WordPress 6.4.2 has been released on December 6th, 2023, which includes an important security fix.
This security fix addresses a potential security issue that can only be exploited if another vulnerability (PHP object injection) is already present on your WordPress site. This was originally introduced in version 6.4.0 of WordPress and was also available in version 6.4.1 of WordPress core.
We highly recommend you update your site to version 6.4.2 as soon as possible, even if you are not running version 6.4.0 or 6.4.1. Sites that have any plugins or themes installed that contain a PHP object injection vulnerability are especially at risk, so it should be a high priority to update WordPress on your site as soon as possible!
Technical analysis
In version 6.4.0 of WordPress, a new class called WP_HTML_Token was introduced with a __destruct() function that can call any callable function.
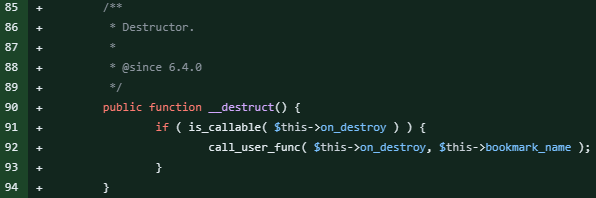
At first sight, this may not be interesting, but in combination with a PHP object injection vulnerability, this can be exploited to execute arbitrary PHP functions on the WordPress site. If you want to learn more about PHP object injection, visit this blog post.
Since an exploitation chain was made available several weeks ago on GitHub and added to the PHPGGC project, it has made it significantly easier for malicious users to exploit any PHP object injection vulnerability present on a website.
If you are a developer and any of your projects contain function calls to the unserialize function, we highly recommend you swap this with something else, such as JSON encoding/decoding using the json_encode and json_decode PHP functions.
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




