UPDATE: We want to thank ThemeForest for reacting swiftly to our report, and for removing the vulnerable premium theme mentioned here from their marketplace.
Recently a friend of mine asked me to set up a WordPress site for her using a premium WordPress theme she had bought - I quickly found the theme came with some severe security issues right out of the box.
Using that example, this article will dive into the risk of pre-made bundled themes. Such themes may hide serious security vulnerabilities within them that won't be obvious to the casual user.
Many people who want to build a website, but are not developers or designers look into pre-made themes, which are being sold in different marketplaces. Such themes are often very specifically designed for a single purpose, such as a design for a bakery, festival, news site, etc. They require only the basic setup and copy changes to get a live page going.
Unfortunately, these pre-made themes often come with a hidden risk. Given that the customers of such pre-made themes are less technical than the average WordPress user, it’s safe to assume the majority of them are not aware of any risk at all.
We'll dive into the case study in a bit, but first, some context.
Background: the problematic practice of bundling plugins with themes
This problem has existed in the WordPress ecosystem since the concept of premium themes was born. Back in the day, WordPress themes were a big business - you didn't have drag-and-drop page builders (like Elementor) that make it easy to put together a well-designed website.
Back then, you either had to dive into HTML/CSS and build your own theme, or you purchased a theme from someone who knew how to build one. Buying a pre-made theme was considered the cheapest option to get a site running.
Exactly like you would install plugins today to add forms or incorporate a fancy slider - the developers back then also used different plugins to complete the design and functionality of the theme they were selling.
The Great Revolution Slider Hack of 2014
Most of the themes come with additional functionality that completes the design. A good example of a design functionality is slider plugins (e.g. Revolution Slider) - but you also need other functionality such as forms, SEO performance modifications, and so on.
Many premium themes relied (and still do) on a plugin called Revolution Slider (A.K.A. RevSlider) which gives a lot of cool functionality to help design the main hero slider element for your website.
In 2014, hackers found a LFI (local file inclusion) vulnerability in the Revolution Slider plugin, which allowed any un-authenticated user to download the site's wp-config.php file, which was then used to exploit a second vulnerability in the Revolution Slider plugin to upload a backdoor to gain full control over the website.
This resulted in a mass-exploitation campaign, where hackers automated attacks against every website they found online (regardless if they used Revolution Slider or not) to gain backdoor access to as many websites possible.
Even though it was impossible to get a clear picture of how many websites had the Revolution Slider plugin installed, the security community quickly realized the scale of the issue by looking at the premium themes being sold where Revolution Slider was being preinstalled.
Hundreds of thousands of websites were hacked, and Envato eventually made a statement confirming over 1,000 premium themes had Revolution Slider bundled in. Since the incident, Envato has also improved its guidelines which now prohibit theme developers from bundling plugins.
Case study: How to get hacked out of the box
This entire article was inspired by a personal experience that happened in early September 2023. A friend who was about to set up a WordPress site had chosen a theme that was purpose-built for an event she was hosting.
I was asked to help set up the WordPress site and install the premium theme that had already been purchased. The theme itself looked very promising and was even marked as “recently updated” in ThemeForest.
After installing the theme .zip file I was presented with an error, asking me to install the required plugins. Like so:
The theme installation process sent me to an “Install Required Plugins” page, where you need to install the plugins that are required for the theme to work. It asked me to install 8 plugins in total - 4 from the official WordPress.org plugin repository, and the other 4 were pre-packaged.
