
Earn cash bounties by hunting for vulnerabilities in WordPress software
Time to squash some security bugs! Successfully report a vulnerability to sign up to our bounty platform. Read the rules.

Zeroday payouts up to
$14,400
Receive generous payouts for reporting high-impact vulnerabilities
Terms & conditionsRewards
Installs
Subs
Unauth
5M+
$7,200
$14,400
1M+
$3,600
$7,200
500K+
$2,450
$4,900
100K+
$1,300
$2,600
50K+
$700
$1,400
10K+
$300
$600
5K+
$200
$400
1K+
$125
$250

Monthly TOP20 prize pool
$8,850
Guaranteed in monthly payouts to TOP20 + one lucky ethical hacker
See leaderboardRewards
🥇 1st
$2,000
🥈 2nd
$1,400
🥉 3rd
$800
4th
$600
5th
$500
6-10th
$400
11-15th
$200
16-19th
$100
20th
$50
Random pick
$50
Random pick outside TOP20
$50

Level up to unlock rewards
$8,887
Earn extra rewards as you accumulate XP and level up
How to earn XPRewards
Lvl 10
$3,000
Lvl 9
$1,700
Lvl 8
$1,337
Lvl 7
$1,000
Lvl 6
$700
Lvl 5
$500
Lvl 4
$300
Lvl 3
$200
Lvl 2
$100
Lvl 1
$50
first to secure 600 plugins' users
we manage security for 600 plugins
 WP Bakery
WP Bakery
 MainWP
MainWP
 Slider Revolution
Slider Revolution
 Visual Composer
Visual Composer
 WP Rocket
WP Rocket
 WP Bakery
WP Bakery
 MainWP
MainWP
 Slider Revolution
Slider Revolution
 Visual Composer
Visual Composer
 WP Rocket
WP Rocket
 WP Bakery
WP Bakery
 MainWP
MainWP
 Slider Revolution
Slider Revolution
 Visual Composer
Visual Composer
 WP Rocket
WP Rocket
 WP Bakery
WP Bakery
 MainWP
MainWP
 Slider Revolution
Slider Revolution
 Visual Composer
Visual Composer
 WP Rocket
WP Rocket
 WP Bakery
WP Bakery
 MainWP
MainWP
 Slider Revolution
Slider Revolution
 Visual Composer
Visual Composer
 WP Rocket
WP Rocket
 WP Bakery
WP Bakery
 MainWP
MainWP
 Slider Revolution
Slider Revolution
 Visual Composer
Visual Composer
 WP Rocket
WP Rocket
Focus on research and let Patchstack handle reporting to vendors

