This blog post gives information and a step-by-step guide on how to act and clean your site after your website is flagged for malware by Google.
Google is very proactive when it comes to protecting the safety of its customers. They scan millions of websites each day, looking for spyware, viruses, and other kinds of dangerous malware that may put their users at risk.
Once Google has identified malware on a website, it will flag it as being a risk for visitors. This warning will be shared across all Google products, affecting how it appears in Google search engine results, Google Chrome, Google Adwords, and other Google products.
For website owners, having a site flagged for malware is a very nasty surprise that can cause significant damage. It may dramatically reduce web traffic, kill your business’s online profits, negatively impact search engine rankings, and get listed on a Google blacklist.

Fortunately, fixing this issue is fairly straightforward. This guide will explain what malware is and why your website may have been flagged. Then, we will tell you what to do if your website is flagged for malware by Google.
What is malware?
Malware is short for malicious software. It refers to any piece of software that is intentionally designed to damage a server, computer, or computer network.
Malware can come in many forms including executable applications, scripts, and executable files. Hackers often attempt to place malware on websites with the following objectives in mind:
- Stealing traffic from your website by redirecting it elsewhere
- Obtaining confidential information from your website or visitors to your website
- Stealing money from your website
- Improving the SEO of one of their own websites by injecting links into your site
- Creating spam pages
- Vandalizing your website by deleting or replacing data
- Making fraudulent purchases on your website
- Launching denial of service attacks
Malware is often inserted into a website after a successful brute force attack, Cross-Site Scripting (XSS) attack, or SQL injection attack.
It might also be added to your website via a vulnerability in a content management system, theme, or plugin.
There are many types of malware including:
- Spyware
- Viruses
- Adware
- Ransomware
- Keyloggers
- Rootkits
- Trojans
- Worms
Why would Google flag my site for malware?
The most common reason for a website being flagged for malware by Google is that your website has been hacked. A hacker might have installed malicious files to which visitors to your website are exposed.

In some cases, hackers might simply add a redirect to send visitors coming to your website to another location containing malware.
Another possibility is that another website has been hacked and you are using some of that website’s content via an iFrame, JavaScript, or PHP inclusion. This kind of problem is relatively simple to fix as you can just exclude that content from your pages.
Finally, Google might flag your website if it is linking to another website that contains malware. You will need to identify which links go to the compromised website and remove them.
What does a Google malware warning look like?
If Google has flagged your website as containing malware, it will immediately take steps to protect its customers. The most significant change relates to how your site appears in Google search engine results.
When your website appears in Google’s results, it may also display a warning that says "This site may harm your computer."
Google will also display warnings on websites that it suspects are phishing. Phishing is an attempt to gather sensitive information like usernames, passwords, and credit card details from users by fraudulent means.
These warnings may also be displayed if the advertisements on your website are determined to be malicious. In Google Chrome, this warning looks like this:
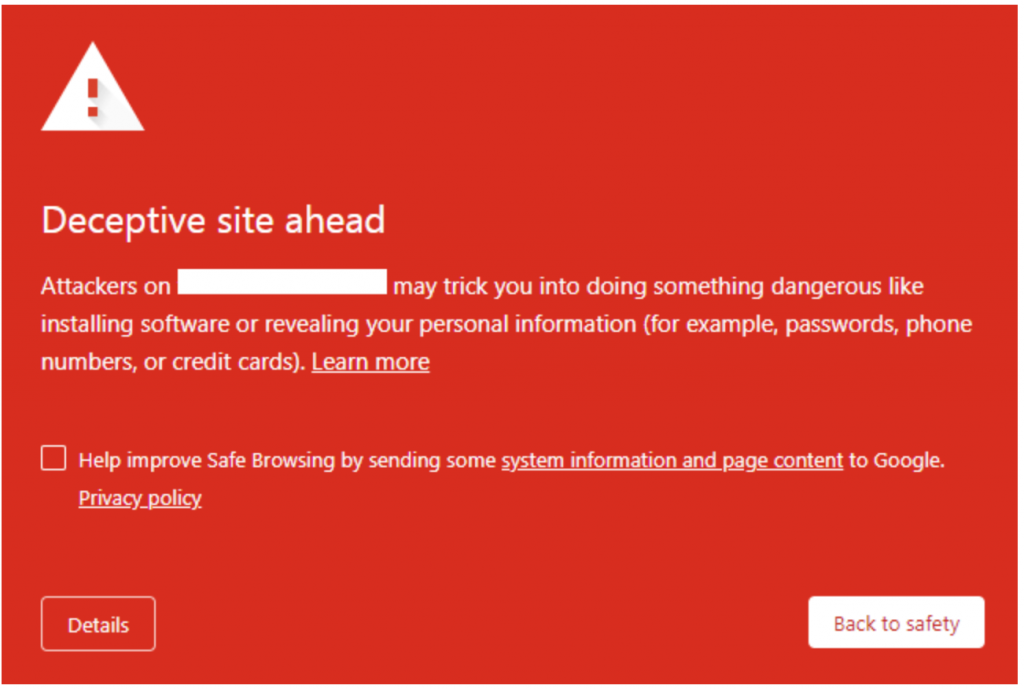
This type of warning is usually triggered by a website having redirects to unsafe content or spam pages. In some cases, this warning will appear if your website has been hacked and is being used to distribute malware.