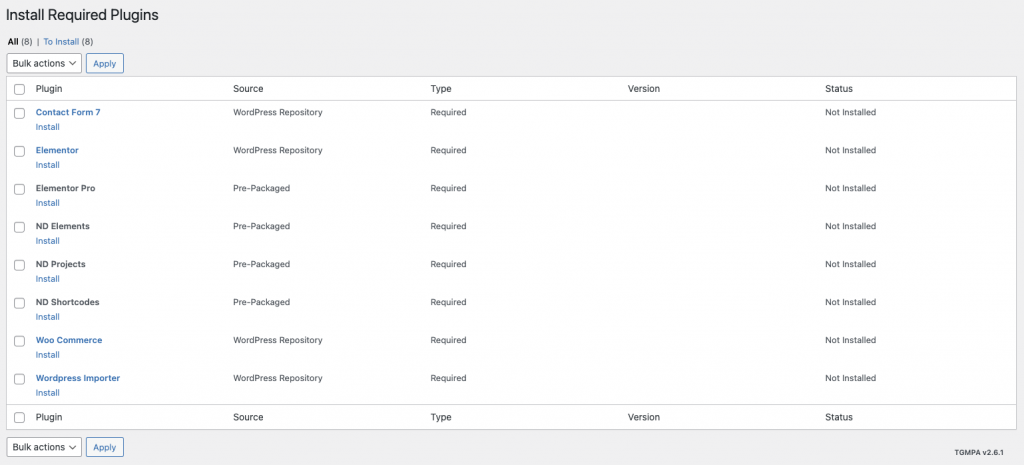
After all of the required plugins were activated, I connected the website to Patchstack to check the brand new site for security issues
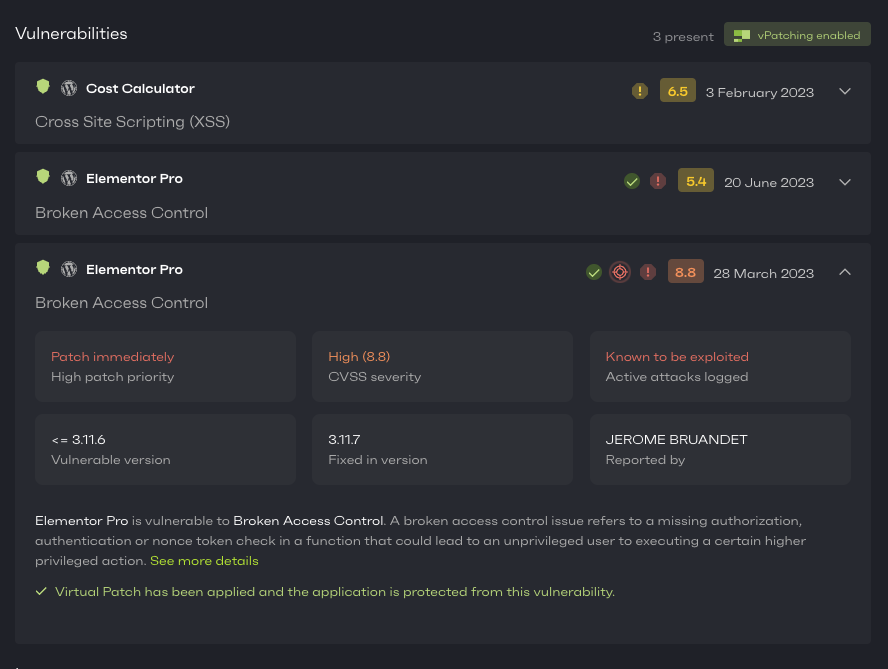
Lo and behold, here’s what Patchstack reported back:
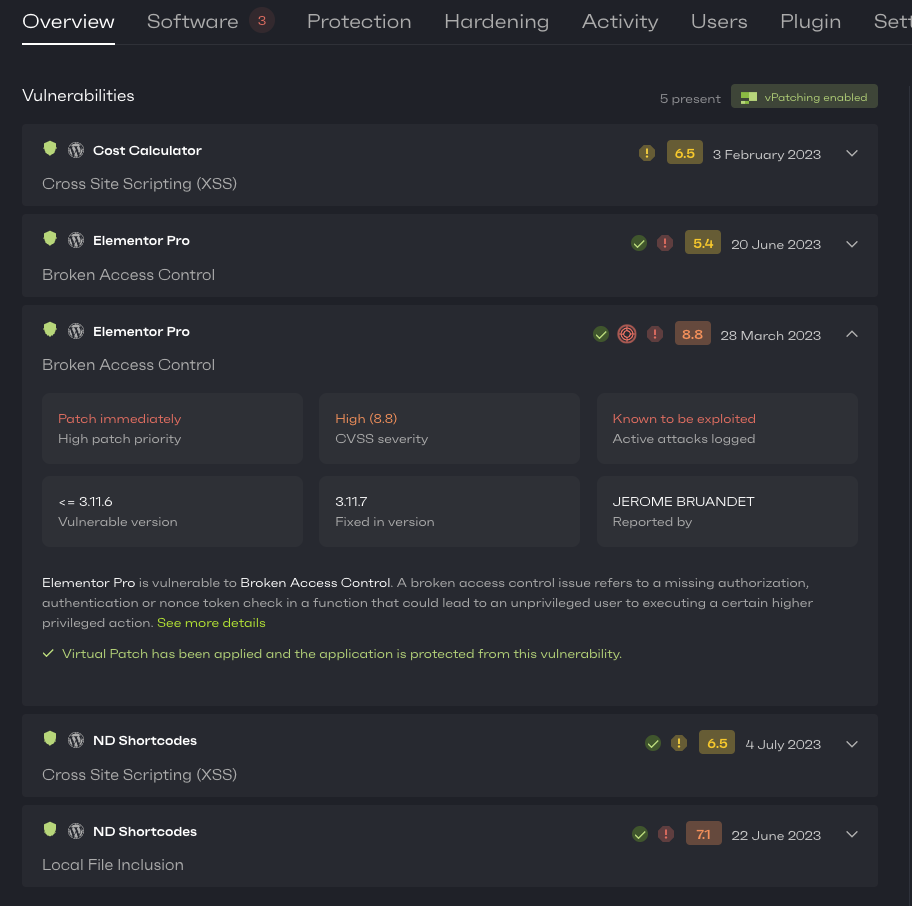
Out of the box, the website came with 5 different security vulnerabilities - 3 of which were high-priority issues and one of them is even known to be actively mass-exploited.
