Did you know that hackers can mimic your eCommerce checkout page and steal your revenue without your customers realizing they’re using a fraudulent form?
Or, were you aware that one of the easiest ways to attack a site is to exploit a WordPress plugin vulnerability?
We spoke to the ethical hackers in the Patchstack security community to understand how hackers choose target websites, what the process of a hack looks like, and what the consequences are. They referenced the cases they’ve worked on, all to help you answer the crucial question:
How can you protect your websites?
Let’s dive in!
First, how big is the risk of a hack for a regular WooCommerce or WordPress site?
Hackers don’t cherry-pick the right sites. Instead, they mass-launch automated attacks against as many sites as possible.
They’re not targeting you. They’re targeting websites with vulnerabilities. If your site is one of them, it will get attacked.
As for the actual process behind the screens, our interviewee explains:
“The easiest way is to mass-scan websites to determine if they use a known vulnerable component or plugin. Then, you check if the victims have valuable assets or information.
If not (and if the vulnerability allows hackers to execute code remotely), they can install an HTTP relay and resell the access to the site as a proxy farm. Remote Code Execution will also allow you to reach other sites hosted on the same server if they’re not properly isolated from each other.”
What happens when an eCommerce website is hacked?
“In several eCommerce website cases, the hacker added a script to the checkout page that sent them CC information.
In another case, they simply replaced the checkout page with their own, tricking customers. Since purchases were done with one-time password authorization, they were guaranteed to get the money – banks would not refund anything.”
In eCommerce cases, the consequences of an attack are pretty clear. You lose:
- Revenue
- Data
- Trust
- Reputation
- SEO rankings
And your customers can lose money and sensitive financial information.
Is my website safe if I don’t generate revenue through it?
Back in the day, I had 3 smaller websites. I never thought they’d get hacked because I wasn’t hosting anything of note on them. I thought I was safe, but it turns out: hackers are motivated to attack small sites, too.
Sure, they can’t always directly funnel revenue from them, like they do with eCommerce sites. However, there are still consequences:
- Website defacement: Hackers gain access and use your site to host pharma (and other types of) spam, ruining your reputation.
- SEO consequences: From manual penalties to getting de-ranked in the search engines sending you traffic (and customers), hacks wreak havoc on your SEO.
- Attacks: Your servers and IPs can be used to attack other sites.
- Compromising other sites on your server: If you use shared hosting and an attacker gains access to one of the sites hosted on the server, they’d be able to access others, as well.
Our interviewee explains the consequences clearly:
“For attacks on web apps, the main consequence was either a partial or a full server compromise. Then, hackers used the access they gained to that one server to reach other websites hosted on the same server.”
How long does it take for hackers to exploit websites?
The answer is straightforward:
“It can take a couple of minutes for hackers to exploit websites after they discover a vulnerability. ”
The exact time depends on how complex the exploit process is and how long it takes attackers to identify vulnerable websites.
In many cases, simple logical bugs like those found in plugin vulnerabilities result in the most sophisticated attacks:
“For example, in WordPress, a simple logical bug in the process of a plugin that allows users to sign up and set their roles [can lead to a profitable attack]. Another example that’s hard to detect is the insecure password reset process or social login process.”
These two are hard to detect because the behavior of the vulnerability exploits the check on a validation key that is supposed to be checked when performing the action.
In other words, the app/website can’t even “recognize” that the behavior is not legitimate.
What types of vulnerabilities are most frequently exploited?
“Unauthenticated vulnerabilities are the most likely to get exploited since most attackers are opportunists and just look for available targets.”
When our interviewee says “unauthenticated vulnerability,” they mean that exploiting some vulnerabilities doesn’t require access to a WordPress account.
Similarly, some vulnerabilities allow attackers to “upgrade” their low-privilege account (e.g., Contributor in WordPress) to an Administrator account.
“Usually, we see the following the most often: unauthenticated or low-level privilege escalation (from no account or a low-privilege account to an admin account), unauthorized or low-level Remote Code Execution (taking over the web server immediately, no questions asked), and SQL Injections.”
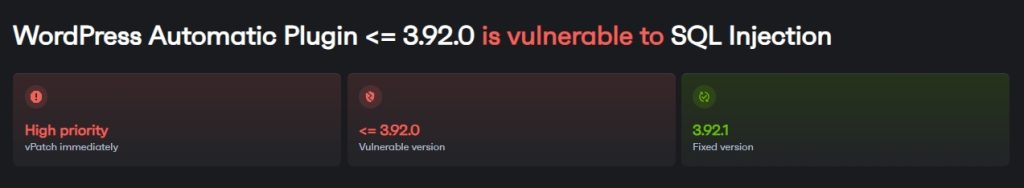
What does a typical SQL Injection vulnerability exploit scenario look like?
SQL Injection allows attackers to insert or "inject" malicious SQL code into a query, leading to giving them access to the database.
From there, they can retrieve data, manipulate it, or easily bring down the site.
