptocurrency-widgets-pack - Unauthenticated SQLi
- letsrecover-woocommerce-abandoned-cart - Unauthenticated SQLi
- letsrecover-woocommerce-abandoned-cart - Authenticated SQLi 1
- letsrecover-woocommerce-abandoned-cart - Authenticated SQLi 2
- wp-rss-by-publishers - Authenticated SQLi 1
- wp-rss-by-publishers - Authenticated SQLi 2
- wp-rss-by-publishers - Authenticated SQLi 3
- web-invoice - Authenticated SQLi 1
- web-invoice - Authenticated SQLi 2
- launchpad-by-obox - CSRF
- gs-instagram-portfolio - CSRF
- sunshine-photo-cart - Unauthenticated XSS
- wp-table-reloaded - Authenticated XSS
Of the above list, the most serious unpatched security bugs are the unauthenticated ones affecting wp-autosearch, cryptocurrency-widgets-pack, letsrecover-woocommerce, and sunshine-photo-cart.
I hope the developers of these plugins find the time to write and push a patch soon.
Thanks and appreciation
This week's thanks goes out to the developers of ChatGPT, OpenAI and the whole team behind this project. It was amazing working with this tool.
A special thank you goes out to Sonarsource for finding and reporting the bug in WordPress core. Even though this went un-patched, I appreciate your efforts and understand why you published the details publicly after 5 years of it going unaddressed.
I will be back in 2023 with more security tips, tricks, opinions and news on the Patchstack Weekly Security Update!





