If you're a WordPress user, then you may already know that WordPress needs certain file permissions to function properly, such as reading, writing, and executing files.
If you misconfigure these permissions, it could put your site at risk.
In this post, you’ll learn all about WordPress file permissions, and how you can change them to secure and optimize your site. You’ll also find out about different notations used in Unix operating systems to denote different permission levels.
Additionally, you'll learn how to use FTP, cPanel, or a command-line interface to change your file permissions, and what signs to look for to identify and resolve file permission issues.
What are WordPress file permissions?
When you store files on your personal computer, only you can access it. However, when you store files on a shared computer, such as a server, more than one person can access and modify these files. We can control who gets to see which files by applying specific permissions to each file.
File permissions dictate who can read, write, or execute specific files, influencing the level of control users or processes have over your site's resources. These permissions are crucial for both security and functionality.
Security-wise, proper file permissions prevent unauthorized access, protecting sensitive information and thwarting potential malicious activities. Functionality-wise, they ensure that the right processes and users can perform any necessary actions, such as updating plugins, themes, or uploading media.
Understanding file permissions
There are three basic types of file permissions – read, write, and execute. Let’s see how these apply to WordPress files and directories.
- Read (r): Allows viewing the contents of a file or the list of files in a directory. Crucial for accessing themes, plugins, and configuration files.
- Write (w): Permits the modification of a file's content or the creation and deletion of files within a directory. Essential for tasks such as installing plugins, updating themes, and uploading media.
- Execute (x): Grants permission to run scripts or execute files. Necessary for executing PHP scripts, running certain plugins, or accessing specific directories for dynamic content.
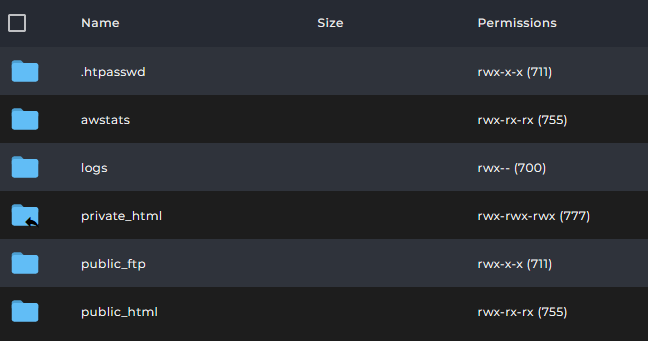
Reading file permission notation on Linux
When reading file permissions, you will see something like -rw-rw-r-- , which is a way of expressing the read and write access permissions of a file or directory for the owner, a group, or others. The permissions are divided into three sets of three characters, as follows:
- The first set of three characters,
-rw-, applies to the user or owner of the file or directory. The first-means that it is a regular file, not a directory or a special file. Therwmeans that the owner can read and write the file, but not execute it. - The second set of three characters,
rw-, applies to the group that owns the file or directory. Therwmeans that the group members can also read and write the file, but not execute it. - The third set of three characters,
r--, applies to the others, or anyone else who is not the owner or a group member. The r-- means that the others can only read the file, but not write or execute it.
