The plugin Responsive Menu - Create Mobile-Friendly Menu (versions 4.1.7 and below), which has over 100.000 active installations, suffers from a critical vulnerability. This vulnerability allows any authenticated user, regardless of their authorization, to execute nearly all of the actions that only administrators are supposed to be able to execute.
Do you want to be the first to be alerted about such vulnerabilities? Sign up for Patchstack.
For plugin developers, we have security audit services and Threat Intelligence Feed API for hosting companies.
One of these actions could allow any authenticated user to upload arbitrary files to the site, including PHP backdoors. Other examples of actions that can be executed are the ability to change all of the settings, import menus, export menus, delete menus, and interact with the menus.

The plugin is described as a plugin that is highly customizable Responsive Menu Plugin for WordPress. With over 150 customizable options you get a combination of 22,500 options! No coding experience or knowledge is needed with an easy-to-use interface you can get it looking exactly as you want with minimal fuss.
The described vulnerability was fixed in version 4.1.8.
The security vulnerability in Responsive Menu
The core issue that causes these vulnerabilities to exist is due to 2 mistakes: the first mistake is that almost none of the admin-related actions have an authorization check. These actions do have a nonce token check, but due to the second mistake, this nonce token can be leaked by manipulating a URL.
The snippet of code that leaks the nonce token is shown below:
if ( empty( $post_type ) && ! empty( $_GET['post_type'] ) ) {
$post_type = sanitize_text_field( wp_unslash( $_GET['post_type'] ) );
}
if ( 'rmp_menu' !== $post_type ) {
return;
}
// ...
wp_localize_script(
'rmp_admin_scripts',
'rmpObject',
array(
'ajaxURL' => admin_url( 'admin-ajax.php' ),
'ajax_nonce' => wp_create_nonce( 'rmp_nonce' ),
'THEMES_FOLDER_URL' => wp_upload_dir()['baseurl'] . '/rmp-themes/',
)
);These snippets of code are part of the function that injects the JavaScript variables into the page. In order to reach the function call that injects the nonce token into the page, there is an if statement to determine if the appropriate page is loaded.
However, this can be bypassed by simply visiting the edit profile page and adding &post_type=rmp_menu to the URL.
Once this URL is loaded on any /wp-admin/ related page, the nonce token can be seen in the source of the website. This can then be used to execute the admin actions of this plugin. One of these actions is admin_post_rmp_upload_theme_file which calls the function rmp_upload_theme.
This function accepts a .zip file of a menu theme which will be unpacked into the /wp-content/uploads/rmp-menu/themes/ folder.
None of the files inside of the .zip file are checked, which allows anyone to add a PHP backdoor to this .zip file to then gain full access to the website once it has been uploaded.
The patch in the Responsive Menu
Since the issue primarily existed due to the nonce token leakage, the addition of a simple authorization check to the function that injects these JavaScript variables into the page would be sufficient. This patch can be seen below.
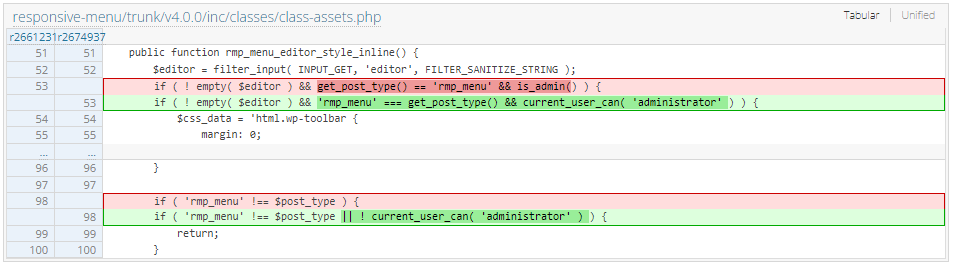
In addition to this change, a few more changes were made to determine that the user has the right authorization to execute several of the higher privileged actions.
Timeline
29-01-2022 - We found the vulnerability and we released a vPatch to all Patchstack paid version customers.
29-01-2022 - We reached out to the developer of the plugin and gave them the information.
08-02-2022 - The developer released version 4.1.8 which contains a sufficient patch.
16-03-2022 - Added the vulnerability to the Patchstack vulnerability database.
16-03-2022 - Published the article.
Websites with Patchstack paid version are protected from the issue and have received a vPatch.





