This blog post is about an unauthenticated arbitrary file upload in the TI WooCommerce Wishlist plugin. If you're a TI WooCommerce Wishlist user, please update the plugin to at least version 2.10.0 (Update: 5th June 2025).
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout TI WooCommerce Wishlist plugin
The plugin TI WooCommerce Wishlist, which has over 100,000 active installations, allows WooCommerce store owners to add wishlist functionality to their shops. The plugin can also integrate with other WooCommerce extensions such as WC Fields Factory to enable custom fields and enhanced forms.

The security vulnerability
In version 2.9.2 and below, the plugin is vulnerable to an arbitrary file upload vulnerability, which allows attackers to upload malicious files to the server without authentication. The vulnerability is now patched in version 2.10.0 and is tracked with CVE-2025-47577.
The root of the issue lies in the tinvwl_upload_file_wc_fields_factory function:
function tinvwl_upload_file_wc_fields_factory( $file ) {
if ( ! function_exists( 'wp_handle_upload' ) ) {
require_once( ABSPATH . 'wp-admin/includes/file.php' );
}
$upload = wp_handle_upload(
$file,
[
'test_form' => false,
'test_type' => false,
]
);
return $upload;
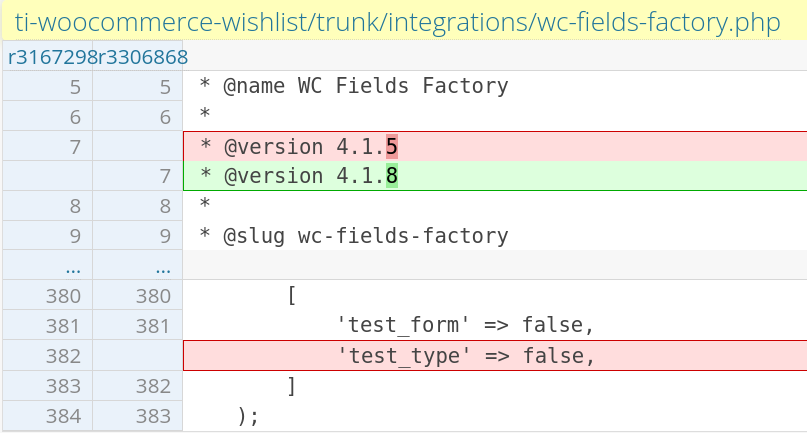
}This function utilizes WordPress’s wp_handle_upload, which normally performs file type validation. However, by explicitly setting 'test_type' => false, this validation is bypassed, allowing any file type (including executable PHP files) to be uploaded. Using an empty string ('') for 'test_type' would also bypass validation, although we have not observed any real-world usage of that variant in this case.
The vulnerable function is accessible via tinvwl_meta_wc_fields_factory or tinvwl_cart_meta_wc_fields_factory, which are only available when the WC Fields Factory plugin is active.
A typical attack involves uploading a malicious PHP file, allowing the attacker to then trigger remote code execution (RCE) by directly accessing the uploaded file.
Note that the vulnerability is only exploitable if the WC Fields Factory plugin is activated and the integration is enabled on the TI WooCommerce Wishlist plugin.
The patch
The vendor decided to remove the test_type parameter from the wp_handle_upload() process (Update: 5th June 2025). The patch can be seen here.
Conclusion
To address the vulnerability, plugin developers should immediately remove or avoid setting 'test_type' => false when using wp_handle_upload().
This ensures that only safe file types (such as images or documents) are accepted during the upload process, preserving WordPress’s default security behavior.
Want to learn more about finding and fixing vulnerabilities?
Explore our Academy to master the art of finding and patching vulnerabilities within the WordPress ecosystem. Dive deep into detailed guides on various vulnerability types, from discovery tactics for researchers to robust fixes for developers. Join us and contribute to our growing knowledge base.
Timeline
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more





