A critical vulnerability was fixed in the WordPress plugin Elementor.
Do you want to be the first to be alerted about such vulnerabilities? Sign up for Patchstack.
For plugin developers, we have security audit services and Threat Intelligence Feed API for hosting companies.
Note: we are still gathering more information on this vulnerability, such as the requirements to exploit this vulnerability (unauthenticated or subscriber+ which we have confirmed), and are also still waiting on information on the original discoverer of the vulnerability as we did not discover this vulnerability. We'll be updating this article as we continue with the investigation.
The widely popular WordPress website builder plugin Elementor, which has over 5 million active installations, has recently released version 3.6.3 which contains an important security fix.
This vulnerability could allow any authenticated user, regardless of their authorization, to change the site title, site logo, change the theme to Elementor's theme, and worst of all, upload arbitrary files to the site.
The arbitrary file upload vulnerability could allow someone to take over the entire site or perform remote code execution (RCE).
Please update immediately! Patchstack protected sites have received a vPatch to be protected from this vulnerability.
The security vulnerability in Elementor
The vulnerability exists due to an "onboarding" module that is loaded on every request and is hooked into the admin_init WordPress hook. This hook is fired on any admin-related screen/script but does not necessarily imply that it's only fired when a higher privileged user is logged in on the site.
This module determines if the POST payload action and _nonce parameters are sent and also determines if the nonce that is sent along with the request is valid. From this point on it will execute the action given in the action parameter.
Since the nonce token that is checked in this module is sent to any authenticated user it makes it possible for any authenticated user to execute this action regardless of their authorization.
Note: At this time we are still determining if unauthenticated users are able to leak the nonce token as well (and thus are able to exploit the vulnerability).
The patch in Elementor
The patch was applied in version 3.6.3 of Elementor. The diffs of the commit can be found here and the security patch itself can be found here. A snippet of the security patch can be seen below.
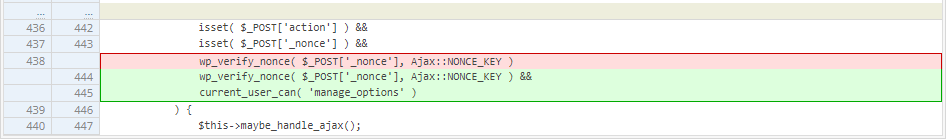
Here you can see that an additional check was added to determine the authorization of the user using the current_user_can WordPress function, which fixes the security issue.
Timeline of the vulnerability in Elementor
13-04-2022 - We came across the vulnerability when it was caught by our monitoring tools. We released a vPatch to all Patchstack paid version customers.
13-04-2022- Added the vulnerability to the Patchstack vulnerability database.





