State of WordPress Security In 2025

In 2024 something happened that will fundamentally change the way open source software is built and maintained: on December 10th, the European Union’s Cyber Resilience Act (CRA) came into force. Its adoption went relatively unnoticed in WordPress circles, but in time it will prove to be a “GDPR moment” for software developers.
The first requirements of the CRA will apply already from 2026. By September 2026, open source developers — including plugin & theme authors — must have processes in place to notify authorities and users about actively exploited or severe vulnerabilities.
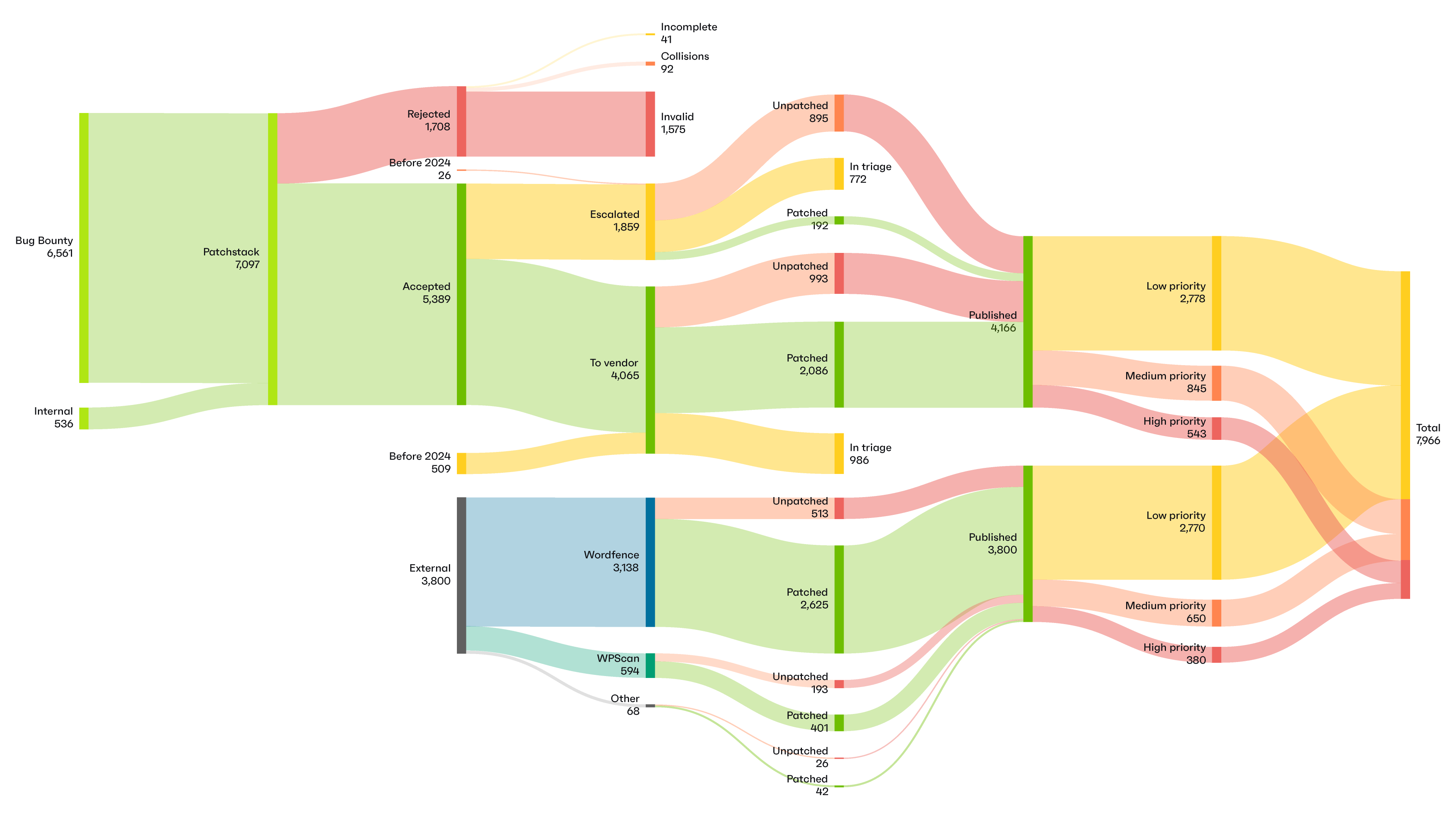
In 2024, 7,966 new vulnerabilities were found in the WordPress ecosystem, primarily in third-party plugins. That’s a 34% increase over 2023. While the majority of vulnerabilities don’t pose an active risk, high priority vulnerabilities were also up 11% year on year.
