This blog post is about an unauthenticated Broken Authentication vulnerability in the Jobmonster theme. If you're a Jobmonster theme user, please update the theme to at least version 4.8.0.
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout the Jobmonster Theme
The Jobmonster theme, which has over 5,000 sales, is a premium WordPress theme designed to build job boards, recruitment, and resume‐portal websites. It aims to be an all-in-one solution connecting employers and candidates, with front-end submission, profile management, monetization, and search/filtering capabilities.

The security vulnerability
A broken authentication vulnerability was identified in the Jobmonster theme. An unauthenticated attacker can exploit this issue to bypass authentication controls, gaining elevated access to protected functionality or accounts without the need for valid credentials. The issue has been assigned CVE-2025-54738.
The theme exposes an AJAX action that returns session data for an arbitrary user identifier supplied by the attacker. The handler does not enforce nonce verification capability checks or require that the requester is authenticated. As a result, an unauthenticated POST to admin-ajax.php can return session information tied to the supplied admin email, enabling account impersonation:
The root of the issue lies in the check_login function:
public function check_login() {
[...]
// simplified vulnerable logic
switch ( $_POST['using'] ) {
case 'fb':
// set $user_email from Facebook response
break;
case 'google':
// set $user_email from Google response
break;
// ... other providers ...
default:
// do nothing (no provider data)
break;
}
[...]
$user_email = !empty($user_email) ? $user_email : (!empty($_POST['id']) ? esc_attr($_POST['id']) : '');
if( empty( $user_email ) ) :
$response['status'] = 'not_user';
$response['message'] = esc_html__('User not being registered.', 'noo');
wp_send_json( $response );
endif;
$user = get_user_by( 'email', $user_email );
if( $user ) :
$user_id = $user->ID;
wp_set_auth_cookie( $user_id, true );
$response['status'] = 'success';
$response['message'] = esc_html__('Login successfully.', 'noo');
wp_send_json( $response );
else :
$response['status'] = 'not_user';
$response['message'] = esc_html__('User not being registered.', 'noo');
wp_send_json( $response );
endif;
}Because the default case simply allowed execution to continue (no error or early return), an attacker could:
- Submit any $_POST['using'] (including a random or unsupported value) so the switch drops to default.
- Supply $_POST['id'] containing a victim email.
The patch
Site owners must update the Jobmonster theme to version 4.8.0 or later immediately. The vendor provided fix in 4.8.0 addresses the broken authentication logic and prevents the unauthenticated bypass:
file: framework/add-ons/social-login/class-social-login.php
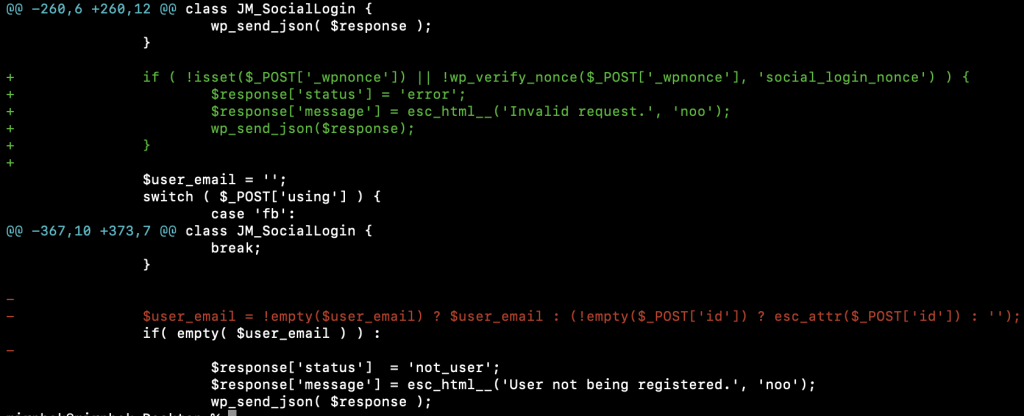
- The theme no longer accepts a user email from $_POST['id']. $user_email is now set only from validated social-provider responses (the code path inside the switch($_POST['using'])), so an attacker cannot directly supply an arbitrary email via POST.
- The insecure fallback that allowed arbitrary $_POST['id'] to be used as $user_email was removed
Together, these changes close the reported broken authentication vulnerability.
Want to learn more about finding and fixing vulnerabilities?
Explore our Academy to master the art of finding and patching vulnerabilities within the WordPress ecosystem. Dive deep into detailed guides on various vulnerability types, from discovery tactics for researchers to robust fixes for developers. Join us and contribute to our growing knowledge base.
Timeline
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more