Patchstack assigns CVE’s to your name faster

Start a public research profile and build reputation
Join the fastest growing OS security community
securing the web with the support of
Clear framework
Patchstack enforces a clear and standardized form for reporting and handling vulnerability reports faster
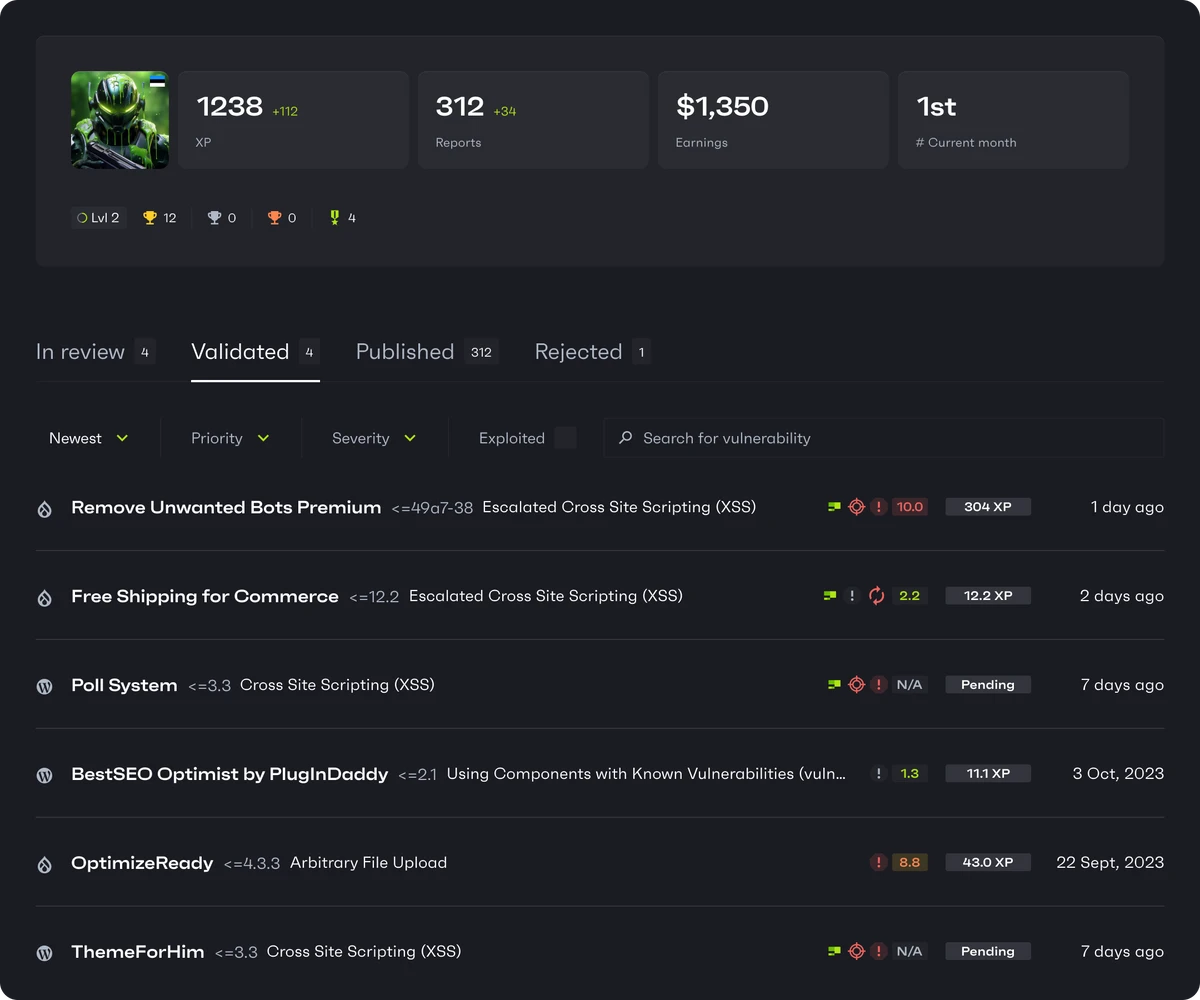
Submissions overview
Researchers can now keep track of their performance; view the status of and access all vulnerability reports in one place
Public profile
All of your reports and achievements will be displayed on your public profile. You can include socials and even a BuyMeACoffee or Paypal link
How to start your researcher profile?
What the FAQ?
For now, we only support PayPal payments. Patchstack covers all payout (PayPal) fees, so you receive the full amount exactly as promised. However, we are not responsible for other fees such as withdrawal or local taxes. Each researcher is responsible for administrating their local taxes related to the bounty payouts.
XP points are calculated by combining parameters like CVSS score, active installation (sales if premium) count, and prerequisite (authentication/authorization) needed to carry out an attack. No points are given if the reported component has less than 500 active installs (sales if premium) or requires an admin/super-admin role as a prerequisite. However, these reports will still receive a CVE ID for the submitter.
Indeed, Patchstack is paying bounties for vulnerabilities even if the software vendors have no means to fund it. We finance the bounty program from our core business to give back to the community.
Everyone can join Patchstack’s Bug Bounty program as long as they are committed to making the WordPress ecosystem safer. By submitting at least one valid vulnerability report that meets Patchstack’s Bug Bounty program vulnerability report submission requirements, you become a member of Patchstack’s Bug Bounty program.
Patchstack’s Bug Bounty program is an open community of cyber security researchers, developers, pentesters, and bug bounty hunters who research and report security issues in WordPress plugins to win monthly bounties, special competitions, and seasons. Our reporting process and validation triage fast-track security patch creation for vendors, saving you time to do more research.
We already have some of the best WordPress security talents on our dedicated Discord channel, and our community was the world’s largest contributor of open-source vulnerability disclosures in 2023, surpassing even the GitHub community.
If you have questions, ask the staff on our Discord.
Ready to squash some security bugs and cash those bounties?
New to bug hunting? Learn from our Academy.