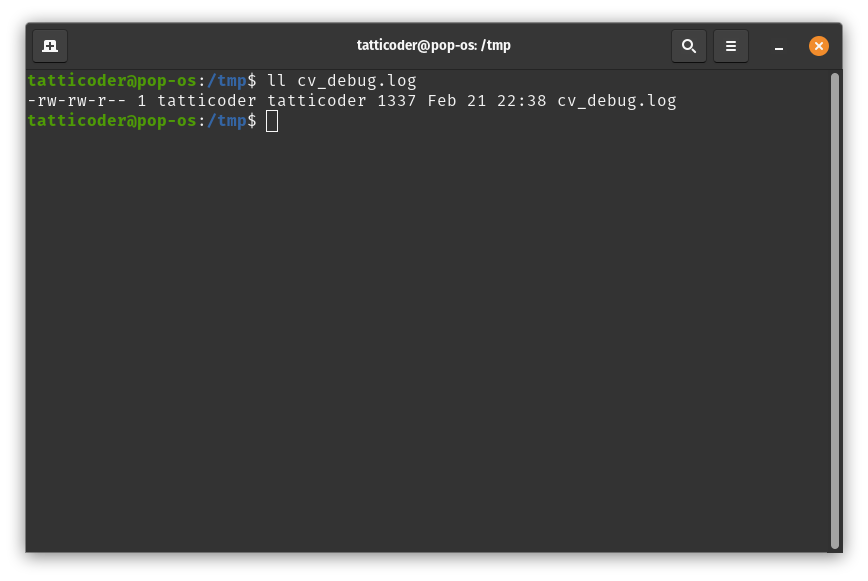
In the above example, we can see that the given file has the permission string set to -rw-rw-r–.
Numeric representation of file permissions (e.g., 755, 644)
When using a Unix-based operating system, you will often see the file permissions being represented as a number. For example, 777, 755, 644, and so on. This numeric representation of file permissions simplifies the complex combinations of permissions into a concise three-digit code.
This is called octal notation; it uses numbers to represent the permissions, where 4 stands for read, 2 for write, and 1 for execute. You can add the numbers to get the combination of permissions, such as 6 for read and write, or 7 for read, write, and execute. You can also use 0 for no permission.
For example, to set the permissions of a file to -rw-rw-r–, you can use the command chmod 664 filename.
This functionality is built on the binary number system and is a quick and easy way to communicate the necessary information while minimizing the possibility of error. For instance, it is simpler to say a three digit number instead of explaining who can read files and who can modify it.
In the numeric representation, the three digits correspond to the owner, group, and others. For example, in '755,'
- The owner has read (4) + write (2) + execute (1) permissions which totals to 7
- The group has read (4) + execute (1) permissions which totals to 5
- And all the other users of the computer have read (4) + execute (1) permissions which totals to 5.
Understanding these numeric codes is vital for interpreting and configuring file permissions in WordPress. Users can set permissions using FTP, cPanel, or command-line tools. Configuring them correctly ensures that the right users and processes have the necessary access, striking a balance between security and functionality.
Default WordPress File Permissions
The default file permissions set by WordPress during installation allow the owner of the files and directories to read, write, and execute the files, while the group and the public can only read and execute them – meaning they cannot modify the files.
The wp-config.php file has more restricted permissions, because it contains sensitive information such as database credentials.
It is important for you to be aware of these file permissions, because they affect the security and functionality of your WordPress site. If the file permissions are too loose, malicious users or scripts may be able to access, modify, or delete your files, or inject malicious code into them.
This can compromise the security and performance of your site, and expose your data to hackers. If the file permissions are too strict, WordPress may not be able to perform certain operations, such as updating, installing plugins, or uploading media. This can limit the functionality and usability of your site, and cause errors or warnings.
Permissions on Windows
The file permissions on Linux and Windows servers are different, because they use different file systems and security models.
- Linux uses a Unix-like file system, which assigns permissions to the owner, group, and others for each file and directory.
- Windows uses a NTFS file system, which assigns permissions to users and groups for each file and directory, based on access control lists (ACLs).
The file permissions on Linux servers are usually represented by three numbers, such as 755 or 644, as explained above. The file permissions on Windows servers are usually represented by letters, such as R, W, X, D, or F, which stand for read, write, execute, delete, or full control, respectively. For example, a file with permissions RWD means that the user or group can read, write, and delete the file.
Modifying file permissions on Linux
There are different ways to change file permissions depending on the tools you use to access your WordPress files and directories. Here are some common methods:
- FTP: You can use an FTP client such as FileZilla to connect to your server and browse your WordPress files and directories. To change the permissions of a file or directory, you can right-click on it and select File Permissions. A dialog box will appear where you can either enter the numeric value of the permissions, or use the checkboxes to set the read, write, and execute permissions for the owner, group, and others.
