WordPress 6.4.3 was released on January 30th, 2024, which includes two low-severity security fixes.
This security fix addresses two potential security issues. The first one is an Administrator+ arbitrary PHP file upload on the plugin and theme upload functionality. The second issue is a potential security issue that can only be exploited if another vulnerability (PHP object injection) is already present on your WordPress site.
We highly recommend you update your site to version 6.4.3 (or one of the patched versions) as soon as possible. Sites with plugins or themes installed that contain a PHP object injection vulnerability are especially at risk, so it should be a high priority to update WordPress on your site.
Patches for the two issues have been backported to version 4.1 and later on the WordPress Core.
Technical analysis
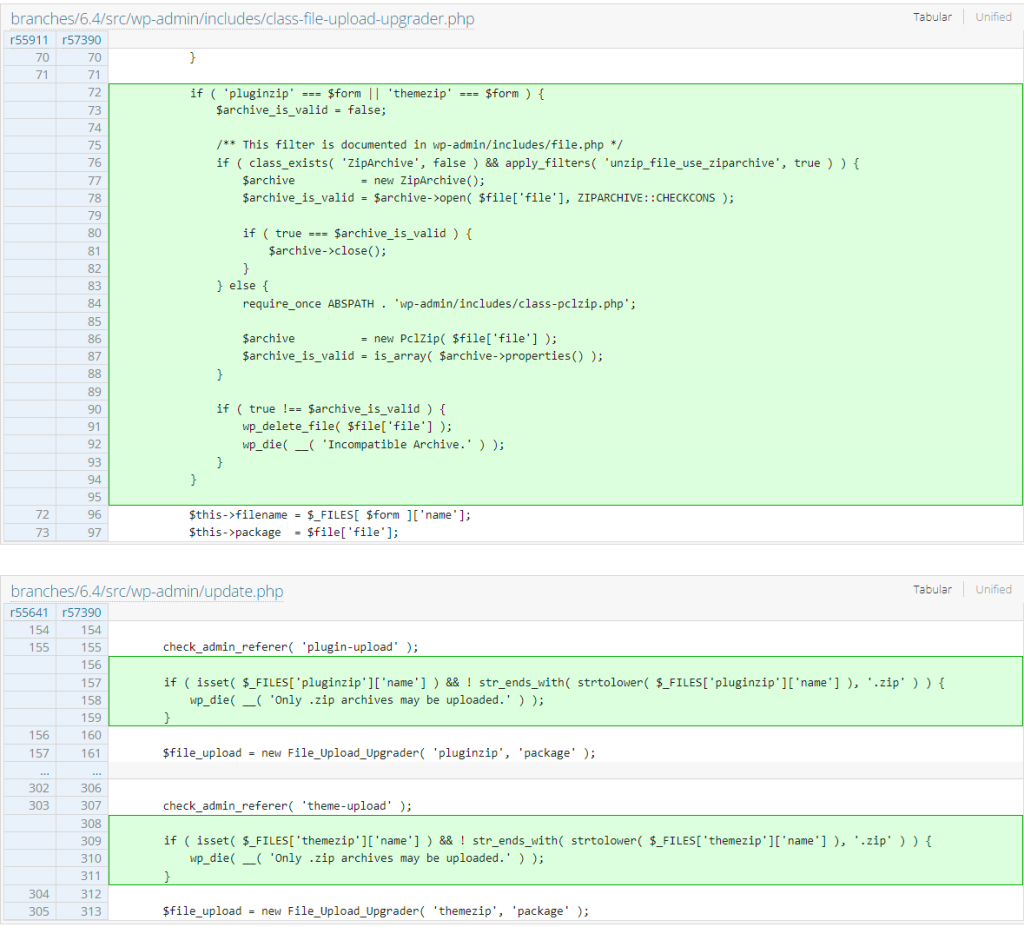
Administrator+ Arbitrary PHP File Upload
This security issue has existed since 2018. This allows the Administrator user role and Super Admin user role on multisite environments to upload PHP files directly to the site through the plugin and theme upload functionality. Note that this is only an issue if the site is implementing a process to limit the Administrator and Super Admin user role to upload a plugin or theme. The patch for this issue can be seen below:
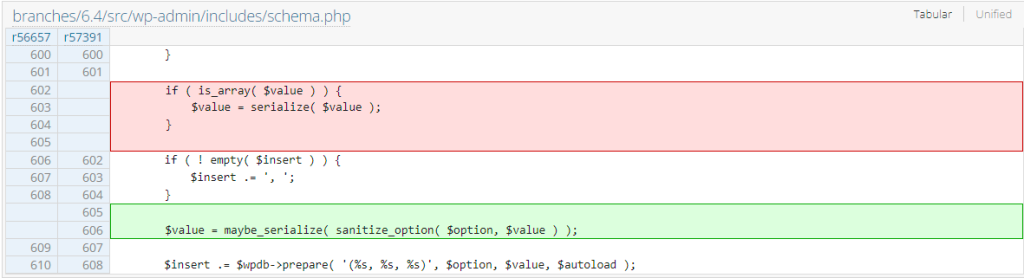
Potential PHP Object Injection Gadget
This potential security issue will not make it into our vulnerability database as this can become exploitable only if a PHP object injection exists somewhere on the targeted WordPress site.
According to the release article, the Core team patched a potential PHP object injection gadget that could be used to gain Remote Code Execution (RCE) on the WordPress site. We notice that there is a change in how the options are stored. The process now involves sanitization using the sanitize_option function before applying another serialization process using the maybe_unserialize function. The option sanitization apparently doesn't get implemented during site installation and upgrade process in older versions. The patch can be seen below:
Since the two issues require a very high permission role or an incomplete site installation or upgrade process, there is only a very small chance that these issues will be exploited in a real-world case.
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




