This blog post focuses on giving you information about how to test WordPress plugin security with a checklist of tasks. It also explains if all the plugins you find from the WordPress plugin repository are safe or not.
Right now, you have access to over 58,000 plugins on WordPress, and each one is approved by the plugin review team at WordPress when it is approved and added to the repository.
The team not only ensures that the plugin works as it is intended to, but also that it follows WordPress’s security guidelines.
However, not even the most efficient review team can test WordPress plugin security and ensure that all plugins on a platform are safe. It’s true for Apple’s App Store. It’s also true for the Google Play Store. And it’s true for WordPress plugins.
In addition, WordPress—like Android—is an open-source platform. This means WordPress’s success as a CMS hinges on how popular it is with individual developers.

There isn’t one team creating the thousands of themes and plugins you see on WordPress. Those are all built by developers because they see value in making a service available to WordPress users.
It’s an ecosystem that works, incredibly well. WordPress is, by far, the most popular content management system (CMS) in the world.
It’s estimated that 40 percent of all websites in the world run on WordPress. In fact, the CMS is so good that almost 40 percent of the top one million sites in the world use WordPress.
How do vulnerabilities end up in WordPress plugins?
An open-source platform comes with its share of issues. Not all plugins and themes are built as securely as they should be. It depends on how good a developer is at the job.
There is usually no malicious intent in security lapses, but hackers have also been known to use plugins for their activities.
SI CAPTCHA is an example of what can go wrong with WordPress plugins. It was a legitimate anti-spam solution with over 300,000 installs when it was banned from the platform.
A hacker bought the application from the developer, then added code that would inject spam ads on websites that had installed SI CAPTCHA.

The developer confirmed that it was part of a coordinated spam campaign with other plugins also targeted similarly. While the plugin cleared security requirements as a legitimate service for some time, a hacker was able to update it to have vulnerabilities.
Such incidents show how vulnerable plugins can impact websites, and you might not even be aware of them for a long time. It’s so common that estimates show 98% of WordPress vulnerabilities are related to plugins.
How to test WordPress plugin security?
Not all instances with vulnerable plugins are as the example above. The vulnerabilities usually end up in the plugins after updates. With updates, the developers can unknowingly create new pieces of code that have a vulnerability.
This is something the WordPress plugin review team cannot know since the plugins are checked only when they are first added to the WordPress plugin repository.

There’s no fool-proof way to know if a plugin or a theme is compromised, but it’s not as ominous as it sounds. You can avoid the obvious ones by looking for some of the more common signs.
PS! You don’t need to be a professional web developer to go through this checklist, but if you have any questions about plugin vulnerabilities and protecting your sites from plugin vulnerabilities to prevent malware infections and more – you can contact us via our live support on our website.
1. You can’t pin down the developer
You are most likely to search the WordPress plugins repository when you want a plugin. It’s also the safest option. Unfortunately, it’s not the most user-friendly search engine.
Now, if you don’t find it there, a quick search on Google (or another search engine of your choice) will usually reveal a plugin that serves the purpose you want.
However, Google will show you plugins outside of the repository as well. These are likely to be listed by WordPress developers on their own websites.
Good WordPress developers have websites, and that’s okay. But if you come across a developer promising a lot for free or very cheap, be cautious.
If you can’t find the developer in the plugins repository, you can try a third-party marketplace like CodeCanyon. These marketplaces have software for multiple CMSes. See if the developer has other products listed.

Good developers are consistent and try to build brand value across platforms. They might have only one plugin listed in the WordPress repository while being active in other marketplaces.
If you find any products, to test WordPress plugin security, you should check for ratings and reviews. Check what the latest reviewers have to say about the product.
It’s best to stay away from new developers without a track record. Go one step further and do a bit of research on the developer if you’re really interested in the product. Try to get in touch and see where that goes.
The WordPress developer community is pretty active and a suspicious developer is likely to have been flagged at some point.
2. The plugin is not very popular
If the feature you want is unique in some way, it’s possible the plugin won’t have too many takers on the market. This won’t happen a lot though. With over 27 million WordPress websites active, it’s unlikely that you will find yourself alone in needing a specific application or solution.
If a plugin for a common feature does not have enough downloads, it’s best to avoid it. This might sound counterintuitive as all great plugins started with a handful of subscribers. Well, a plugin that’s been around for months or years with few installs is always a tough sell.
If it’s a new listing, you should consider waiting a bit to observe how early adopters or security researchers react to it. It could be a great plugin, but wait until it has at least 1 000 active installations.

