This blog post is about the HT Mega plugin critical vulnerability. If you're a HT Mega user, please update the plugin to at least version 2.2.1.
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout the HT Mega plugin
The plugin HT Mega (versions 2.2.0 and below, free version), which has over 100,000 active installations is known as one of the more popular Elementor addons plugin in WordPress. This plugin is developed by HasThemes.
This plugin is an Elementor addons package for WordPress. It is a complete package of widgets, pre-designed templates, forms, tables, and so on. It empowers us to build a professional website in WordPress from blog widget, slider widget, accordion widget.
The security vulnerability
This plugin suffers from an unauthenticated privilege escalation vulnerability and allows any unauthenticated user to escalate their privilege to that of any role on the WordPress site.
It is possible to register a new user account with any arbitrary role which could allow an unauthenticated user to register with administrator role which is the highest privileged role on a default site. This vulnerability occurs because the code that handle user registration process directly assign user role from user supplied input without any check and validation. The described vulnerability was fixed in version 2.2.1 and assigned CVE-2023-37999.
The underlying vulnerability is located in the function htmega_ajax_register:
function htmega_ajax_register() {
$user_data = array(
'user_login' => !empty( $_POST['reg_name'] ) ? $_POST['reg_name']: "",
'user_pass' => !empty( $_POST['reg_password'] ) ? $_POST['reg_password']: "",
'user_email' => !empty( $_POST['reg_email'] ) ? $_POST['reg_email']: "",
'user_url' => !empty( $_POST['reg_website'] ) ? $_POST['reg_website']: "",
'first_name' => !empty( $_POST['reg_fname'] ) ? $_POST['reg_fname']: "",
'last_name' => !empty( $_POST['reg_lname'] ) ? $_POST['reg_lname']: "",
'nickname' => !empty( $_POST['reg_nickname'] ) ? $_POST['reg_nickname']: "",
'description' => !empty( $_POST['reg_bio'] ) ? $_POST['reg_bio'] : "",
'role' => !empty( $_POST['reg_role'] ) ? $_POST['reg_role']: get_option( 'default_role' ),
);
$messages = !empty( $_POST['messages'] ) ? $_POST['messages']: "";
if( $messages ){
$messages = json_decode( stripslashes( $messages ), true );
}
if( htmega_validation_data( $user_data ) !== true ){
echo htmega_validation_data( $user_data, $messages );
}else{
$register_user = wp_insert_user( $user_data );
-------------------------------------- CUTTED HERE --------------------------------------Above function serves as a function handler of wp_ajax_nopriv_htmega_ajax_register ajax action. Note that $userdata variable is constructed from multiple values including the role value that is directly retrieved from $_POST['reg_role'].
There is a check using the htmega_validation_data function, but it only checks for the validity of the username, email, password and user URL. Since there is no proper check on the role value, we can specify any user role that we want when registering a new user account.
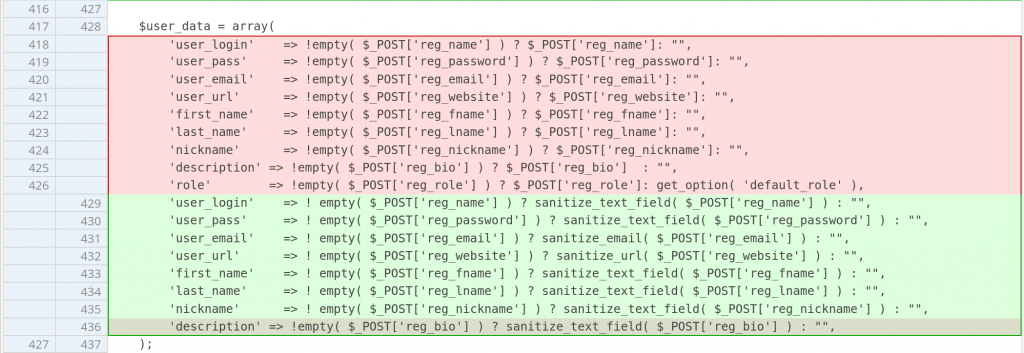
The patch
Since this vulnerability exists because the code directly assigns a role from user supplied input without proper validation, removing the direct role assignment should be enough to patch the issue. The patch can be seen below:
Conclusion
For plugin and theme developer, pay extra attention and apply additional security checks on the custom user registration handler. Always check and validate a role value if it can be directly supplied by the user. We recommend assigning default_role option as a default role value for custom user registration.
Disclosure note
Since we’ve detected that third-parties have had access to the vulnerability information via monitoring the changelog , we’ve decided to disclose the vulnerability early.
Timeline
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