When someone clicks on your link in Google’s search engine results, they may also be redirected to a Website Malware Warning. They must read this warning and click Ignore this warning or View details to get through to your website.
This warning typically causes websites to lose about 95% of their Google search traffic. It will look different based on the web browser you are using.
Website malware warning in Google Chrome:
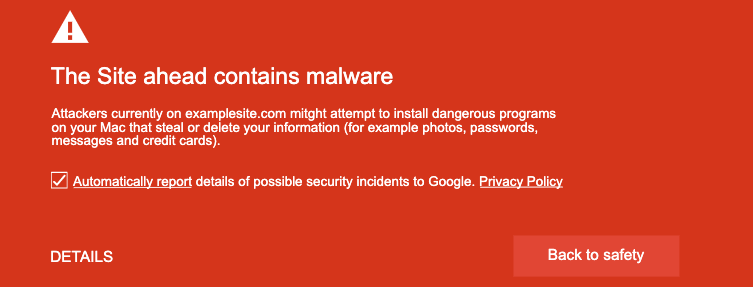
Google uses a variety of terms to tell customers that a website has been infected with malware, including:
- The website ahead contains malware
- Danger malware ahead
- The site ahead contains harmful programs
- The site ahead contains malware
- Reported attack page
- Suspected malware site
- This website has been reported as unsafe
- Deceptive site ahead
- Suspected phishing site
- Website request forgery
- This site may be hacked
- This site may harm your computer
- Unwanted software
Users of Google Search Console, Google Analytics, or Google Adsense may also receive separate warnings about the presence of malware on their websites.
This usually includes email warnings from Google and notifications in the dashboard sections of the Search Console, Analytics, or Adsense.
What to do if your website is flagged for malware?
There are several steps you need to take if your website is flagged for malware. The steps include identifying why it is flagged by reviewing your site, cleaning the site for malware, and more. Let's look into it step-by-step.
Step 1: Identify why your website is flagged by Google
There are multiple ways to discover why your website was flagged for malware.
Review diagnostic pages
If your website has one of the large Website Malware Warnings listed above, you can click on More Information, Details, or Why Was This Website Blocked to learn more about the cause of the problem.
You can also check your website’s status via the Google Safe Browsing site status page. Simply type in your domain name and hit enter to perform a search. Google will return Site Safety Details and Testing Details.

The Site Safety details will tell you if malicious content has been found on your website and where that content is located. It might be a list of malicious files on your domain or pages that contain spam content.
It could also be an external script, unauthorized redirect, hidden iframe, or another external source of malware that is affecting your website.
The Testing Details section will tell you the discovery date of the malware and the last scan date. This can help you identify files that are affected as you can perform a search for files modified after a certain date.
If you have added your site to Google Search Console (highly recommended), you will have already received details of any malware present.
To take a closer look at the issues that Search Console has found, click on the Security Issues link. It will list all issues by category.
You can click 'Show details' to take a closer look at a particular issue.