As seen in the screenshot above, the most critical vulnerability that is marked as actively mass-exploited did have a fixed version available. So I checked if I could update the plugins:
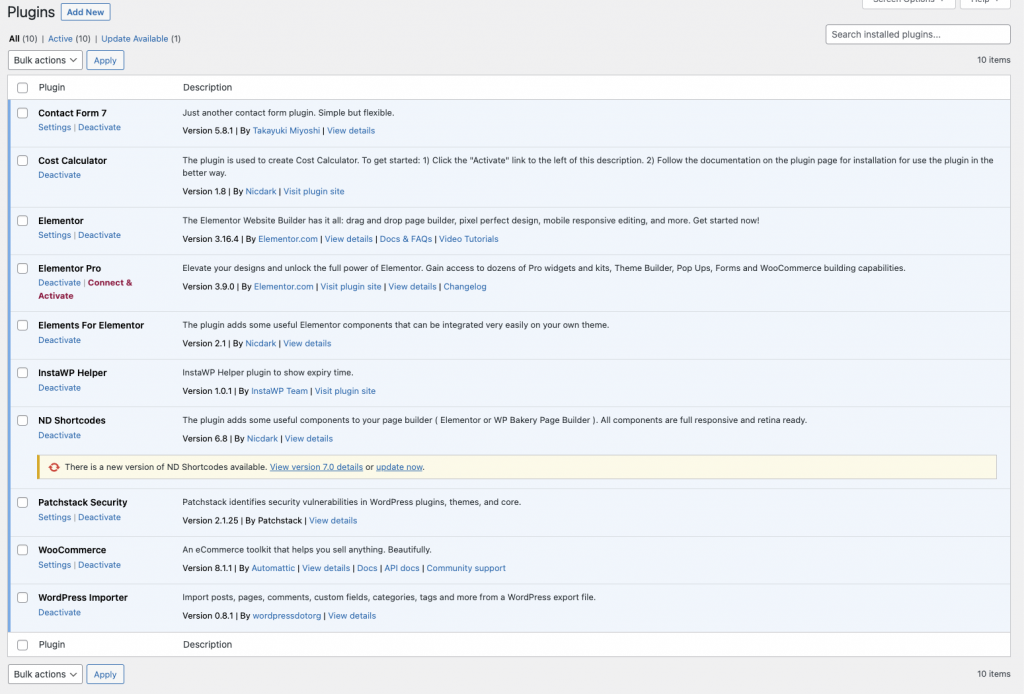
Interestingly, there was only one update available. But for the starters, I installed that to check if that fixed any of the vulnerabilities - it did some.