“An SQL Injection is good for dumping the database and stealing information from customers and their accounts. Plus, if the site lacks proper data encryption, an SQL Injection could even lead to giving hackers passwords or payment information.”
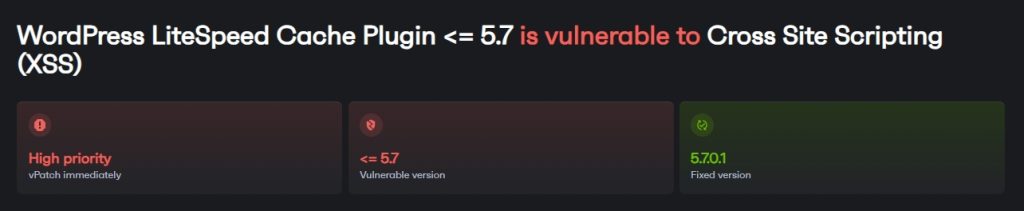
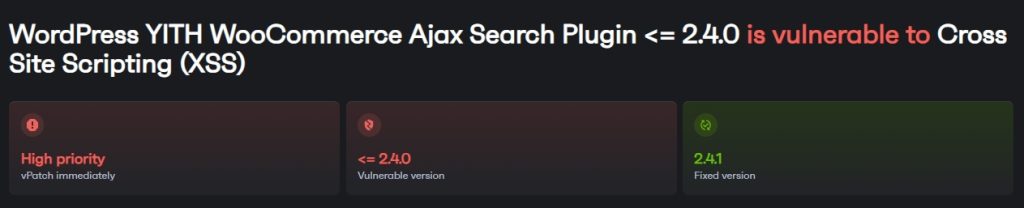
What does a typical Cross-Site Scripting (XSS) vulnerability exploit scenario look like?
Cross-Site Scripting (XSS) is typically found in websites and web apps. Attackers inject malicious scripts into web pages viewed by other users.
Then, the scripts can execute in the user’s browser, potentially stealing session cookies to impersonate legitimate users during attacks, defacing websites, or redirecting users to malicious sites.
“An XSS attack is, in my opinion, less likely to happen in spray-and-pray attacks. Instead, it’s very effective when targeting a specific domain – if you make your phishing very subtle and don’t make any mistakes.”
How can you recognize a hack?
Hacks aren’t always obvious. If something seems suspicious or you’ve received alerts, start looking for IOC (Indicators of Compromise):
“Look in the server’s requests logs for malicious requests, suspicious new user accounts with high privileges that you didn’t add, and pictures received or posted by random users that don't render.”
You might also notice a sudden and long-term increase in site loading time, or perhaps you receive a malware scan notification from your hosting company.
From there, you can run a server-side malware scan or a file integrity scan to see if there are any patterns of known malicious activity or changed files. As our Database Team Lead, Nestor Angulo de Ugarte, explained:
“File integrity monitoring is very useful in a WordPress environment because WordPress core files are fixed and shouldn’t be modified. The “wp-admin” folder and “wp-includes” folder, along with all core files in the site root folder, except “wp-config.php,” shouldn’t change except when we update the site. If there is a change, it’s clearly suspicious.”
How can you protect WooCommerce and WordPress websites from attacks?
Exploiting weaknesses in plugins, sites, and human nature? Yeah, it can feel like hackers are omniscient beings who can attack us no matter what we do. However, remember what our interviewee said earlier?
Hackers are opportunists.
And just like burglars, you can deter them with the right preventive measures:
“First, implement the principle of least privilege (PoLP) and only give access to users based on their needs. Second, always pay attention to your website's main software and the third-party components on it. For example in WordPress, always check for component updates on WordPress Core, plugins, and themes.”
And, to make your life easier, use threat mitigation tools.
You don’t have to stay exposed in the time between a vulnerability is discovered and the patch is issued.
Instead, use Patchstack.
It was designed to deal with vulnerability-specific threats and block your website from executing the code exploiting the logic flaws.
When the security community identifies a vulnerability, Patchstack puts a barrier between your site and the malicious actors attempting to exploit it.
You get real-time protection from attacks through virtual patching.
Then, update the vulnerable component in peace, and prevent revenue hits, downtime, SEO consequences, and the loss of trust.
Attacks are on the rise (but you are not powerless)
Finally, we couldn’t help but ask our ethical hackers for their predictions for the future. And just like in most industries, AI is bound to change things:
“In cybersecurity, AI will outperform any human in the coming years. With almost unlimited resources and speed, we can soon expect AI to uncover the most difficult and complex vulnerabilities in software. And with AI continuously studying and scanning thousands of plugins with the skills of the best cybersecurity gurus, we’ll see many more cases of exploitation.”
But you’re not powerless, and neither is the WordPress community.
With bug bounty programs like the Patchstack Alliance and Managed Vulnerability Disclosure Programs for plugins, as well as the rise of cybersecurity awareness through regulations like the Cyber Resilience Act, we have the tools to protect our community, revenue, and future.
And now that we understand the threat, it’s time to mitigate it.





