Welcome to the Patchstack Weekly Security Update, Episode 53! This update is for the first week of 2023.
I will start by wishing you a Happy New Year - and thank you for listening/reading!
2023's first week's news will include an update related to the LastPass compromise from last summer. The cloud-based password vault vendor released an important announcement during the holidays, which you need to know about.
LastPass's announcement is an inconvenience, but also a reminder about a common security best practice: always rotate your passwords. I will kick off the new year by sharing some security best practices with you over the next few weeks.
In this week's vulnerability roundup I will discuss a handful of security bugs found in WordPress components that have gone unpatched. Unfortunately for these open-source projects, the new year is starting out rough, but it's important for users of these plugins to know about the risks so they can take action.
LastPass security breach update
I have shared updates in the past related to the LastPass security incident from August 2022. The updates I have shared with you are based on the official announcements made by LastPass.
Previously, I said that LastPass assured users that no customer password vaults were leaked during the breach. On December 22nd, 2022 LastPass released an update that now makes it clear - attackers did gain access to an encrypted copy of customer data, including the password vaults.
The data was encrypted, so the attackers do not have access to your passwords as plain text. However… all encrypted data can be de-encrypted eventually, given enough time. The fact the attackers have a copy of the LastPass source code also means they know what algorithms were used to encrypt the data, and they know how the salts were generated, which gives the attackers an advantage. It will still take a lot of computational time to crack every last pass user's encrypted vault, but it will happen if an attacker who has a copy of this stolen data puts the effort into it.
This means if you've used LastPass, you should be rotating your passwords before it is too late. The only good news is, you have some time to get this done - but the sooner, the better.
In fact, you should be rotating your passwords regularly. LastPass has this as a feature to make this automatic (for some websites.) For the rest of us non-LastPass users, it isn't hard to do manually.
Security best practice: rotating passwords
With the LastPass incident fresh on our minds we are reminded passwords should be temporary, not permanent. This is because breaches happen. Backups of account login credentials get leaked from major vendors all the time. LastPass is not alone in this, you can view details on many public breaches on haveibeenpwned.com.
If we accept that breaches happen, companies we trust with our data with get hacked, and we need to be responsible for our own account data. What can we do?
As far as passwords and credentials are concerned, here is what I recommend:
- Rotate passwords regularly, maybe once a year but always rotate them after an incident occurs when the secret may have been leaked.
- Never use a password twice, every login needs its own unique and strong, password.
- Use 2FA, and rotate your 2FA secrets too. Different 2FA options have different risks, but if you can rotate the 2FA code you should.
Take some time this new year to rotate the important account passwords in your life. LastPass user or not this is a best practice for everyone.
Vulnerability roundup
The trend of abandoned open-source projects not receiving security patches continues as the new year starts. I spent some time writing some last patches for abandoned WordPress plugins in 2022, but there are so many each week that it's unsustainable to write a patch for everything.
I will continue to share a list of abandoned WordPress components with serious vulnerabilities that have gone unpatched each week.
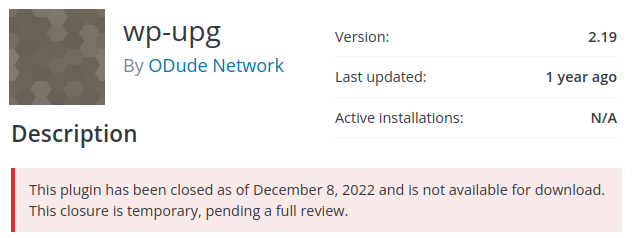
wp-upg - Unauthenticated Remote Code Execution
This is a serious risk and it is strongly recommended sites using wp-upg aka "User Post Gallery" find another solution for their websites. This plugin has not been updated in over a year, and the developer appears focused on other projects at this time.
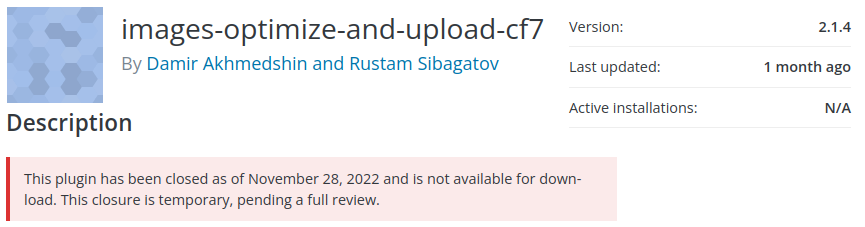
images-optimize-and-upload-cf7 - Unauthenticated Content Deletion
The developers for this projects have been active in the last few months. Answering support questions in the plugin's forums and pushing a release in November. So there is still hope they may be working on a patch.
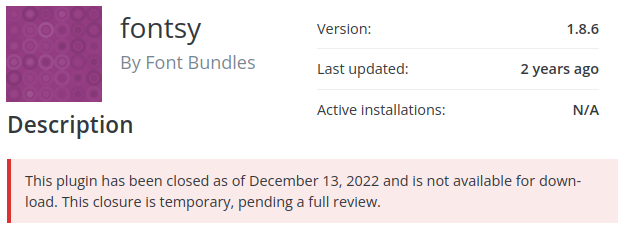
fontsy -Unauthenticated SQL Injection
Users of this fontsy plugin should find an alternative ASAP. The plugin's developer activity has been silent for over 2 years, with no updates and no support activity on WP.org in that time. It appears the developer has moved on to focus on other projects.
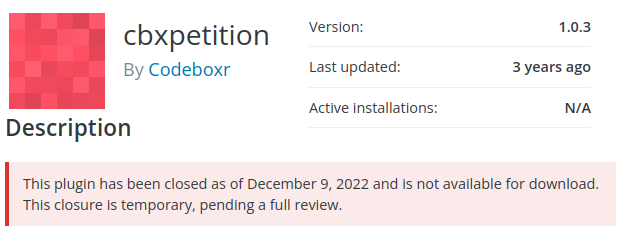
cbxpetition - Unauthenticated SQL Injection
The cbxpetition plugin has not received an update in 3 years and was last tested against WordPress 5.2.17. This is a signal the project has been abandoned. It would be recommended users of cbxpetition find an alternative plugin for their needs.
Thanks and appreciation
This week's thanks goes out to the team at LastPass for being transparent about the customer password vault data being compromised during the breach. I suspect your security, incident response, and development teams have been working extra hard in response to this incident. Great job, keep it up.
Special thanks goes out to the Patchstack Alliance. We are still adding up the numbers, but 2022 was a big year for WordPress vulnerabilities being reported, patched, and managed through the Patchstack Alliance.
I will be back next week with more security tips, tricks, opinions, and news on the Patchstack Weekly Security Update!





