Welcome back to the Patchstack Weekly security update, this update is for December 9th, 2021. We will talk about the Gravatar breach, web history, and vulnerabilities from this week.
In this week's session, we have two high-risk vulnerabilities to report in WordPress plugins and I will talk about the Gravatar email leaks, one-way encryption, and how the web experience has changed over the years.
I will give recognition to the technical pioneers that brought us Web 2.0, and acknowledge those who are currently looking forward, the yet-to-be-named pioneers who are about to build what will be known as Web3.
Listen to this week's episode here. 👇
Vulnerability news
This week there are two WordPress plugins affected by high-risk vulnerabilities.
The first is an authentication bypass vulnerability patched in the RegistrationMagic plugin. If you run this plugin, please update to 5.0.1.8 as soon as possible.
A second high-risk vulnerability was reported in the PublishPress Capabilities plugin, this vulnerability is unique to WordPress, commonly known as insecure option table updates.
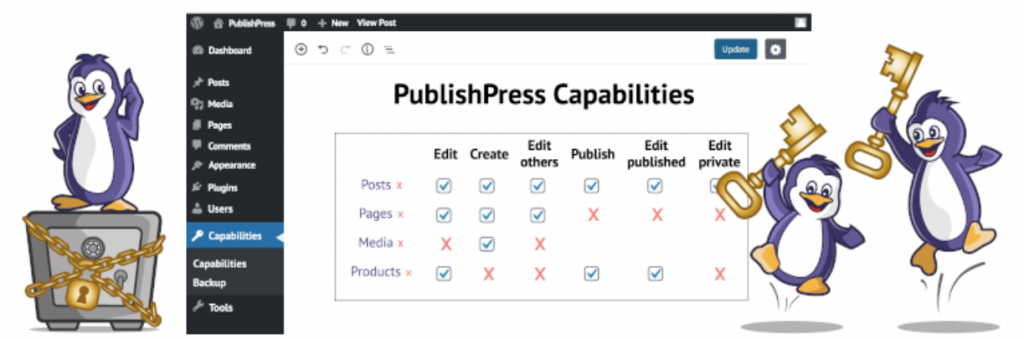
While we could categorize this as an injection attack or OWASP A03-2021, anyone familiar with WordPress development work will immediately understand this risk when they hear an unauthenticated option table update.
Looking at the code diff for this patch, we can see some great work addressing this issue. The developers have added a nonce and capability check in a single if() clause, which is an effective way to protect the function that updates the site's option table values, this prevents CSRF and unauthenticated users from taking this action.
I have talked about Authentication vs. Authorization back in week 45, and you can find the more detailed take on it there. The patch itself does a good job of showing you how easy it is to add CSRF and authentication checks in WordPress.
Hold on, I think I got that attack-type wrong. The patch shows that this was not an Injection attack, the vulnerability here was a lack of authorization checks (OWASP A1-2021, or Broken Access Controls).
My bad, I was wrong. Luckily this is just an inaccurate naming formality, but it is also a reminder that sometimes people make mistakes. It is always worth the time to look a little deeper, understand the problem better, before deciding on an answer.
Have I Been Pwnd Notifies Gravatar users of email exposure
Gravatar is a free-to-use service that connects an individual email address with a "Globally Recognized Avatar" or profile image. Gravatar dates back to 2004 and was acquired by Automattic in 2007 and shortly thereafter integrated into many websites including GitHub, StackOverflow, Slack, and sites running the open-source project WordPress.
"Have I Been Pwnd" is a free-to-use service that informs users if their personal data such as login details, or email addresses are found being exposed after a security incident.
This week, Have I Been Pwnd reported that it identified a data dump of over 114 million email addresses connected to Gravatar has been exposed. The Gravatar breach data was only email addresses and names, no passwords were reported as part of the data set.
How did the Gravatar breach happen?
Gravatar is based on a simple, and very clever design. Ir is extremely easy to implement, and it comes at no cost, which is likely why it has been so widely adopted.
Gravatar's simple design utilizes md5 hashes (or one-way encryption) of email addresses to access a user's gravatar image and profile.
This clever design allows for anyone to look up your public gravatar image and profile if they know your email address, but makes it difficult to figure out what your email address is from your gravatar image or profile URL alone.
Difficult, but not impossible.
There are applications designed to brute-force md5 hashes, you just need some computing power and time. To protect against this, you can add a secret salt whenever you use one-way encryption like md5 hashes, secret salts make it significantly harder to brute force a hash if the secret is not known.

Unfortunately, secret salts are something Gravatar can not implement with its current design and implementation, Gravatar relies on the usage of an unsalted hash of each person's email address and has been implemented this way for the last 20 years.
This risk has been brought up publicly multiple times, in 2008, in 2013, and again in 2016. Then, in 2020 a security researcher named Carlo Di Dato found they were able to view public profile data based on the Gravatar user's ID number, bypassing the need to brute force the hash entirely.
This issue was reported to Gravatar before being released publicly and Gravatar no longer allows access to look up profiles by their ID number.
Unfortunately, it looks like many users of Gravatar have had their emails exposed due to either brute-force attacks or the user ID enumeration.
Gravatar's core design was from a different time, we're talking MySpace and Digg; Facebook and GitHub are barely getting started; Slack and Instagram don't exist. A free service like Gravatar would be highly appealing and provide reasonable security at that price.
Weekly knowledge
From Web 2.0 to Web3
The internet has changed a lot in the last 20 years. Websites transitioned from static content to communities and social networks. Technology that was huge 20 years ago, like Real Player or Adobe flash, has been phased out as they no longer fit into the current web ecosystem, or they cause more problems than they solve.
This transition into a social web is known as Web 2.0 and was driven by many Open Source projects, the technology they developed, and the communities behind them.

Websites like GitHub, frameworks like WordPress, communities like Stack Overflow. These projects were led by pioneers who saw the problem, built a solution, and enriched the web for everyone.
Now, new pioneers are looking toward the future, looking to see how they can solve new problems, problems like centralization of control, and inadequate privacy controls. Problems that have been codified into law in some countries, problems that will not go away.
These pioneers are designing solutions so drastic it is being called Web3, and I am looking forward to seeing what this next generation of pioneers builds for the world.
Thanks and Appreciation
Thanks go out to the developers of PublishPress, for releasing the patch and securing their code.
Further thanks are extended to haveIbeenPwned, a service built by Troy Hunt after he identified a problem and built a solution.
I extend this thanks to all of the other internet innovators as well. In the past, you built what is known as Web2.0, and in the future new innovators will build and define, what Web3 will be. We do not know who the web3 pioneers are just yet, but I bet they will see problems and will put in the work to build the solutions.
I will be back next week with more security tips, tricks, opinions, and news on the Patchstack Weekly security update.





