
RomethemeKit For Elementor
Arbitrary Plugin Installation/Activation to RCE
This blog post is about the RomethemeKit For Elementor plugin vulnerability. If you're a RomethemeKit For Elementor user, please update the plugin to at least version 1.5.5.
✌️ Our users are protected from this vulnerability. Are yours?
Automatically mitigate vulnerabilities in real-time without changing code.
See pricingIdentify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout the RomethemeKit For Elementor plugin
The plugin RomethemeKit For Elementor, which has over 30k active installations, is one of the most popular free Elementor related plugins in the WordPress repository. The plugin is developed by Rometheme.

This WordPress plugin acts as a toolkit for Elementor website builders, offering a collection of professionally designed templates, sections, widgets, and an icon pack. It streamlines the website creation process by providing pre-made layouts and design elements, reducing the need for extensive design skills and coding.
The security vulnerability
The RomethemeKit For Elementor plugin suffered from an authenticated Arbitrary Plugin Installation/Activation to RCE vulnerability. The vulnerability occurred due to a lack of permission and nonce check when installing and activating a plugin. Due to the behavior of the plugin installation and activation, this vulnerability could lead to Remote Code Execution if a malicious plugin is installed or activated. The vulnerability is fixed in version 1.5.5 and has been tracked with CVE-2025-30911.
The underlying vulnerability exists in the install_requirements function:
public function install_requirements()
{
include_once ABSPATH . 'wp-admin/includes/plugin.php';
include_once ABSPATH . 'wp-admin/includes/file.php';
include_once ABSPATH . 'wp-admin/includes/misc.php';
include_once ABSPATH . 'wp-admin/includes/class-wp-upgrader.php';
$plugin = $_POST['plugin'];
$plugin_file = WP_PLUGIN_DIR . '/' . $plugin;
$plugin_slug = dirname($plugin);
if (file_exists($plugin_file)) {
// Activate the plugin if already installed but inactive
ob_start();
activate_plugin($plugin);
ob_clean();
ob_end_clean();
wp_send_json_success("Install and Activate Successfully");
} else {
ob_start();
$plugin_download_url = "https://downloads.wordpress.org/plugin/{$plugin_slug}.latest-stable.zip"; // Adjust URL structure
$upgrader = new \Plugin_Upgrader();
$result = $upgrader->install($plugin_download_url);
if (is_wp_error($result)) {
wp_send_json_error();
}
$activate_result = activate_plugin($plugin);
if (is_wp_error($activate_result)) {
wp_send_json_error('Plugin installed but failed to activate: ' . $activate_result->get_error_message());
}
wp_send_json_success('Plugin installed and activated successfully.');
}
}The function above can be called from the wp_ajax_install_requirements hook. Since there is no proper permission and nonce check on the function, any authenticated users such as Subscriber role users are able to arbitrarily install and activate any plugin on the site, resulting to a possible Remote Code Execution (RCE).
The patch
The vendor initially made an attempt to patch the issue by adding an additional permission check on version 1.5.4. The vendor then implemented a full patch on version 1.5.5 by adding an additional nonce check. The patch can be seen below:
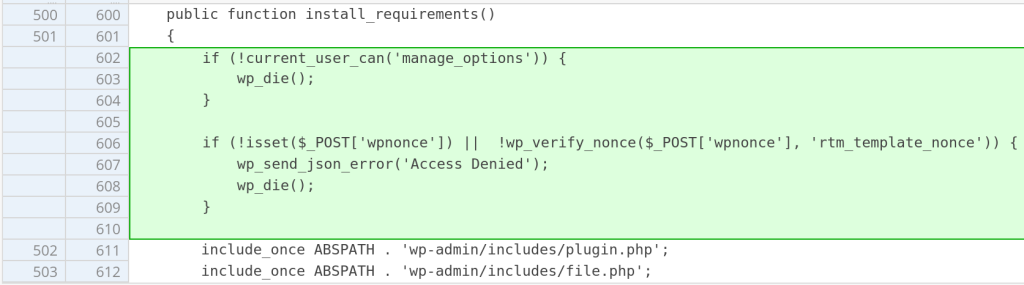
Conclusion
For a critical process such as installing and activating a plugin, make sure to implement a proper permission and nonce check.
Want to learn more about finding and fixing vulnerabilities?
Explore our Academy to master the art of finding and patching vulnerabilities within the WordPress ecosystem. Dive deep into detailed guides on various vulnerability types, from discovery tactics for researchers to robust fixes for developers. Join us and contribute to our growing knowledge base.
Timeline
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