In WordPress, you can see the exact number of websites running the plugin right now. If that number stays steady or grows fast, it’s likely that the product is good and no suspicious activity has been found.
3. It doesn’t work with the latest WordPress version
WordPress puts great value on compatibility with version updates. All plugins need to be compatible with the latest version, or the marketplace “devalues” it.
This means users cannot find it when searching for it. The “tested up to” value lets you know the last version on which the plugin worked well. WordPress requires this value to be at least the last stable version available.
It’s good practice for you to keep your website updated as well. Older versions of WordPress can leave you vulnerable. New versions often fix vulnerabilities while adding new features.
According to WordPress, only 37.5 percent of users have updated to version 5.5, their latest. At least 79.2 percent have updated to version 5 or newer. That still leaves millions of websites running older versions.

If you find a plugin outside of the marketplace and it’s incompatible with the current version of the CMS, do not choose it. You can be assured that there will be a similar plugin that’s updated to work with the latest version.
4. There are no updates or support
The two might sound similar but are two separate things. Just like WordPress core, you must always keep your plugins and themes updated to the latest version.
It might change how you’ve set up your website, but an outdated version of a plugin could have security issues as updates sometimes have important security fixes.
WordPress tells you when a plugin was last updated. If it was over six months ago, that’s a bad sign. It might mean that the developer has lost interest in the application and will no longer keep improving the plugin.

These orphaned plugins could have vulnerabilities that the developer is no longer working on.
The second, support, shows how active a developer is in responding to any problems you face while using the plugin. Everyone uses a different set of plugins and themes, and the applications can interfere with each other.
A good developer is willing to engage with users and find solutions, especially if it’s a security concern.
Each plugin will have a “support” tab that’s open for everyone to read through. Look through the topics and see how the developer has responded and resolved issues. Avoid the plugin if the developer has been unresponsive or has been unable to solve problems. In any case, ratings are usually poor if developers don’t work with users.
5. Keep up with security updates and news
In the open-source world of WordPress, news of a vulnerability in a plugin become common knowledge pretty fast. It’s a good idea to test WordPress plugin security updates every once in a while.
Security companies like Patchstack keep a tab on what’s happening and publish updates almost every day.
If hackers can exploit the vulnerability before a patch is released, anyone who installed the plugin is at risk. You should probably uninstall the plugin until the developer confirms that the issue has been resolved.
Apart from such reports, a web host might also have a list of banned plugins. Some of these will be for technical reasons because they already provide the same features or the extensions are not supported on the platform. Not always though.
For example, GoDaddy’s list has plugins blacklisted for both security and inactivity. The latest list has two plugins, ‘Real-time Find and Replace’ and ‘NextGEN Gallery’, blacklisted for security reasons. This list even has a few plugins blocked because of performance issues.
At the least, you need to do a basic search—plugin name + hacked or vulnerability—before installation. If you get any credible results, do a more thorough check and ensure that the plugin is safe to install right now.
How to find a reliable security tool for WordPress?
There is no website that is and will always be invulnerable. You can choose to keep it simple and use only a handful of necessary plugins that are unlikely to be hacked. But if get hacked, choose a service that focuses on preventing malware infections in the first place.
Then follow the plan because WordPress security does not have a one-time solution.

