In the dynamic world of web hosting, the foundation of your WordPress website's security lies in the choice of your hosting provider.
When it comes to your WordPress site, security isn't merely an option – it's an absolute necessity. A secure web hosting environment forms the bedrock of your site's defense against an ever-evolving landscape of cyber threats. It's the digital moat that protects your valuable content, sensitive data, and online presence from malicious actors.
We understand that the vast array of hosting options can be overwhelming, which is why we've crafted this guide to demystify the process.
At Patchstack, we don't just talk about security – we live and breathe it. Your website's security is our top priority, and we're dedicated to ensuring that you have the knowledge and resources to make the right choice.
We're proud to be partnered with some of the industry's most reputable hosting companies, all of whom share our unwavering commitment to WordPress security. These partnerships allow us to bring you the best recommendations and insights into hosting providers that prioritize your website's safety.
Keep reading to know more!
What Makes a Web Hosting Secure?
A hosting environment that is specifically designed and configured to safeguard WordPress websites from various online threats and vulnerabilities should protect your sites against unauthorized access, data breaches, malware infections, and other security risks that can compromise the integrity and functionality of a WordPress site.
Secure web hosting for WordPress typically comes with:
- Server Hardening: Implementing stringent security measures at the server level to prevent unauthorized access and mitigate potential risks.
- Regular Updates: Ensuring that server software, including the operating system and server applications, is kept up to date with security patches.
- Firewalls: Deploying firewalls to filter out malicious traffic and protect against common web application attacks.
- Malware Scanning and Removal: Conducting regular scans for malware and offering tools to remove any detected threats.
- Backup Solutions: Providing automated backup options to enable website owners to restore their sites in case of data loss or security incidents.
- SSL Certificates: Offering secure sockets layer (SSL) certificates to encrypt data transmission between the server and website visitors, enhancing data security.
Significance of Hosting Companies
The pivotal role played by hosting companies in ensuring the security of websites cannot be overstated. Hosting providers undertake a multifaceted approach to enhance website security:
- Infrastructure and Network Security: Hosting companies need to meticulously maintain secure server infrastructure and networks. This care greatly mitigates the risk of unauthorized access and data breaches.
- Security Patching: Hosting companies prioritize regular updates for server software and the application of security patches. This proactive measure is vital for addressing known vulnerabilities and strengthening defenses against emerging threats.
- Customer Support: Hosting companies extend responsive customer support to assist website owners in addressing security concerns and incidents. This support network is invaluable for promptly resolving issues and maintaining the integrity of websites.
- Server Maintenance: Hosting companies ensure that routine server maintenance tasks are performed without compromising security. This includes configuring server settings securely and isolating websites from one another, preventing cross-site vulnerabilities.
The significance of these security measures cannot be understated for website owners, with the hosting companies playing a pivotal role in maintaining the security of the hosting infrastructure, and assisting website owners in securing their WordPress sites.
Recent events have underscored the critical importance of robust security measures. For instance, consider the case of a recent ransomware attack on a prominent cloud provider, CloudNordic. This attack, which occurred on August 18, resulted in the complete encryption of CloudNordic's servers, effectively paralyzing their operations. The malefactors behind the attack also wiped out both the company's and customers' websites and email systems. Despite ongoing efforts by CloudNordic's IT team and third-party responders to restore data, even backup systems were compromised.
In response to the extortion demands of the attackers, CloudNordic chose to uphold its principles and refused to pay a ransom to retrieve the information and systems. This incident serves as a stark reminder of the need for robust security measures, and hosting companies' dedication to security is paramount in safeguarding against such threats.
What to Look for When Choosing Secure Web Hosting
To ensure your website's security, here's a checklist of key factors you should consider:
1. HTTPS Availability
In today's digital landscape, HTTPS is no longer a luxury but a necessity. Most hosting providers offer free HTTPS, thanks to initiatives such as Let's Encrypt and ZeroSSL, which provide free TLS certificates.
