All-in-One WP Migration Box Extension
Unauthenticated Access Token Manipulation
All-in-One WP Migration Google Drive Extension
Unauthenticated Access Token Manipulation
All-in-One WP Migration OneDrive Extension
Unauthenticated Access Token Manipulation
All-in-One WP Migration Dropbox Extension
Unauthenticated Access Token Manipulation
This blog post is about the All-in-One WP Migration Extensions vulnerability. If you're an All-in-One WP Migration Extensions user specified below, please update the plugin to the patched version mentioned in this article.
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout the All-in-One WP Migration Extensions Plugin
The plugin All-in-One WP Migration (free version), which is not vulnerable to this vulnerability but only the listed extensions, is the most popular migration plugin in WordPress which is estimated to be used by over 5 million websites. The plugin also has several premium extensions which allow users to do a migration to a third-party platform such as Box, Google Drive, OneDrive and Dropbox. The plugin itself is developed by ServMask.

This plugin is one of WordPress's most trusted and utilized plugins for moving websites with absolute ease. It's intently built with the non-technical user in mind, All-in-One WP Migration comes loaded with newbie-friendly functions that allow us to migrate our WordPress website with little to no technical knowledge or experience.
The security vulnerability
The All-in-One WP Migration Extensions suffers from unauthenticated access token manipulation, which allow any unauthenticated users to update or delete the access token configuration of the affected extension. This access token manipulation could result to a potential sensitive information disclosure of migration to the attacker's controlled third party account or restore a malicious backup. The vulnerability is assigned CVE-2023-40004. Below are the details on which version the vulnerability is patched on each of the extensions :
- All-in-One WP Migration Box Extension , version 1.54
- All-in-One WP Migration Google Drive Extension , version 2.80
- All-in-One WP Migration OneDrive Extension , version 1.67
- All-in-One WP Migration Dropbox Extension, version 3.76
Unauthenticated Access Token Manipulation
The vulnerable code is pretty identical on all of the 4 affected extensions. The underlying vulnerable code exists in the init function (below is the example code from All-in-One WP Migration Box Extension) :
public function init() {
if ( isset( $_GET['ai1wmbe_token'] ) ) {
update_option( 'ai1wmbe_box_token', urldecode( $_GET['ai1wmbe_token'] ) );
// Redirect to settings page
wp_redirect( network_admin_url( 'admin.php?page=ai1wmbe_settings' ) );
exit;
}
if ( AI1WMBE_PURCHASE_ID ) {
update_option( 'ai1wmbe_plugin_key', AI1WMBE_PURCHASE_ID );
}
}The code difference from the other 3 extensions is only located on the naming of the ai1wmbe value which differ on each of the affected extensions. Notice that the function itself will update the ai1wmbe_box_token option from the $_GET['ai1wmbe_token'] value. The init function itself is hooked to the WordPress's admin_init hook which is declared in activate_actions function :
/**
* Register listeners for actions
*
* @return void
*/
private function activate_actions() {
add_action( 'admin_init', array( $this, 'init' ) );
add_action( 'admin_init', array( $this, 'router' ) );
add_action( 'admin_init', array( $this, 'load_textdomain' ) );
add_action( 'admin_head', array( $this, 'admin_head' ) );
-------------------------- CUTTED HERE --------------------------The admin_init hook itself could be triggered by unauthenticated user from the /wp-admin/wp-ajax.php endpoint. Since there is no permission and nonce validation on the init function, an unauthenticated is user able to modify or delete the access token used on each of the affected extensions.
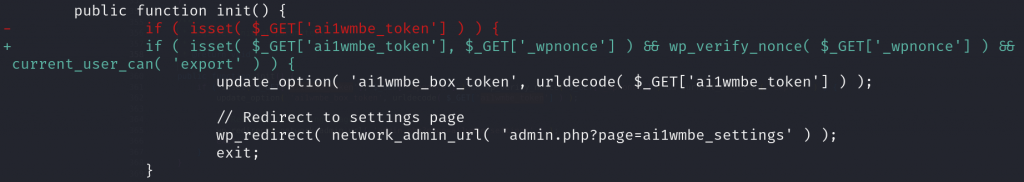
The patch
The patch is as simple as adding permission and nonce validation on the init function. Below is an example patch from the All-in-One WP Migration Box Extension:
Conclusion
For plugin and theme developer, keep in mind that the admin_init hook by default can be reached by an unauthenticated user. We recommend applying permission and nonce validation on the function hooked to admin_init if there is sensitive information exported or an action being performed.
Timeline
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