When you’re ready to expand the scope of your website, which usually means adding more features, you need professional help. Patchstack is a managed service that keeps monitoring and assessing risk.
It’s also a good idea to choose one platform that provides multiple solutions, rather than loading your website with a number of single-solution security plugins.
How can Patchstack help to protect your WordPress sites?
Patchstack will help you with automated WordPress security patches and vulnerability monitoring. It means that with Patchstack you can instantly detect vulnerabilities within WordPress plugins, themes, and core.
Missing just a single vulnerability can quickly result in a hacked website when it comes to plugins. Trying to manually stay up to date can be an impossible job as well. With Patchstack you can stay updated and safe because Patchstack will let you know if you have any vulnerable plugins on your site.
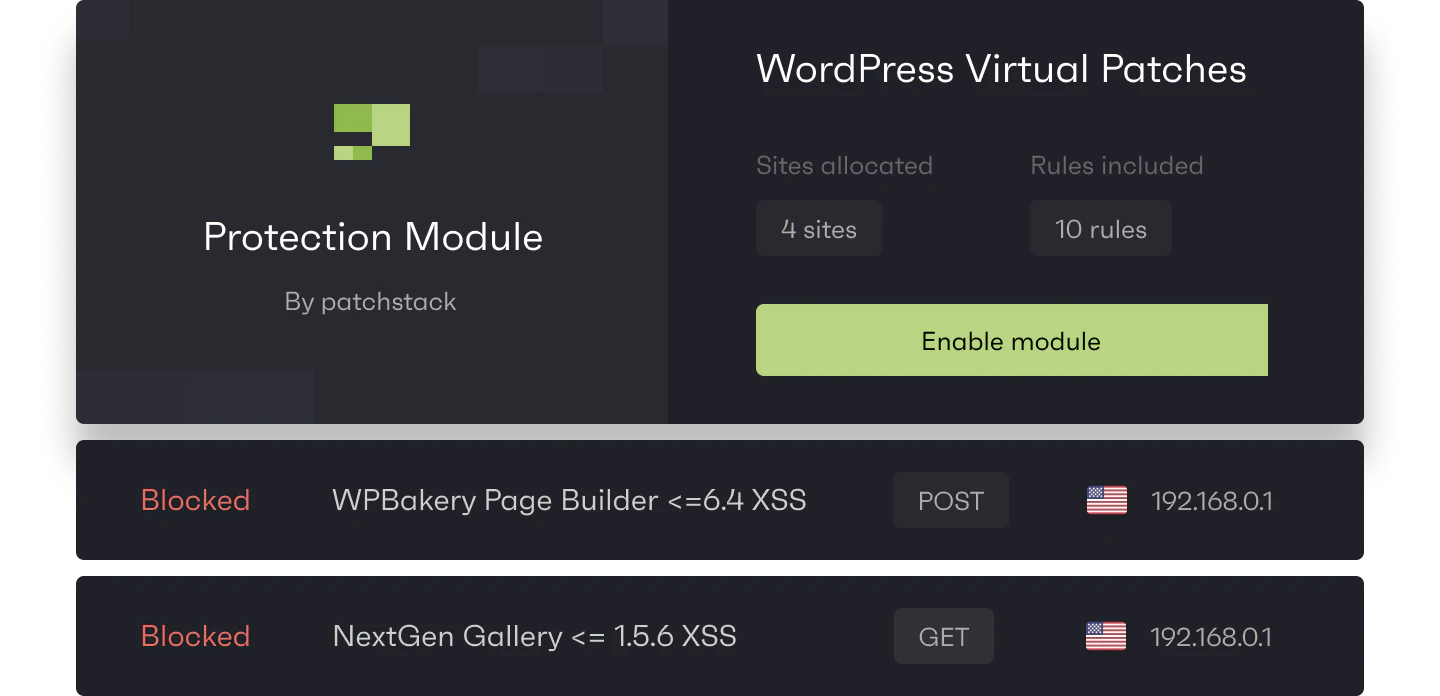
The second thing you need is a quick response when a vulnerability in the plugin you use does not have a security fix or update from a plugin developer. It often takes just hours before bots try to abuse new vulnerabilities.
Patchsack Alliance checks vulnerabilities in plugins and themes daily and when a vulnerability is found, the Patchstack team sends vPatches to the Patchstack firewall engine to make sure sites are safe even before the plugin developer can start working with a patch.
With Patchstack you will receive automatic vPatches for new WordPress vulnerabilities, additional security modules to filter unwanted traffic, and can apply custom security rules. Most importantly you can prevent malware infections and save on malware removal costs.