- cPanel: You can use the File Manager app in your cPanel to access your WordPress files and directories. To change the permissions of a file or directory, you can right-click on it and select Change Permissions. A dialog box will appear where you can use the checkboxes to set the read, write, and execute permissions for the owner, group, and others.
- Command-line: You can use a terminal or SSH client to connect to your server and use the command-line tool chmod to change the permissions of a file or directory. To use chmod, you need to specify the permissions using the numeric value or the symbolic notation, and the file or directory name.
For example, to change the permissions of a file named example.html to 644, you can use the command chmod 644 example.html.
Troubleshooting permission issues on Unix
When working with permissions, it is easy to get frustrated and grant all permissions to all users – but it is generally not a good idea to do this. We recommend only granting the necessary permissions to each file, and only increasing it where necessary – this is called the principle of least privilege.
Although the principle of least privilege is useful to keep things secure, sometimes you might encounter errors due to insufficient permissions. Some common signs that indicate file permission issues in WordPress are:
- Error messages while uploading, installing, or updating files or plugins, such as “Installation failed: Could not create directory” or “Failed to open stream: Permission denied”.
- Blank pages or missing content on your WordPress site, such as images, stylesheets, or scripts.
- Files or directories being inaccessible or not found, such as the wp-config.php file or the wp-content directory.
- Security warnings or alerts from your web host or WordPress security plugin, indicating that your files or directories have been modified or compromised.
When changing permissions, it is important to refer to the official documentation of the WordPress plugin or theme. With some of the above mentioned issues it won't be immediately obvious that they can be fixed by granting permissions. Therefore, system administrators sometimes temporarily change the permissions to 777 and grant all permissions to everyone (which is highly insecure) just to see if this fixes the issue.
WordPress directories or files that require heightened security
There are some specific directories or files that require heightened security measures, as they contain sensitive or critical information or functionality for your WordPress site. Some examples are:
- The wp-config.php file, which contains your WordPress database credentials, security keys, and other important settings that should be protected very securely. You should set the permissions of this file to 640, which means that only the owner can read and write the file, and the group can only read the file.
You should also move this file to a higher level than your web root directory, if possible, to prevent web access to it. - The wp-content directory, which contains your WordPress themes, plugins, uploads, and other custom files. You should set the permissions of this directory to 755, which means that the owner can read, write, and execute the directory, and the group and others can only read and execute the directory.
You should also set the permissions of the files inside this directory to 644, which means that the owner can read and write the files, and the group and others can only read the files. You should also disable PHP execution in this directory, by creating a .htaccess file to prevent any malicious PHP code from running in this directory. - The .htaccess file, which controls the configuration of your web server and the behavior of your WordPress site. You should set the permissions of this file to 644, which means that the owner can read and write the file, and the group and others can only read the file. You should also use this file to add security rules, such as blocking access to specific files or directories, enforcing HTTPS, or preventing hotlinking.
Conclusion:
In summary, WordPress users should set strict file permissions to control who can access and modify the files on their server. The recommended WordPress file permissions are:
- 755 for directories
- 644 for files
- 640 for wp-config.php.
But file permissions are not enough to protect your WordPress site from hackers and malware.
You need a comprehensive WordPress security solution that can monitor, detect, and prevent any threats to your site. That’s why you should sign up for Patchstack, the ultimate WordPress security plugin.
Patchstack is a free WordPress security plugin that offers the following features:
- Real-time security monitoring and alerts for your WordPress site, plugins, and themes.
- Automatic vulnerability scanning and removal, with regular reports and logs.
- WordPress firewall and brute force protection, with IP blocking and whitelisting.
- WordPress hardening and optimization with security recommendations.
Patchstack is easy to install and use, and compatible with any WordPress site, plugin, or theme.
Sign up for Patchstack today, and get the best WordPress security plugin for free.





