As the leading threat intelligence provider in the WordPress ecosystem, Patchstack has more experience with validating reports and coordinating vulnerability disclosures than anyone else. Because of this, hundreds of WordPress plugin vendors have chosen to trust Patchstack to manage their vulnerability disclosure programs.
Setting up a vulnerability disclosure program (VDP) is going to be mandatory by the EU laws (CRA) starting from June 2026.
However, not every vendor has the in-house security expertise, and that’s where having a VDP managed by a security company comes with many benefits.
The goal of a VDP is to set a clear framework and an internal process on how external reporters must send vulnerability reports and how the software vendor then processes them. It’s an industry standard and a baseline for ethical disclosure that all security companies, ethical hackers, and security researchers should respect.
An automated way to handle mis-reported vulnerabilities
Ever since we launched the Patchstack mVDP for WordPress plugins in 2023, we have noticed that not all reporters follow the ethical disclosure principles. Some intentionally ignore the VDPs set up by the vendors and don’t go through the process the vendors have specifically set up for vulnerability reporting.
As the goal of the VDPs is to have a strict framework of how vulnerabilities are being reported and so all vulnerabilities go through the same process - external reporters who don’t respect the VDPs are not just unethical, but also create unnecessary confusion and can introduce potential security risks where mis-reported vulnerabilities fall out of an internal security policy and processes.
Until today, vendors have forwarded such reports to Patchstack manually, so we could assist them and add them to their Patchstack mVDP platform.
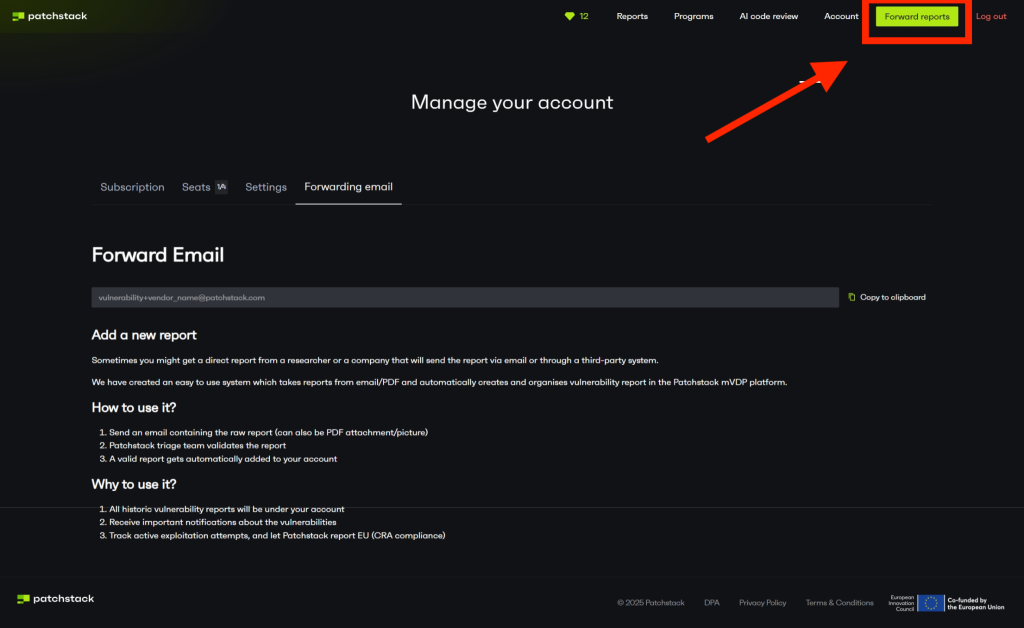
To make this process more streamlined, we’ve now launched a new report forwarding system where mis-reported security vulnerabilities can be automatically pulled into the Patchstack mVDP platform, by just forwarding the email report, screenshot or a PDF.
You will now find a “Forward reports” button on your mVDP dashboard with a dedicated forward email. All forwarded reports will be automatically standardized, validated by Patchstack, and then added under the vendor mVDP dashboard for status tracking and exploitation monitoring.
A few extra tips on how to deal with unethical reporters
We’ve seen it all.
Beg bounty reporters (researchers who report very low impact security “issues” and ask beg for a bounty even if the company has no bounty program), straight up unethical researchers who drop vulnerabilities publicly before reporting it to vendors, and security companies who don’t follow the VDPs and aggressively enforce vendors to sign up to their product to access vulnerability details.
Here are a few tips on how to deal with cases like that:
1) If you’re unsure if a vulnerability report is valid, ask a trusted security expert to validate it before you reply to the reporter.
2) Have clear information on your website and software readme file on how all vulnerabilities should be reported to avoid situations where a researcher can claim there was nowhere to report.
3) If a reporter is not respecting your VDP and asking you to sign up for their services to see the vulnerability report, just ask for the report to be sent to a secure email, which you can then forward to your VDP system.
Don’t have a VDP? Consider the free Patchstack-managed VDP
Top WordPress plugin companies such as Elementor, YITH, StellarWP, and many, many others have chosen Patchstack as their managed VDP provider.
Patchstack manages your VDP, helps coordinate vulnerability disclosure with a goal to minimize negative impact, and helps to secure your codebase with an AI code review tool and auditing.
All the important information can be found here: https://patchstack.com/for-plugins/





