Websites made with WordPress usually rely heavily on third-party software components like plugins and themes. Every single day, hackers and security enthusiasts find new vulnerable plugins or vulnerabilities across different WordPress plugins and themes.
In 2022 alone we added 4,528 new known security bugs to our WordPress vulnerability database.
Keeping the number of plugins on your WordPress installation as low as possible is highly recommended, as each installed plugin raises the risk of having a vulnerable component in your site.
What is a plugin vulnerability?
Plugin vulnerability refers to a weakness or flaw in plugin code, that can be exploited by attackers. When a vulnerable plugin is found it should be either removed or updated to a newer, safe version.
Why would I care about plugin vulnerabilities?
The purpose of hackers exploiting these plugin vulnerabilities is to gain unauthorized access to your website, inject malicious code, and steal sensitive information. In that way, they can also gain access to your server, or perform other types of malicious actions.
There are lots of different types of vulnerabilities that researchers and hackers find across different plugins and themes. We have listed the 21 most common WordPress vulnerabilities in this article.
Mostly, the reason why vulnerabilities come to exist in plugins or themes is that the developers have not paid enough attention to basic security rules. And no one checks the code before it's pushed live to the WordPress plugins repository.
How do I check WordPress plugin vulnerabilities?
To see if your site currently hosts vulnerable software versions, try Patchstack. Installing Patchstack is quick and easy. You'll get an overview of which of the current plugin and theme versions found on your site(s) are vulnerable, based on our vulnerability database.
Set up Patchstack in 3 simple steps:
- Create a Patchstack account
- Add your website's URL inside the Patchstack App
- Install the Patchstack plugin on your WordPress site
After installing the Patchstack plugin, it's easy to keep an eye on your software - and every time a vulnerability is found in any of the components your WordPress uses, you'll get an email notification.
On the screen below, you'll see an example of what the Patchstack App shows you about your site's security:
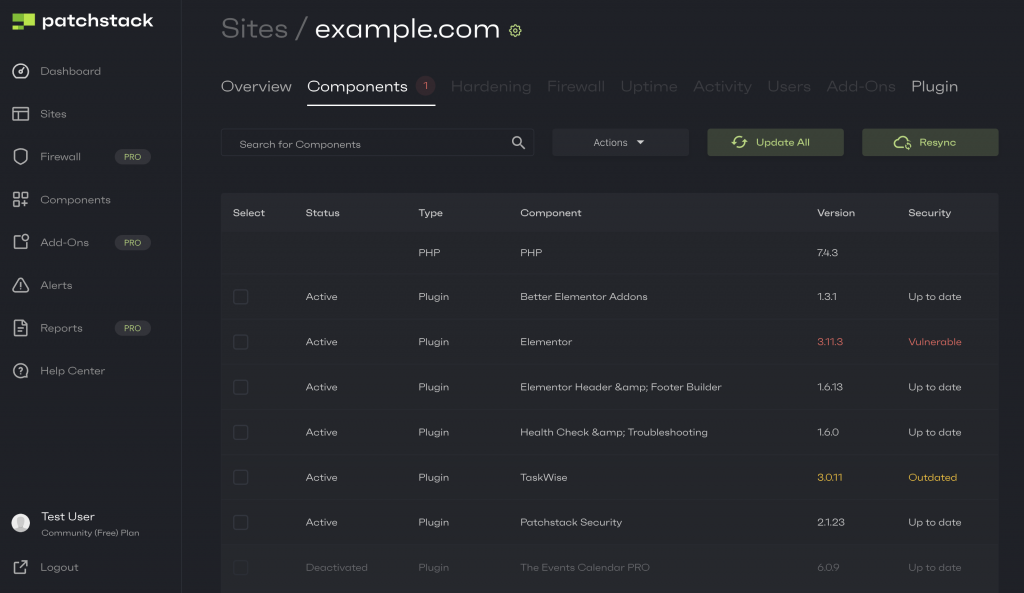
What to do if I find vulnerable plugins on my site?
Your best option is to enable the Patchstack firewall. It protects your site from all attacks targeting vulnerable components, so you don't have to worry about constantly keeping an eye on the software versions.
Patchstack protects your WordPress sites with automatically applied vPatches, as well as OWASP's top 10 firewall rules.
In case you do feel like you want to stay on the free plan, then you can simply follow this routine:
- Update the vulnerable software always as quickly as possible. You can do it straight through the Patchstack App by selecting the component and clicking "Actions" > "Update". You can also have Patchstack send you notification emails when vulnerable components appear on your site(s).
- If no update is available for the vulnerable component, we strongly urge you to replace the plugin or component in general or remove it completely ASAP.
Please note that regardless of having protection, it is generally a sensible practice to keep all your software up to date, if possible.
Keep an eye on vulnerable plugins
It is completely normal that vulnerabilities are found in the software we use on our WordPress websites. By paying attention to the tools you use, you can prevent bad stuff from happening.
If you have any questions about WordPress security, feel free to start the live chat. Click on the green chat circle on the bottom right corner of this page!





