
Motors Theme
Arbitrary File Upload
This blog post is about a Subscriber+ arbitrary file upload vulnerability in the Motors theme. If you're a Motors theme user, please update to at least version 5.6.82.
This vulnerability was discovered and reported by Patchstack Alliance community member Denver Jackson.
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout Motors theme
The Motors theme, with over 20,000 active installations, is a theme specifically designed for building automotive websites and was developed by StylemixThemes.

The theme is a popular, feature-rich WordPress theme and plugin designed for building automotive websites, specifically car dealerships, rental sites, and classified listings for vehicles (cars, bikes, boats, etc.).
The security vulnerability
In versions 5.6.81 and below, the theme is vulnerable to arbitrary file upload, due to allowing any logged-in user to arbitrarily install and activate plugins on the site. This means any Subscriber or higher user is able to inject malicious code through the plugin installation and activation and leading to a full site takeover.
This vulnerability has been patched in version 5.6.82 and is tracked with CVE-2025-64374.
The root cause of the issue lies in the mvl_theme_install_base function:
add_action( 'wp_ajax_mvl_theme_install_base', 'mvl_theme_install_base' );
function mvl_theme_install_base() {
check_ajax_referer( 'mvl_theme_install_base', 'nonce' );
$response = array();
$plugin_url = sanitize_text_field( $_GET['plugin'] );
$plugin_slug = 'motors-car-dealership-classified-listings';
ob_start();
require_once ABSPATH . 'wp-load.php';
require_once ABSPATH . 'wp-admin/includes/class-wp-upgrader.php';
require_once ABSPATH . 'wp-admin/includes/class-plugin-upgrader.php';
require_once ABSPATH . 'wp-admin/includes/plugin-install.php';
require_once ABSPATH . 'wp-admin/includes/plugin.php';
require_once ABSPATH . 'wp-admin/includes/class-wp-upgrader-skin.php';
require_once get_template_directory() . '/inc/install_plugin/stm_upgrader_skin.php';
$plugin_upgrader = new Plugin_Upgrader( new Motors_Theme_Plugin_Upgrader_Skin( array( 'plugin' => $plugin_slug ) ) );
$installed = ( mvl_theme_check_plugin_active( $plugin_slug ) ) ? true : $plugin_upgrader->install( $plugin_url );
mvl_theme_activate_plugin( $plugin_slug );
$response['message'] = ob_get_clean();
$response['url'] = admin_url( 'admin.php?page=mvl_plugin_settings' );
wp_send_json( $response );
}First, we notice that there is a nonce check using the check_ajax_referer function. However, the mvl_theme_install_base nonce value itself can be fetched from Subscriber role users on the wp-admin base page.
Since there is no proper permission check on the function, users can just supply arbitrary plugin code from any URL via the $_GET['plugin'] parameter, and the plugin will be installed or activated.
The patch
In version 5.6.82, the vulnerability is mitigated with the addition of a current_user_can permissions check, ensuring that only legitimate, privileged users are allowed to use this AJAX action.
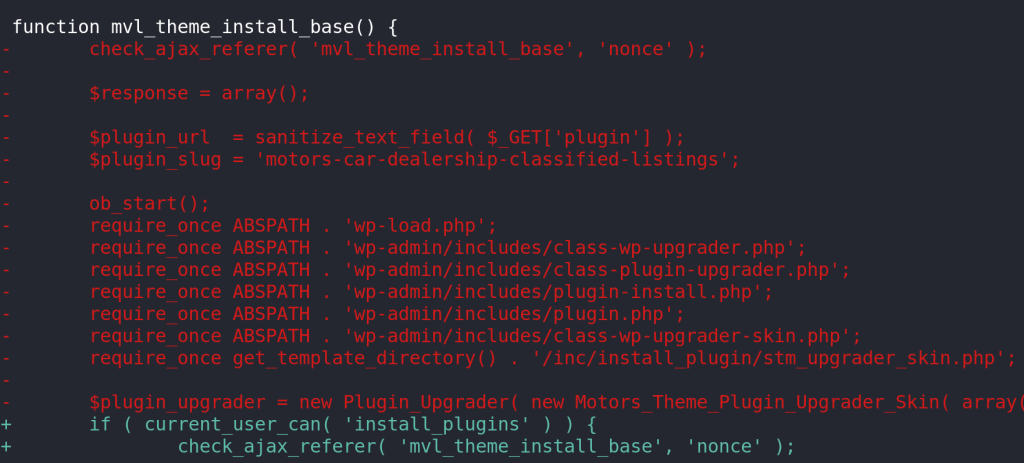
Conclusion
Nonce validation is essential for any site functionality that can cause changes, and a lack of nonce validation can lead to other vulnerabilities, such as CSRF attacks.
However, like the WordPress developer documentation says:
Nonces should never be relied on for authentication, authorization, or access control. Protect your functions using current_user_can() and always assume that nonces can be compromised.
Even when limited to only showing to the correct users, a nonce is not a substitute for proper user validation, as the risk of compromise always exists. And when shown more broadly, such as in this case, it leads to a common problem in many WordPress components, where access control is only limited by who can click the View Page Source button and find a nonce hiding in there.
Privileged functionality should always be specifically validating permissions, and cannot just assume that only the correct users will have the needed nonce.
Want to learn more about finding and fixing vulnerabilities?
Timeline
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