Perhaps the most surprising finding from 2024 is that more than half of the plugin developers to whom Patchstack reported a vulnerability did not patch the issue before official disclosure. This raises concerns about whether the WordPress ecosystem is ready for the CRA or other security regulations.
About Patchstack
Patchstack is the world's #1 WordPress vulnerability intelligence provider. We help hosting companies and website developers find and mitigate vulnerabilities in WordPress core, themes and plugins. Our mission is to make the open web more secure.
We’re a globally trusted security partner for many of the leading WordPress hosting companies. We provide a vulnerability management & mitigation solution to companies such as GoDaddy, Hostinger, Cloudways and many others.
Patchstack is backed by hundreds of ethical hackers through a global community called Patchstack Alliance. They actively search for new security vulnerabilities and potential threats so that Patchstack can notify its users and partners.
We also partner with over 600 software vendors such as Elementor, WP Rocket, YITH and others to secure their plugins and ensure they comply with the Cyber Resilience Act.
Patchstack is a member of the Open-Source Security Foundation, is backed by the European Innovation Council, and in 2024 was invited to Google's AI for Cybersecurity startup program.

Fastest vulnerability mitigation in WordPress

Public WordPress vulnerability database

Free vulnerability disclosure program for plugins

Vulnerability protection for hosts
WordPress security by the numbers
7,966 new security vulnerabilities were found in the WordPress ecosystem in 2024. That’s about 22 new vulnerabilities per day.
96% of the vulnerabilities were uncovered in plugins, and 4% were found in themes. Only seven vulnerabilities were uncovered in WordPress core itself, but none of those were significant enough to pose a widespread threat.
Patchstack was responsible for coordinating the disclosure of 52% of all new vulnerabilities in 2024, through the combined efforts of our internal research team and our Patchstack Alliance community. While the numbers of WPScan have significantly dropped year on year, we see an increase in the number of vulnerability disclosures coordinated by Wordfence.
Patchstack disclosed 52% of all new vulnerabilities in 2024
Patchstack disclosed the highest number of medium and high severity vulnerabilities
96% of the vulnerabilities were found in plugins
An increase in vulnerabilities requires better prioritization
As the number of vulnerabilities has increased it is more difficult to filter out what truly matters. Due to the specific characteristics of WordPress, the standard CVSS (Common Vulnerability Scoring System) scale rarely gives vulnerabilities a low severity.
The majority of vulnerabilities receive a medium CVSS score, even when they require high user privileges and cannot be exploited in a real-life scenario. We also commonly see cases when such vulnerabilities receive high-severity CVSS scores.
This creates a problem: when everything is important, nothing is.
In 2023 we released the Patchstack Priority scoring system and predicted that the volume of uncovered vulnerabilities would grow significantly over time. We knew that continued reliance on the CVSS scoring system would lead to alert fatigue and people would miss important issues.
Patchstack Priority Score
To create the Patchstack Priority scoring system, we analyzed all of the available historical data about vulnerabilities known to be exploited in the WordPress ecosystem. It takes into account the prerequisites, vulnerability type, exploitation complexity, active install counts, and more. Based on these markers, the system categorizes all security vulnerabilities into low, medium, and high priority.
Out of the 7,966 vulnerabilities uncovered in 2024, 11.6% received a high Patchstack Priority score. These vulnerabilities are expected to be exploited or are already known to be exploited. 18.8% received a medium score, which means they could be exploited in more targeted attacks. 69.6% of the vulnerabilities received a low score which we consider unlikely to be exploited.
30% of new vulnerabilities had significant risk of exploitation
When we look into how CVSS scores have been assigned for the same vulnerabilities, only 0.48% of vulnerabilities received low severity and 64.70% of vulnerabilities were assigned medium severity. A high or critical CVSS score was assigned to 34.82% of vulnerabilities.
As we automatically deploy virtual patching rules to our customers for all medium and high-priority vulnerabilities and track the vulnerability exploitations in real-time, we’ve calculated that Patchstack Priority helps our users cut noise by 69.5%.
CVSS often assigns too high severity for low impact WordPress vulnerabilities
43% of all vulnerabilities uncovered in 2024 required no authentication - at least for the attacker
43% of new vulnerabilities found in 2024 did not require any authentication to be exploited. While vulnerabilities with an unauthenticated prerequisite tend to be easier to exploit, it’s not always the case.
