Litho Theme
Unauthenticated Arbitrary File Deletion
This blog post is about an Unauthenticated Arbitrary File Deletion vulnerability in the Litho theme. If you're a Litho theme user, please update the plugin to at least version 3.1.
The vulnerability in the Litho theme was originally reported by Patchstack Alliance community member Tran Nguyen Bao Khanh to the Patchstack Zero Day bug bounty program for WordPress.
✌️ Our users are protected from this vulnerability. Are yours?
Identify vulnerabilities in your plugins and get recommendations for fixes.
Request auditProtect your users, improve server health and earn additional revenue.
Patchstack for hostsAbout the Litho Theme
The theme Litho, which has nearly 5,000 sales, is a creative and responsive business and portfolio, blog, and eCommerce multipurpose Elementor WordPress theme with 37+ homepages, 200+ elements, and inner pages.

The security vulnerability
The plugin suffers from an arbitrary file deletion vulnerability. As a result, an attacker can delete any file on the system using a path traversal payload. Since deletion of critical files such as wp-config.php triggers a new WordPress installation, an attacker can take over the WordPress site by deleting the configuration file to take over the website.
This vulnerability occurred because the code that handles user input didn’t have any authorization or nonce checks. An attacker can use the file deletion vulnerability that existed due to a font removal functionality. Patchstack assigned CVE-2025-49879 to this vulnerability.
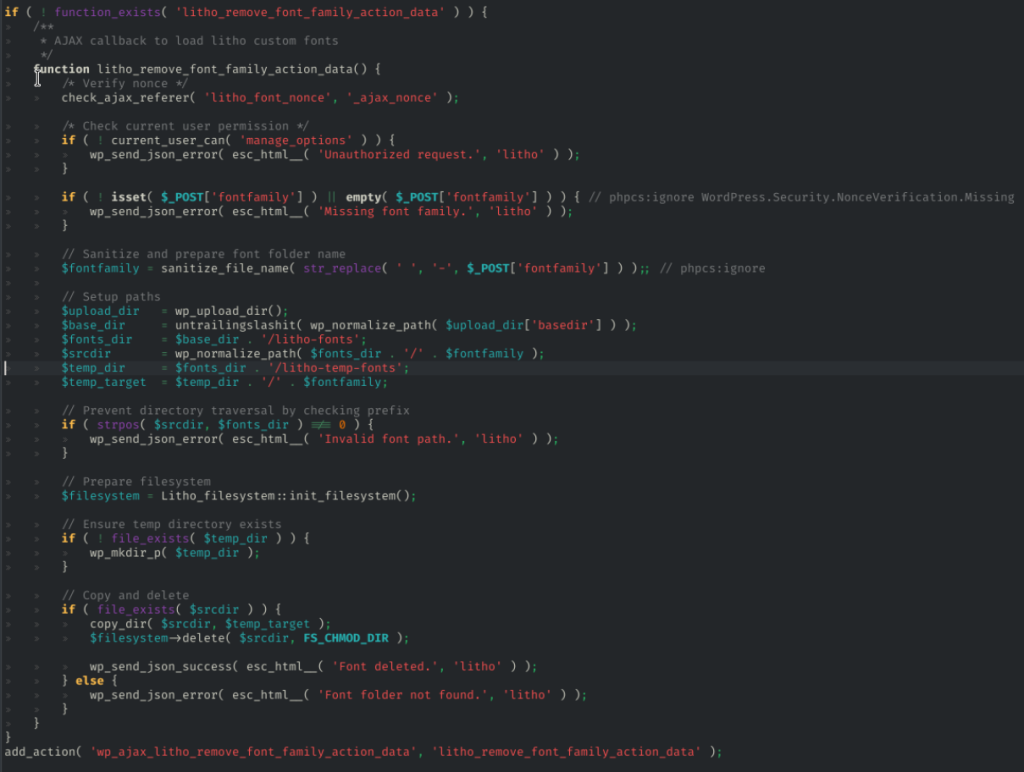
The main vulnerability existed in the function litho_remove_font_family_action_data:
if ( ! function_exists( 'litho_remove_font_family_action_data' ) ) {
/**
* AJAX callback to load litho custom fonts
*/
function litho_remove_font_family_action_data() {
if ( ! isset( $_POST['fontfamily'] ) || empty( $_POST['fontfamily'] ) ) { // phpcs:ignore WordPress.Security.NonceVerification.Missing
return;
}
$fontfamily = $_POST['fontfamily']; // phpcs:ignore
$fontfamily = str_replace( ' ', '-', $fontfamily );
$filesystem = Litho_filesystem::init_filesystem();
$upload_dir = wp_upload_dir();
$srcdir = untrailingslashit( wp_normalize_path( $upload_dir['basedir'] ) ) . '/litho-fonts/' . $fontfamily;// phpcs:ignore WordPress.Security.NonceVerification.Missing
$targetdir = untrailingslashit( wp_normalize_path( $upload_dir['basedir'] ) ) . '/litho-fonts/litho-temp-fonts';
$font_family_location = $targetdir . '/' . $fontfamily;
if ( ! file_exists( $targetdir ) ) {
wp_mkdir_p( $targetdir );
}
if ( ! file_exists( $font_family_location ) ) {
wp_mkdir_p( $font_family_location );
}
if ( file_exists( $srcdir ) ) {
copy_dir( $srcdir, $font_family_location );
$filesystem->delete( $srcdir, FS_CHMOD_DIR );
} else {
return true;
}
die();
}
}
add_action( 'wp_ajax_litho_remove_font_family_action_data', 'litho_remove_font_family_action_data' );
add_action( 'wp_ajax_nopriv_litho_remove_font_family_action_data', 'litho_remove_font_family_action_data' );Since there are no checks for whether the file type or the file name, and the action is added as 'nopriv' with no authentication or authorization checks, any attacker that has access to the WordPress site with the theme installed can delete any arbitrary files by supplying it to the 'fontfamily' POST parameter.
The patch
Instead of having an unauthenticated action with a critical functionality, the theme now validates the authentication, applies nonce checks against CSRF attacks, and sanitizes the supplied string.
Conclusion
Deleting files directly from users to the server always carries security risks. Both file extensions and file names should be thoroughly validated and sanitized to prevent arbitrary file deletions. Vendors should never rely on user-supplied file names, as they can be manipulated for attacks. Implementing proper access controls and restricting executable files can further enhance security.
Want to learn more about finding and fixing vulnerabilities?
Explore our Academy to master the art of finding and patching vulnerabilities within the WordPress ecosystem. Dive deep into detailed guides on various vulnerability types, from discovery tactics for researchers to robust fixes for developers. Join us and contribute to our growing knowledge base.
Timeline
🤝 You can help us make the Internet a safer place
Streamline your disclosure process to fix vulnerabilities faster and comply with CRA.
Get started for freeProtect your users too! Improve server health and earn added revenue with proactive security.
Patchstack for hostsReport vulnerabilities to our gamified bug bounty program to earn monthly cash rewards.
Learn more