This security advisory is written about a critical Easy Digital Downloads vulnerability originally discovered by Nguyen Anh Tien and reported to us through our bug bounty program. Patchstack users have received a vPatch to protect their site against this vulnerability.
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout the Easy Digital Downloads plugin
The Easy Digital Downloads plugin is described as a plugin that gives you unlimited products with no hidden listing fees, unlimited products, unlimited transactions and provides unlimited possibilities.
Easy Digital Downloads vulnerability information
On April 21st, 2023, Nguyen Anh Tien reported a critical vulnerability to us that exists in the Easy Digital Downloads plugin versions 3.1.1.4.1 and below. This vulnerability makes it possible for any user, regardless of their current authentication and authorization, to execute any action registered with the prefix edd_.
This prefix is also present in one of the methods that performs a password reset which means it's possible to reset the password of any user as long as you know their username thus being able to reset the password of the administrator and login on their account. This vulnerability occurs because this password reset function does not validate a password reset key and instead directly changes the password of the given user.
The patch in the Easy Digital Downloads plugin
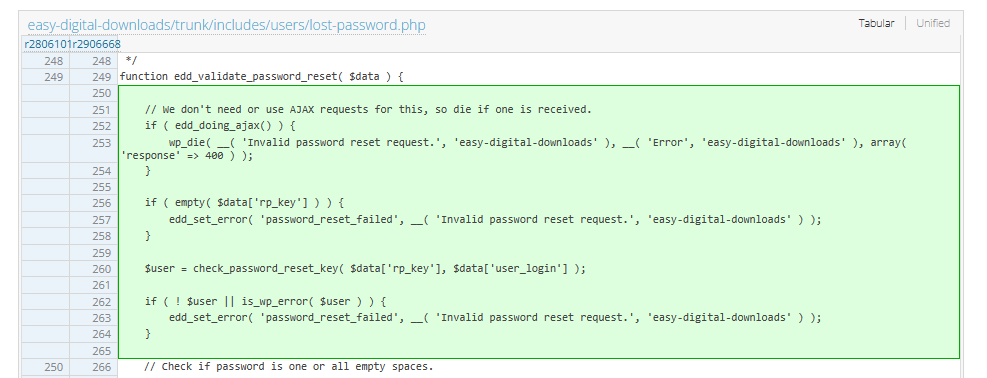
This issue occurs because we are able to call any action registered with the edd_ prefix. The patch can be seen here. This shows that the function can no longer be called directly and includes additional validation to make sure that the password reset key is present and legitimate.
Disclosure timeline
21-04-2023 - Vulnerability was reported to us by Nguyen Anh Tien.
21-04-2023 - We reached out to the developer of the plugin.
01-05-2023 - Version 3.1.1.4.2 was published to patch the reported issues.
01-05-2023 - Added the vulnerabilities to the Patchstack vulnerability database.
02-05-2023 - Published the article as the vulnerability became public knowledge.
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more