For each problem, Google will share a list of affected URLs, damaged pages, and the type of damage that has been caused. Copy this information into a text document so you can easily refer to it later.
Another method for checking which pages may have been infected is by searching for site:yoursite.com in Google (replace yoursite.com with your domain name).
Any page that has the text This site may harm your computer may have malware on it. This is a useful step for identifying infected pages or new pages added by a hacker.

Google uses the following categories for malware and hacked websites on their Website Malware Warning pages, in Google Search Console, and in Google Safe Browsing listings:
- Social Engineering (Phishing and Deceptive sites)
- Your website contains content that is attempting to trick visitors into divulging sensitive information.
- Malware infection type: Server configuration
- A hacker has compromised your website and is redirecting visitors to their malware-infected website.
- Malware infection type: SQL injection
- This means your website’s database is probably compromised via an SQL injection attack.
- Malware infection type: Code injection
- Pages on your website have been modified to include malicious code. This is often done via an iframe containing a malware attack site.
- Malware infection type: Error template
- This will occur if the page that appears for error messages and missing pages has been altered to contain malware.
- Cross-site malware warnings
- Your website may be including content from another website that is flagged by Google for having malware
Step 2: Fix your website
The next step is to remove the malware from your website. You may need to perform additional scans to determine where the malware is located on your website and database.
This can be a complicated process, so it is often worth enlisting the help of a specialist.
Preparation
Create a new text document that you will use to keep track of the types of malware warnings that you have received, the affected URLs, and any other useful information.
Avoid visiting your website during this process, as you may spread the malware onto your computer. Instead, review pages using the Google Safe Browsing site and Google Search Console.
You can also use third-party site scanning products. They may provide you with additional information about the malware on your website and any security issues that are present.

When you need to examine a web page to check its content or to remove malicious content, do so with SFTP or SSH. Visiting the website via a web browser before you have removed any malware could make the problem worse.
You should make a backup of your website’s files and database before you begin this process. This will ensure that you can undo any accidental erasure of data or files.
Scan your website for malware
Perform a scan of your website using some of the third-party tools listed above. This will help you identify malware locations, security issues, malicious payloads, and blacklist status with major authorities.
Make a note of malicious payload and file locations found by these programs.
These scans will help you determine if your website has been flagged by other security authorities. Once you have fixed your website, you may need to contact each authority to have your site removed from their blacklists.
You should also perform a scan of your website using a server-side antivirus application like ClamAV. This application will identify and remove most types of malware for you.
However, it is important to understand that a website vulnerability or backdoor may still exist after the malware has been removed. This vulnerability or backdoor will require manual patching.
Remove file infections
Start by deleting any malware payloads on your domain that have been identified by your security scans. Malware payloads are usually standalone files inserted into pages or distributed to website visitors.
You may also have new pages added to your website which are full of malware or spam. Delete these files by logging into your server via SFTP or SSH and manually removing them.

If the scans have found that the pages of your website have been modified to include malware or redirect to a malware-infected page, you have two options for dealing with them.
Replace the files with versions you know are safe
If you are using a content management system like WordPress or Joomla, you can download source files from a trustworthy source and replace the infected files.
If you have an old backup of your website that you know is clean of malware, you can also use that.
Manually review the files to remove malware
You can manually log into your website using SFTP or SSH, then manually review each of the files to determine its authenticity and validity.
Start by sorting your file system by date. If there are new files that you don’t recognize, they may be a part of the malware distribution system installed by the hacker.
Manually check the files that are a part of your website for any alterations.
If you decide to manually review your website’s files and have a safe backup available, you can make the process faster. Log into your web server and use the diff command to compare your safe backup to the current website.
The command that will be used is:
diff -qrSo if your current website is located in the www directory and your backup website is in the backups/trusted-backup folder, use the command:
diff -qr x current-site /backups/trusted-backup/You will receive a list of the modifications that have been made to your website’s files.
If the reports provided by Google or third-party security scans have identified a URL associated with malware, you can also search for that URL in your files.
This may help you locate the page that is redirecting to that malware website or including its content.
When you perform this file review, remember that you aren’t just looking for malware. You are also looking for the backdoor that the hacker may have used to gain entry into the website.