For example, a CSRF (Cross-Site Request Forgery) vulnerability is exploited by tricking the user into clicking a link or visiting a malicious page that will then execute a certain action under their own session. This happens when a nonce token is not being checked in the request.
These results skew the unauthenticated related severity results as vulnerabilities are judged from the perspective of the attacker. Since the attacker does not need authentication in order to exploit a CSRF vulnerability, it is rated as unauthenticated by nature.
Vulnerabilities by prerequisite
Cross-Site Scripting (XSS) remains the most widespread vulnerability
Cross-site scripting (XSS) could allow a bad actor to inject malicious scripts, such as redirects, advertisements, and other HTML payloads, into your website. These are executed when guests visit your site or on specific pages on the administration interface for authenticated users.
XSS is a relatively easy security bug to find, and one security researchers often look for. It’s not surprising that in 2024 it was also the most commonly reported vulnerability type, making up almost half of all the new entries.
Due to its potential severity (especially in the case of unauthenticated site-wide stored XSS), Patchstack often incentivizes researchers to find that particular vulnerability, contributing to its “popularity”.
Most commonly reported vulnerabilities
Vulnerabilities in popular plugins
There’s a security myth in WordPress that using popular and trusted plugins guarantees security.
Software development is hard and security bugs happen everywhere. In addition, not all teams have dedicated security processes in place and some popular plugins don’t have much of a team at all.
1,018 vulnerabilities were found last year in components with at least 100,000 installs - of these, 153 received a High or Medium Patchstack Priority score. This demonstrates that install count is not a good indicator of security. If anything, a high install count makes plugins attractive targets for attackers.
Fewer vulnerabilities are found in popular plugins, but the potential impact is greater
The most popular plugins with severe vulnerabilities
We looked at how many high-severity vulnerabilities were found in plugins with at least 100,000 installs to find the most impactful ones from 2024.
Last year’s charts were heavily dominated by LiteSpeed Cache. Patchstack paid out the largest bounty in Patchstack history for a single vulnerability: $16,400 for the Privilege Escalation vulnerability in LiteSpeed Cache. This prompted our researchers and the community to dig deeper into the plugin, and five high severity issues were found.
This does not mean that LiteSpeed Cache is an insecure plugin. Instead, it’s a good example of how bug bounties can motivate researchers to spend time digging out security issues that might otherwise remain hidden from everyone except bad actors.
Most popular plugins with severe vulnerabilities
Component | Install count | Vulnerability | CVSS | Discovered by |
 LiteSpeed Cache | 6,000,000 | Privilege Escalation | 8.1 | TaiYou (Patchstack Alliance) |
 LiteSpeed Cache | 6,000,000 | Broken Authentication | 9.8 | Rafie Muhammad (Patchstack) |
 LiteSpeed Cache | 6,000,000 | Privilege Escalation | 9.8 | John Blackbourn (Patchstack Alliance) |
 LiteSpeed Cache | 6,000,000 | Cross Site Scripting (XSS) | 8.3 | Rafie Muhammad (Patchstack) |
 LiteSpeed Cache | 6,000,000 | Broken Access Control | 8.2 | Rafie Muhammad (Patchstack) |
Really Simple SSL | 4,000,000 | Broken Authentication | 9.8 | Istv√°n M√°rton |
 Better Search Replace | 1,000,000 | PHP Object Injection | 9 | Sam Pizzey (mopman) |
 Loginizer | 1,000,000 | Broken Authentication | 8.1 | wesley (wcraft) |
 The Events Calendar | 700,000 | SQL Injection | 9.3 | Foxyyy |
 WPvivid Backup and Migration | 400,000 | SQL Injection | 9.3 | Denis Werner |
The most actively exploited new vulnerabilities
The following new vulnerabilities uncovered in 2024 have been most actively exploited based on our virtual patch hit data.

LiteSpeed Cache Plugin
WordPress Automatic Plugin

Startklar Elementor Addons Plugin

GiveWP Plugin

GiveWP Plugin
More than 500,000 websites infected in 2024

Sucuri alone observed over 500,000 websites that became infected in 2024 - but this is just the tip of the iceberg. It’s impossible to see the full extent of the malware problem from the data of a single provider.
Nevertheless, Sucuri’s data offers some insight into the most common malware types.