To check if your website has HTTPS enabled, simply type "https://" followed by your domain name in your browser. If you see a lock icon (or a Tune icon in newer versions of Chrome), then you're good to go. If not, explore how to set up HTTPS with your hosting provider.
2. Backup and Restoration
Backups are your safety net in case of emergencies. However, it's crucial to not only rely on them – but also test their functionality. Reach out to your hosting provider to understand their backup and restoration process.
If possible, perform a test run – but do avoid overwriting your live site! This proactive approach ensures your backups are reliable when you need them the most.
3. Keeping Software Updated
We all know the importance of regularly updating a WordPress website, as well as our laptop or PC’s operating system. But web servers have operating systems too – and they also need regular updating.
Luckily, WordPress allows you to confirm the versions of the software it relies on. Simply log in to your WordPress admin panel, open Tools, and Site Health. From the Site Health page you will get a list of details – including server versions, if you click on the “Info” tab, then expand the “Server” section.
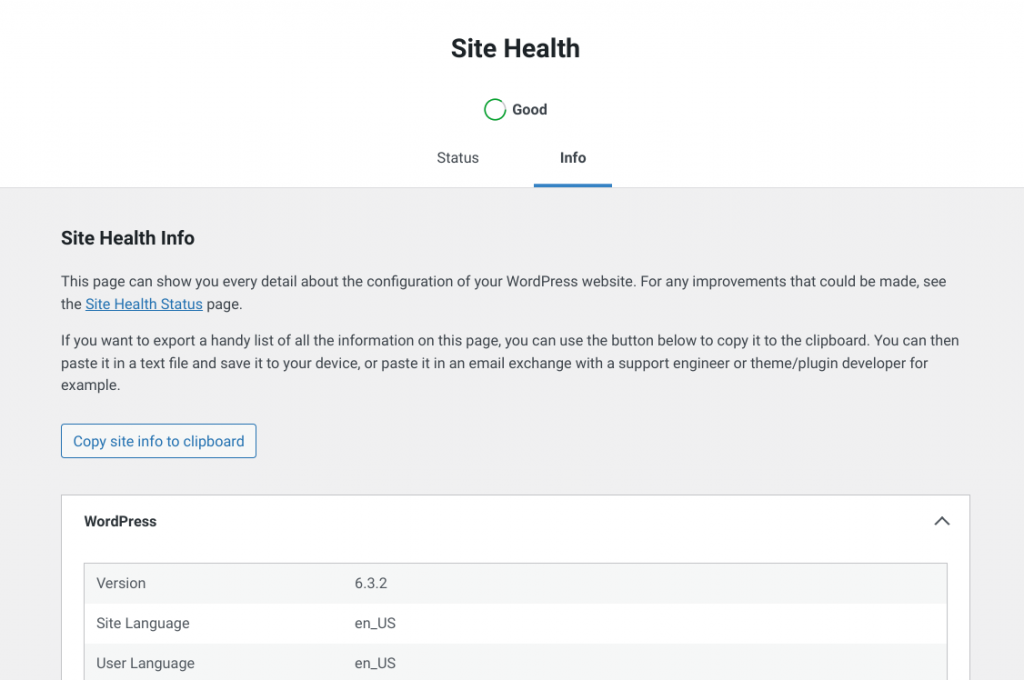
The server section has information about software versions of PHP, Web Server, and more. Alternatively, you can expand the “Database” section to find out the server and software version for your database server as well.
You will need to do a little manual verification to find out if these components are still supported by their respective software vendors, but it is worth the time and effort.
If you find a software version is out of date or unsupported – don’t panic. Simply reach out to the hosting provider’s support team to ask them about it. You may be able to easily upgrade, or they may inform you the package is “backported” – which means someone did apply the security patches needed, but it still reports an old version number.
4. Brute Force Protection
An analysis by Google Cloud shows that Brute-force attacks are the most common threat for cloud service providers. This type of attack doesn’t require any skill and it can be automated easily; this is why almost half of all attacks on websites are brute force attacks. We have covered brute-force attacks on WordPress extensively in one of our previous posts.
