Welcome back to the Patchstack Weekly security update! This update is for week 11 of 2022. This week is all about plugin vulnerabilities and the State of WordPress Security 2021 whitepaper.
There is some big news this week, but really I should say last week. Patchstack released our State of WordPress Security Whitepaper for 2021 on March 9th or last Wednesday.
I will be giving a short summary of some high points in this week's knowledge share, but if you would like to read the whole thing you can view it on patchstack.com for free, no email or registration is required.
Before I talk about WordPress security from 2021 … I need to tell you about this week's vulnerability news, which includes a WordPress core security release (5.9.2) and five WordPress plugins that patched high-risk security bugs in them in the last week. Emphasis on high risk too, they require no authentication for an attack to be successful.
Vulnerability news
WordPress 5.9.2 Security Maintenance Release
Late Thursday evening (or early Friday morning depending on where you're at) the WordPress core team released version 5.9.2. This release addresses 1 maintenance bug and 3 security bugs.
Details are light on the security bugs at this time, but it appears that they are related to either Prototype Poisoning (a Javascript attack) or Cross-Site Scripting.
I checked the WordPress core file diffs and did not see any obvious issue, so these patches may be related to updating libraries WordPress core is including, like the Gutenberg block editor. This strongly implies authentication (likely author or editor or higher) would be required to perform the attacks, but I am unsure.
There are, unfortunately, no official CVEs or details at this time so security reviewers are having to put in extra work to find out details, and the timing caught a lot of people by surprise.
Ninja Forms File Uploads Extension premium plugin <= 3.3.0 - Unauthenticated Arbitrary File Upload
The developers of the premium plugin Ninja Forms File Uploads Extension released a patch for a serious security bug this week.
Sites with the File Upload Extension added to Ninja Forms were at risk to allow anyone to upload any file to the website. Site owners should make sure they patch this premium extension for the popular Ninja Forms plugin ASAP.
Church Admin plugin <= 3.4.134 - Unauthenticated Plugin Backup Disclosure

The Church Admin plugin developers patched a bug that could have led to sensitive information being disclosed to unauthenticated visitors.
This plugin may not have the biggest installation base, but looking at how frequent there are updates to the code, I can tell the developers behind the Church Admin plugin are great stewards of their code! Update your sites, and feel confident these developers are active and committed to providing their users regular updates.
The remaining high risk vulnerabilities of the week
Finally, to round out the remaining high-risk vulnerabilities of the week, we have 3 plugins that patched unauthenticated SQL injection vulnerabilities in this in the last week. If you're using the following plugins, please be sure to update ASAP.
- SpeakOut! Email Petitions plugin <= 2.14.14 - Unauthenticated SQL Injection (SQLi) vulnerability
- Stop Bad Bots plugin <= 6.87 - Unauthenticated SQL Injection (SQLi) vulnerability
- Title Experiments Free plugin <= 9.0 - Unauthenticated SQL Injection (SQLi) vulnerability
That is all for this week's vulnerability highlights, now let's talk about 2021 and I will share some highlights from Patchstack's yearly whitepaper in this week's knowledge share.
Weekly knowledge
The State of WordPress Security 2021
Patchstack has been busy for the last few months preparing the State of WordPress Security Whitepaper for 2021. We put months of effort into talking with site owners, reviewing vulnerability data added to the Patchstack database, and reflecting on the many bugs reported and how they were handled through the Patchstack Alliance.
In the end, we compiled a year's worth of knowledge into a single document which you can download and review from here.
But first, how about I share some highlights on some of the more surprising things even Patchstack learned when putting this document together:
- 29% of plugins with critical vulnerabilities, received no public patch.
This was by far the most concerning finding. In total, nine plugins with critical security bugs (we're talking full site compromise, no authentication required) were removed from their respective repositories due to the developers not addressing these bugs.

- 2021 saw a 150% rise in security bugs reported in the WordPress ecosystem.