Check your server’s logs
Checkin the server, access, and error logs will help you learn more about how your website was infected. You might notice a new user has been logging into the server and you can check what commands they have been running.
Clean hacked database tables
If hackers have gained full access to your file system, they may have also inserted malware into your database. Tracking down modifications to your database may be time-consuming, but it must be done.
- Log into your database administration panel (using PHPMyAdmin, Search-Replace-DB, or Adminer)
- Backup the database before making changes
- Search for content that is suspicious. This might be URLs of malware websites, spam keywords, posts by certain users, etc.
- Open the affected tables and manually review the database content
- Check that the site still works after your modifications
- Pay close attention to tables that hold login details for administrators — the hacker may have added new admin users.
Alternatively, you could restore an old database backup that you know is safe.
Follow Google’s advice on specific malware types
Google provides advice on their preferred method for cleaning each malware type. By following this advice, you can ensure that you have complied with their requirements.
- Server configuration
- SQL injection
- Error template
- Code injection
Tighten security on your website
Once you have identified and removed the malware, take steps to improve the security of your website.
- Make sure an antivirus scanner like AVG or Clam is continually running on your web server.
- Update the web server’s operating system and software.
- Update the content management system you are using, along with any themes or plugins. Remove unused themes and plugins.
- Update passwords for server users, databases, FTP users, and CMS users.
- Harden your file permission levels
- If you are using a CMS like WordPress, install a WordPress security tool.
- Install a WordPress theme-checking plugin like Theme Check.
- Change to a web host with tighter security procedures.
- Harden your PHP and MySQL installations.
- Ensure that regular backups of both files and databases are being performed.
- Install an antivirus on your personal computer to prevent it from infecting your website. Eset, BitDefender, Sophos, F-Secure, Malwarebytes, Avast, Microsoft Security Essentials, and Avira are all good choices.
Step 3: Request a review of your website
Once you are certain that any malware and backdoors have been removed from your website, request a review from Google.
- Open Google Search Console (log in or create an account)
- If you haven’t added or verified your website, do it now
- Navigate to the Security Issues tab
- Review the issues to ensure they have all been addressed
- Check the box to confirm I have fixed these issues
- Click Request Review
- Give Google details of how you cleaned your website
It’s important to understand that your website will only be eligible for one review every 30 days.
If you haven’t successfully removed the malware from your website, a failed review may mean a long wait. It usually takes a few days for Google to review a website.
Once your website has been reviewed and given the all-clear, you should also have Google re-crawl it.
- Head over to Search Console again
- Click the Fetch as Google section
- Enter your URL and click Fetch
- Click Submit to Index
- Check the I am not a robot button
- Choose the option Crawl this URL and its direct links
- Click go
Thanks for reading, for more advice on handling malware contact our team via live support on our website.
What is malware?
Malware is short for malicious software. It refers to any piece of software that is intentionally designed to damage a server, computer, or computer network.
Why do hackers put malware on websites?
Hackers often attempt to place malware on websites with the following objectives in mind:
- Stealing traffic from your website by redirecting it elsewhere
- Obtaining confidential information from your website or visitors to your website
- Stealing money from your website
- Improving the SEO of one of their own websites by injecting links into your site
- Creating spam pages
- Vandalizing your website by deleting or replacing data
- Making fraudulent purchases on your website
- Launching denial of service attacks
How to request review from Google after removing from blacklist?
Once you are confident that any malware and backdoors have been removed from your website, request a review from Google.
- Open Google Search Console (log in or create an account)
- If you haven’t added or verified your website, do it now
- Navigate to the Security Issues tab
- Review the issues to ensure they have all been addressed
- Check the box to confirm I have fixed these issues
- Click Request Review
- Give Google details of how you cleaned your website
It’s important to understand that your website will only be eligible for one review every 30 days.
What does it mean "security vendor flagged this url as malicious"?
It means that your site may have been compromised and is flagged for malware. You now need to identify the breach, clean the site, and request a review to fix the issue.
What does malware do on a website?
Malware can collect data, redirect visitors, steal credit card info or confidential info from your customers, infect computers and phones, and much more.