Hosting providers often implement mechanisms to throttle or block repeated failed login attempts. To test your host's brute force protection, go to your site’s login page (usually wp-login.php), and then deliberately enter the wrong login details. If you're not blocked after ten or more incorrect attempts, it's a cause for concern.
Note: Don’t try this if you rely on the same IP address to access your site. We recommend you try it during off-hours or from a different location.
5. Proactive Insecure Component Identification
The world has moved on to proactive security instead of reactive security – you should check if your hosting provider identifies insecure components on your website. However, it is not advisable to install malware on your websites to see what your host does (because what they do won’t be good!)
Instead, you can consider installing a known insecure version of a component – you can find many in the Patchstack database. Be sure that the security bug in question requires a high-privilege logged-in user too. You do not want to install something that could result in your site being hacked.
Once an insecure version of a component is installed, and you have auto-updates turned off, all you need to do is wait. Count the days until you receive a notification from your hosting provider (if you receive a notification at all).
Proactive notification of insecure components is available from a few Patchstack hosting partners already. However, if you do not receive a notification then you can address this yourself by installing the Patchstack plugin.
6. Customer Support
Responsive customer support is an integral component of any web hosting environment, especially when it comes to addressing security issues.
Security incidents can happen at any time. Having responsive customer support means that when you encounter a security issue, you can quickly reach out to experts who can guide you through the resolution process. This reduces downtime and minimizes the potential damage from security breaches.
Moreover, security can be complex, and not all website owners are security experts. Responsive support ensures that you have access to knowledgeable professionals who can help you understand and address security concerns effectively.
Conclusion
We've emphasized the paramount importance of selecting a secure web hosting provider for your WordPress site. Your hosting choice forms the foundation of your website's security.
Consider the security features and practices discussed in this guide, and ensure that your hosting provider aligns with these best practices. This includes aspects such as firewalls, regular backups, DDoS protection, and responsive customer support.
If you find that your hosting provider lacks certain security features, explore the option of using WordPress plugins to supplement your site's security.
Patchstack is here to help you enhance the security of your WordPress site. Think of us as your dedicated team of security specialists, vigilantly safeguarding your online presence.
Additional Resources
- Most Common WordPress Vulnerabilities & How to Fix Them
- How To Find Out If My WordPress Site Has Vulnerable Plugins?
- How To Limit Login Attempts on WordPress (Should You?)
Vulnerability roundup
wp-booklet - Remote Code Execution
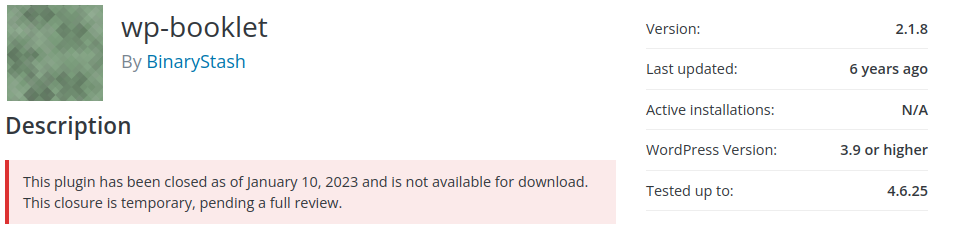
The wp-booklet plugin was recently closed for unofficial reasons, but it is likely because of this remote code execution bug. Luckily, it appears a valid user account (subscriber or higher) is required to exploit this vulnerability. Which may buy you some time to find an alternative.
hide_my_wp - Unauthenticated SQL injection
The developers for hide_my_wp have released a patch to address an unauthenticated SQL injection security bug. Users should make sure they update their installed versions of hide_my_wp as soon as possible.
Please note this is the hide_my_wp premium plugin found in the Envato market.
Thanks and appreciation
This week's thanks go out to the developers of hide_my_wp, wpWave. Great job patching that SQL injection bug.
This week's special thanks go out to everyone taking responsibility for the website's security. Hopefully, that means you.
I will be back next week with more security tips, tricks, opinions, and news on the Patchstack Weekly Security Update!