There is a vulnerability in the OceanWP theme - Subscriber+ Path Traversal Leading to Local File Inclusion in <= 3.4.1 If you're an OceanWP user, please update the theme to at least version 3.4.2.
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout the OceanWP Theme
The theme OceanWP (versions 3.4.1 and below, free version), which has over 700,000 active installations is known as one of the most popular free themes on WordPress.

This theme is considered to be lightweight and highly extendable, it will enable us to create almost any type of website such as a blog, portfolio, business website, and WooCommerce storefront with a beautiful & professional design.
The security vulnerability in OceanWP theme
The OceanWP theme suffers from an authenticated Local File Inclusion (LFI) vulnerability. This vulnerability allows any authenticated user with a minimum Subscriber user role to perform local file inclusion with a limited .php file extension on the WordPress server. The described vulnerability was fixed in version 3.4.2 and assigned CVE-2023-23700.
Check this vulnerability in the Patchstack vulnerability database.
This is the first vulnerability I personally found in a WordPress theme. Generally, if we compare plugins and themes, we can see that themes tend to process user input much less frequently than plugins. This causes much fewer vulnerabilities to exist in themes than in plugins.
The initial discovery of this vulnerability happened when we analyzed a few of the wp_ajax actions in the theme. One of the wp_ajax actions available is wp_ajax_oceanwp_cp_load_pane_action which will load the theme panel pane. This action is handled by the load_theme_panel_pane function:
/**
* Load the pane by the slug name.
*
* This function is called via admin-ajax.php.
*/
public function load_theme_panel_pane() {
$slug = esc_attr( $_POST['slug'] );
ob_start();
$this->print_pane( $slug );
$pane_html = ob_get_clean();
$pane_html = '<div class="oceanwp-tp-preloader"><div class="oceanwp-tp-loader"></div></div>' . $pane_html;
wp_send_json_success( $pane_html );
wp_die();
}The function first will assign the $_POST['slug'] value that previously applied esc_attr function to the $slug variable. The code then will call $this->print_pane function with $slug variable as parameter.
/**
* Print pane HTML by slug.
*
* @param string $slug Pane ID.
*/
public function print_pane( $slug = '' ) {
$sections = $this->get_sections();
$default = reset( $sections );
if ( empty( $slug ) ) {
$slug = $default['href'];
}
$file = OCEANWP_THEME_PANEL_DIR . "/views/panes/{$slug}.php";
// String pattern replace.
$slug = str_replace( '-', '_', $slug );
// Get file location.
$file = apply_filters( "oceanwp_theme_panel_pane_{$slug}", $file );
if ( file_exists( $file ) ) {
include_once $file;
return;
}
}The $slug variable will be formatted to the $file variable. The code then will re-assign the $file variable with the apply_filters function. Since the value passed to the apply_filters hook name is not valid, the $file variable is not modified.
Finally, the code will check if the $file exists using file_exists function, and then will include the $file. With this condition, we are able to supply a path traversal payload to include a local arbitrary .php file.
The patch in the OceanWP theme
Since this issue is mainly because the code tries to include some part of the file path from user input, the developer decided to apply basename function on the $slug variable. The patch can be found here :
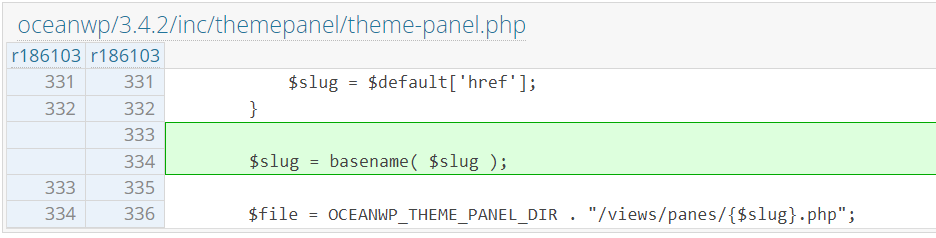
Disclosure timeline of the vulnerability in OceanWP theme
15-02-2023 - We found the vulnerability and reached out to the theme vendor.
22-02-2023 - OceanWP theme version 3.4.2 was published to patch the reported issues.
27-02-2023 - Added the vulnerabilities to the Patchstack vulnerability database.
01-03-2023 - Published the article.
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