As for the other plugins, it looked like everything was up-to-date.
Yet, we were still left with 3 other vulnerabilities, including the mass-exploited one.
And this here is a perfect example of one of the biggest security risks in WordPress - a false sense of security from seemingly up-to-date plugins, that in reality may contain unpatched issues.
If you're looking at your admin panel it would appear that your site is nicely up-to-date. Instead, a site in this state would probably be hacked within a week.
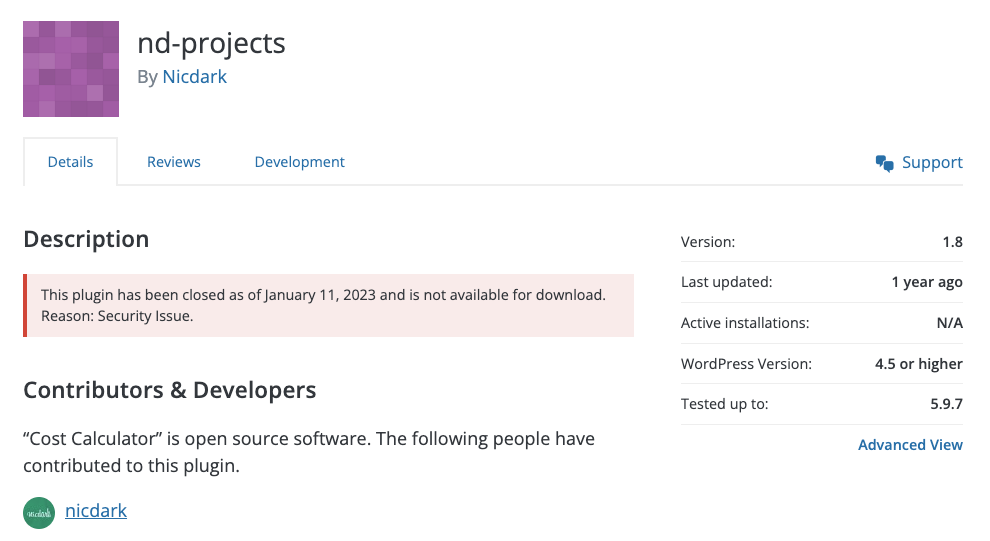
On my friend's site, there was nothing I could do with the Cross Site Scripting vulnerability in the Cost Calculator Plugin. Of course, Patchstack had automatically applied a vPatch on it so it couldn’t be exploited, but there was no other way to solve the issue as the plugin had never released a fix for it. In fact, the plugin had even been removed from the WordPress.org plugin repository since January 2023.
The only option we had here was to delete the plugin and hope that the theme would keep working (even with Patchstack's protection, it's just a bad security practice to leave vulnerable plugins running on your site!)
Now, to the most serious security issue, which was the Elementor Pro broken access control vulnerability - the one known to be actively mass-exploited. This vulnerability itself was actually fixed by the Elementor team quite a while ago (as was the other remaining vulnerability).
