We are beyond excited to celebrate the winter holidays and the launch of the Patchstack Alliance Discord community with a special WordPress bug-hunting event taking place throughout December 2022.
In December, we released a public leaderboard and profiles for the top security researchers who contribute to making WordPress and the open-source web more secure.
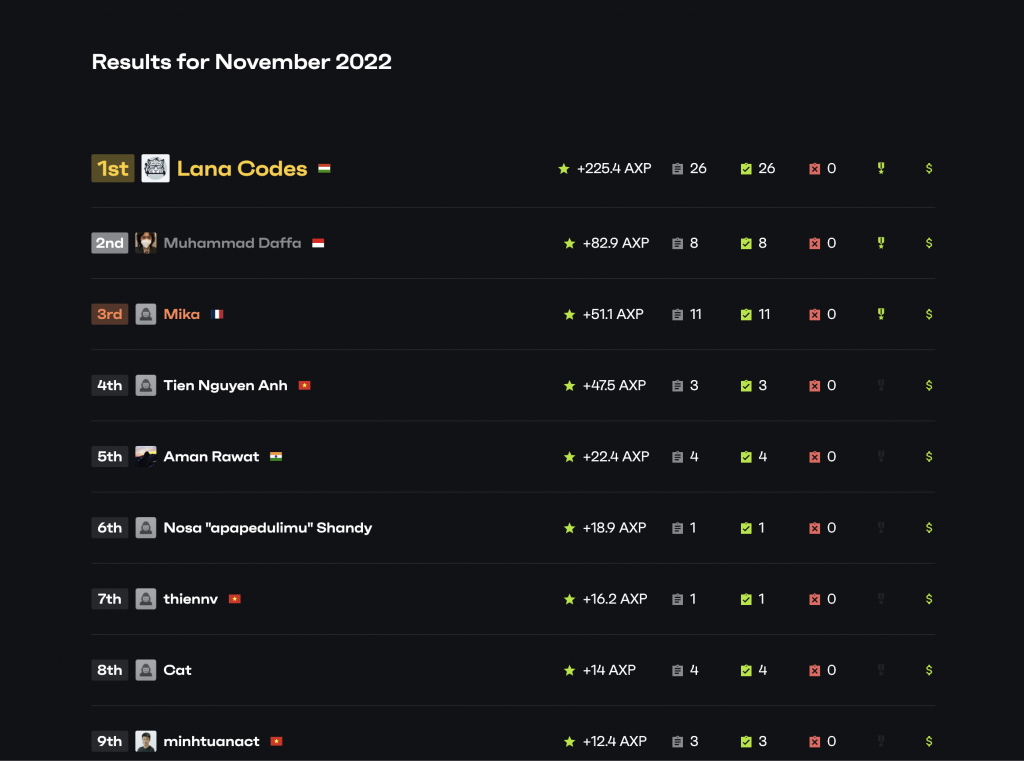
You can see the November WordPress bug-hunting winners and profiles here: https://patchstack.com/database/leaderboard?monthly=2
December prize pool is $4300 in cash rewards
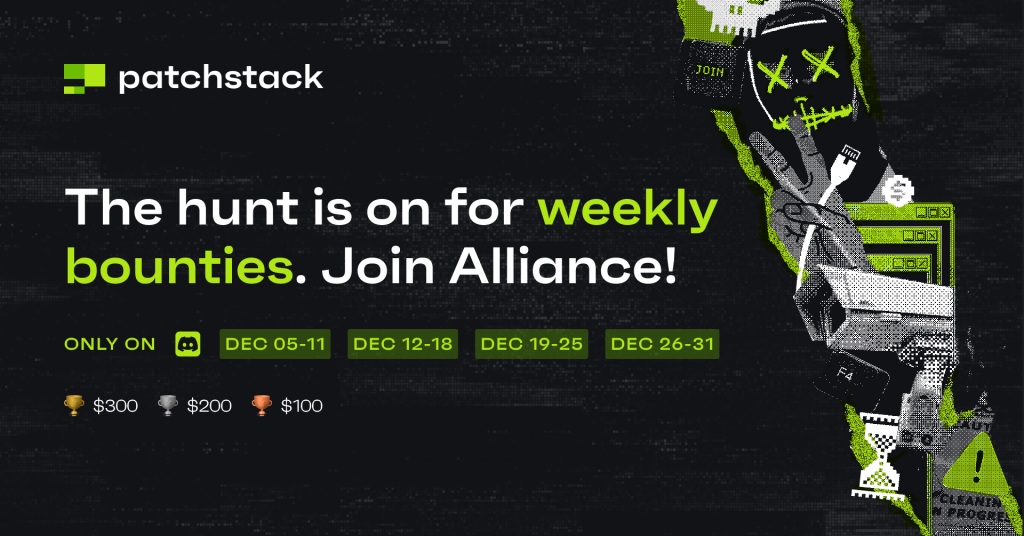
On each Monday, we’ll announce the scope for the weekly WordPress bug-hunting focus. With 4 weeks of challenges and monthly prizes on top, we pay out $4300 in cash rewards!
Each week has a special vulnerability that needs to be hunted in any publicly available WordPress themes, plugins, or even in the core itself.
The top 3 researchers with the most points from each week will get cash rewards (1st place - $300, 2nd - $200, and 3rd - $100). All points will also be used for the monthly Patchstack Alliance competition, with an additional $1900 prize pool.
The first week (Dec. 5-11) - Cross-Site Request Forgery (CSRF) - finished!
1st place ($300 bounty) - Lana Codes reported 58x vulnerabilities (349.4 points)
2nd place ($200 bounty) - Muhammad Daffa reported 9x vulnerabilities (129 points)
3rd place ($100 bounty) - Cat reported 25x vulnerabilities (125.3 points)
The second week (Dec. 12-18) - Cross-Site Scripting (XSS) - finished!
1st place ($300 bounty) - minhtuanact reported 8x vulnerabilities (50.4 points)
2nd place ($200 bounty) - pilvar reported 1x vulnerabilities (31.5 points)
3rd place ($100 bounty) - Muhammad Daffa reported 2x vulnerabilities (21.5 points)
The third week (Dec. 19-25) - SQL injection (SQLi) - finished!
1st place ($300 bounty) - Le Ngoc Anh reported 2x vulnerabilities (16.8 points)
2nd place ($200 bounty) - minhtuanact reported 10x vulnerabilities (14.6 points)
3rd place ($100 bounty) - Lucio Sá reported 1x vulnerability (7.5 points)
The fourth week (Dec. 26-31) - Remote Code Execution (RCE) - finished!
1st place ($300 bounty) - minhtuanact reported 1x vulnerability (9 points)
2nd place ($200 bounty) - Le Ngoc Anh reported 1x vulnerability (8.5 points)
3rd place ($100 bounty) - none
More details on the Patchstack Alliance Discord
Claim your CVEs
Patchstack is an official CNA authorized by MITRE to assign CVE IDs to vulnerabilities reported through the Patchstack Alliance bug bounty program. We make sure the reports get to the developers and that all ethical hackers get credit for their research and contribution.
Join the community
Patchstack Alliance is a community of ethical hackers who contribute to making the entire web more secure. It’s a great place to learn new skills, make friends and create a portfolio of your security research.
For more information & rules, join our Discord server here: https://patchstack.com/bug-bounty/