WordPress core, plugin and theme vulnerabilities are to blame for almost half of the malware infections. Rest is related to poor security hygiene that enables hackers to hijack sessions from infected devices or use leaked usernames and passwords to get admin access.
Looking at the data it is important to understand that while vulnerabilities remain one of the biggest threats in the WordPress ecosystem, users need to adopt a multi-layered approach to security. This involves having appropriate tools to manage threats on the application, network and server levels.
Users also need better security hygiene – strong unique passwords, 2 factor-authentication and thoughtful access management should be as elementary as brushing your teeth.
SEO spam
This form of malware involves manipulating search engine optimization (SEO) techniques to fraudulently boost the visibility of certain content, often redirecting legitimate traffic to malicious or irrelevant sites.
Sucuri’s data indicates a total of 422,466 incidents related to SEO spam, showcasing the varied methods employed to exploit search engine algorithms. Japanese SEO Spam emerged as the most prevalent, accounting for 27.77% of incidents. This tactic involves injecting Japanese text and links into vulnerable websites, often to promote counterfeit goods or phishing sites.
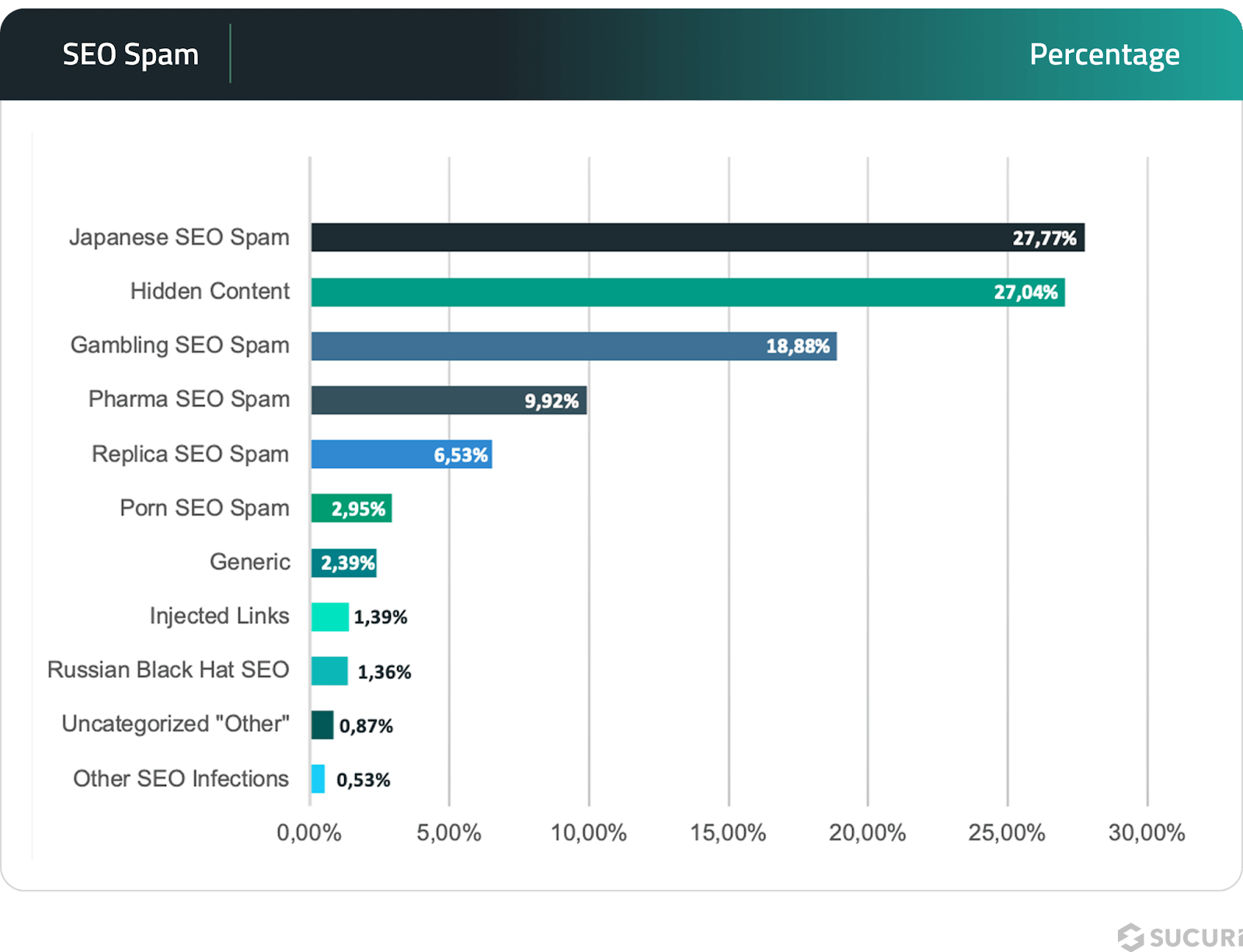
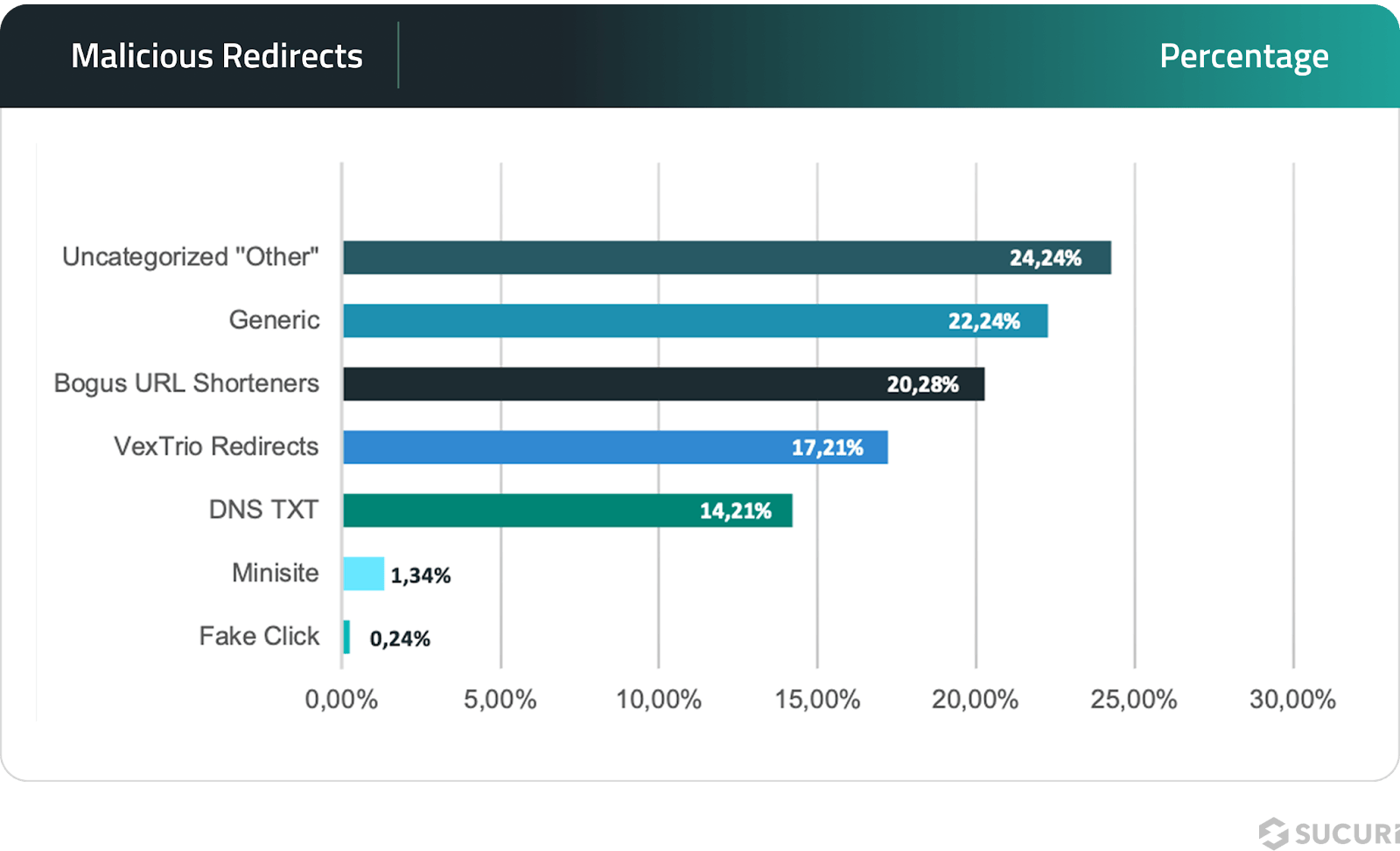
Malicious redirects
These redirects covertly reroute users from their intended destinations to harmful or deceptive sites, often exploiting vulnerabilities in website code or configurations.