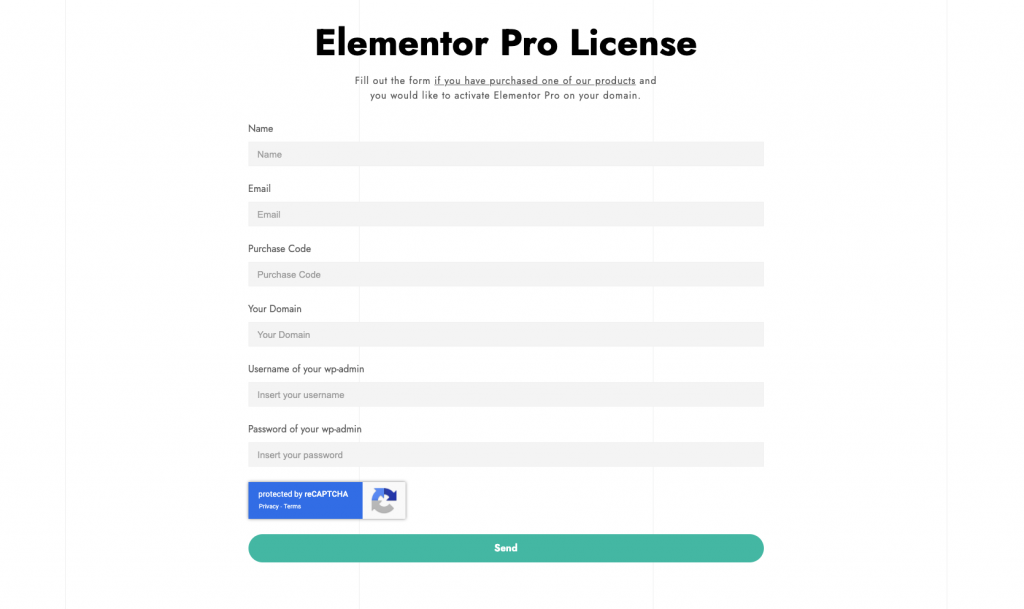
However, the theme was using a very old version of Elementor Pro, and since it didn't come with the actual licence there was no possibility to download a newer, safer version!
The only option was to either delete the Elementor Pro plugin or spend additional money and purchase the Elementor Pro license.
The theme developer did offer a free license to Elementor Pro, but he also stated that “Elementor PRO it is not mandatory for use the theme that you have purchased and you are free to not request it”. So probably most of the customers who have purchased this theme never bothered with the license. Especially because to get it, the theme designer asked for your WordPress admin panel username and password - which you should never share with someone else!
In the end, I purchased the Elementor Pro license for the friend, and we were able to get rid all of the vulnerabilities on the site - but I doubt this is the case with the majority of the customers (over 2,500 of them) who also bought the same theme.
How to prevent cases like this one?
Before you purchase premium themes, ask the designer which plugins are required for it to work. Also make sure you get the required licenses for all of the required plugins, so you will receive all the important updates. And of course, make sure to keep the plugins updated!
Also, set up vulnerability monitoring in Patchstack and receive real-time alerts when a new vulnerability is found in any of the plugins/themes that you have installed.
You can also turn on protection modules, so the website receives a vPatch for the vulnerability, giving you time to update or choose what to do next, without leaving the website exposed to the hackers.
I also want to thank the Envato team who reached out to the specific theme developer and this theme is currently removed from the ThemeForest marketplace. The representative from Envato also told us that the pre-packaging the plugins with themes on such way is against the guidelines, and required plugins should only be downloaded from the official WordPress.org plugin directory.
The lack of visibility into premium plugins
Premium plugins and themes often don’t follow the common WordPress best practices. The updating process is often as not straightforward as it is with plugins you install directly from the official WordPress.org plugin repository, and their source code is not open to the public.
Because of this, premium plugins miss out on a big benefit of open-source - namely that anyone can read the code, propose improvements and point out any issues or problems that should be fixed. This is one of the reasons open-source code is usually more secure, as more people have looked into it and potential vulnerabilities get fixed.
This is not the case with premium plugins. Even though most premium plugins are also GPL or have dual-license, the source code is not made public. This means that it’s much harder to keep an eye on updates for the plugin, and there is no benefit from community-driven security oversight.
Based on our experience as the leading vulnerability processor in the WordPress ecosystem, even today the security vulnerabilities are much more severe in the premium plugins compared to the ones that are on the official WordPress.org plugins repository.
Stay safe!