More security bugs being reported means more security bugs are getting patched. Patchstack started the Patchstack Alliance in 2021, and this attracted more security researchers to pay attention to reporting securtity bugs in the WordPress ecosystem. - Security defense budgets are extremely low.
We surveyed website owners, agencies and freelance developers and on average nearly a third have zero dedicated security budget, another third spend only up to $3 per month on security services.
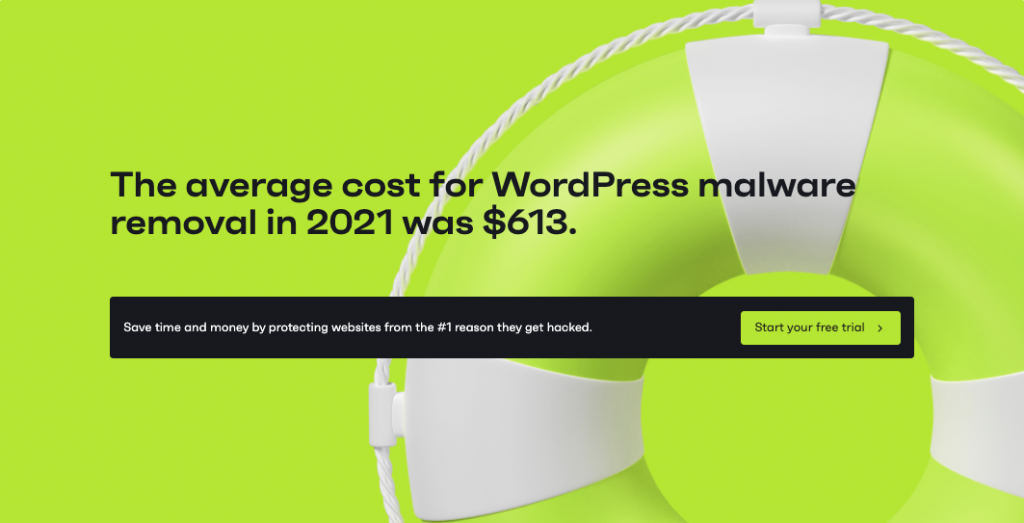
We all know what happens when preventative security doesn't get a budget too, so how much on average was a clean-up after a compromise?
- $613 was the average cost of post-compromise cleanup.
Site owners who had to deal with getting compromised spent over $600 on average, and in some cases it cost thousands of dollars to address malware removal, website cleanup and incident response.
- WordPress core had 4 security releases.
WordPress core continues to show WordPress itself is secure. With the only critical bug found in the software, being a bug in a library not WordPress core itself. Back porting security releases, and providing regular and timely security patches for bugs reported through their own vulnerability disclosure process. - WordPress plugins had 35 critical security bugs reported in them.
35 security bugs were reported in 31 different WordPress plugins. This is on average one security bug every other week in 2021, highlighting the importance of keeping tabs on WordPress plugin security releases for site owners, agencies, and hosting providers. - There were 55 critical security bugs affecting themes in 2021.
Dividing this by 52, averaged out this means every week you could expected to see a new critical security bug was being reported in WordPress themes. In reality, a lot of these bugs were reported toward the end of the year and this is another reminder to make sure you're monitoring all of the code your site(s) are utilizing (including the theme) for security vulnerabilities.
Thanks and appreciation
This week's thanks go out to the Plugin developers who pushed those security bug patches this week. Thank you to the developers of Ninja Forms File Upload Extension, Church Admin, Speakout email petitions, Stop bad bots, and Title Experiments Free. We owe you a debt of gratitude for pushing those security patches and securing your user's websites. Let me not forget the WordPress core developers who worked on release 5.9.2 as well.
A big thank you is owed to the hard-working team at Patchstack as well. I know firsthand how much effort went into researching and compiling data for the State of WordPress Security 2021 Whitepaper, and I believe we uncovered some important issues in a concise and easily readable format.
If you are interested in reading more, please check it out here: State of WordPress Security Whitepaper.
I will be back next week with more security tips, tricks, opinions, and news on the Patchstack Weekly security update!