WordPress 5.8.1 is now available and there are 3 WordPress security issues fixed in that version.
Altogether this security and maintenance release features 60 bug fixes in addition to 3 security fixes we will be focusing on in this article.
Because this was a security release, it is recommended that you update your sites immediately. All versions since WordPress 5.4 have also been updated.
If you have sites that support automatic updates, they’ve already started the update process.
Data exposure vulnerability within the REST API
Web: https://wordpress.org/support/wordpress-version/version-5-8-1/
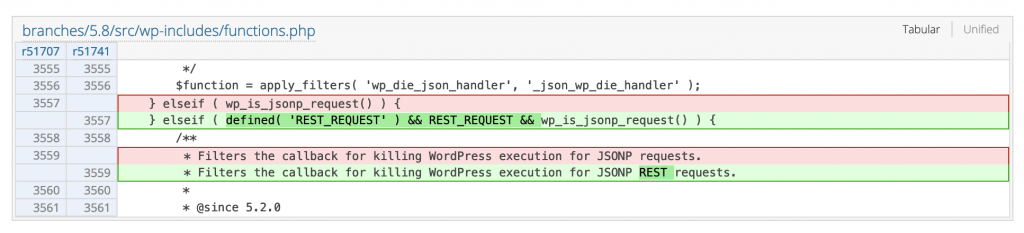
Info: Information Disclosure in wp_die() via JSONP, leading to CSRF.
Core Track: https://core.trac.wordpress.org/changeset/51741/
CWE: CWE-200 (Information Disclosure), CWE-352 (CSRF)
CVE ID: CVE-2021-39200
H1 Report: https://hackerone.com/reports/1142140
CVSS3.0: 3.7 (base score)
Affected versions: 5.2 - 5.8
GitHub commit
Details & Impact: In affected versions of WordPress CMS output data of the function wp_die() can be leaked under certain conditions, which can include data like nonces. It can then be used to perform actions on your behalf.
See more from the Patchstack database.
Block Editor XSS vulnerability
Web: https://wordpress.org/support/wordpress-version/version-5-8-1/
Info: XSS vulnerability within the Gutenberg Block Editor
Core Track: https://core.trac.wordpress.org/changeset/51681
CWE: CWE-79 (Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting'))
CVE ID: N/A
CVSS3.0: N/A
Affected versions: 5.4 - 5.8
Details & Impact: An authenticated low-privileged user (contributor+) can perform Persistent/Stored XSS injections, which can lead to a complete compromise of the website.
Discovered by: Michał Bentkowski from Securitum.
See more from the Patchstack database.
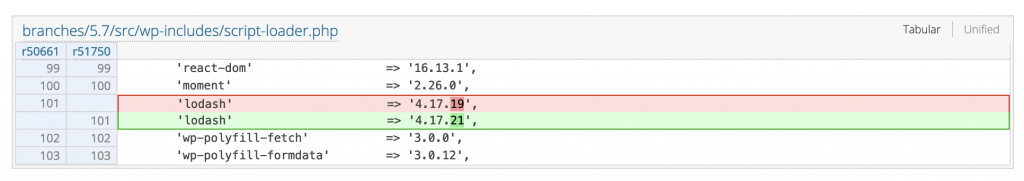
The Lodash library update to version 4.17.21
Web: https://lodash.com
Info: Two vulnerabilities were fixed in Lodash library < 4.17.21
Core Track: https://core.trac.wordpress.org/changeset/51750
Versions update: From version 4.17.19 to version 4.17.21
Vulnerability #1: CWE-77 - Command Injection (published 15 Feb, 2021) [CVE-2021-23337]
CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H - 7.2 base score (High)
GitHub commit | GitHub Advisories | CVE Detail
Vulnerability #2: Regular Expression DoS (published 15 Feb, 2021) [CVE-2020-28500]
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L - 5.3 base score (Medium)
GitHub commit | CVE Detail
See more from the Patchstack database.
Update your WordPress to get these WordPress security issues fixed
We also want to thank all of the reporters for privately disclosing the vulnerabilities. By reporting privately, it will give the WordPress security team time to fix the vulnerabilities before WordPress sites could be attacked.
If you wish to learn more about vulnerabilities within your WordPress sites try out Patchstack.
You can see all the latest WordPress core, plugin, or theme vulnerabilities from the Patchstack vulnerability database.