There were 175,520 incidents involving malicious redirects, with a variety of tactics employed to mislead and exploit users.
Bogus URL Shorteners accounted for 20.38% of incidents, using misleading short links to guide users to malicious sites. These shorteners disguise harmful destinations under the guise of legitimate URLs, making them particularly deceptive.
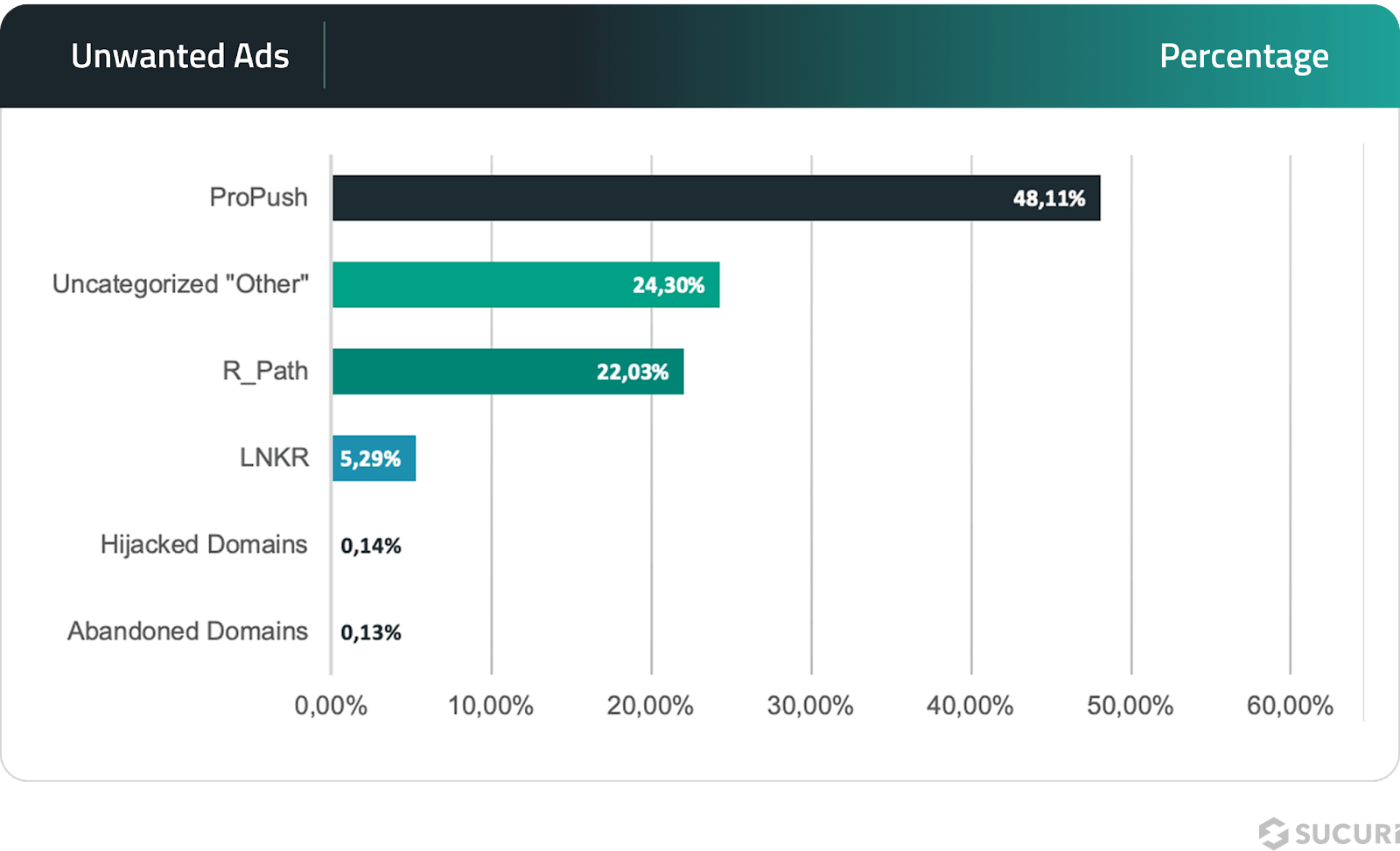
Unwanted ads
According to Sucuri, a total of 16,274 incidents were linked to unwanted ads, with a diverse range of tactics employed by attackers.
ProPush emerged as the most prevalent threat, accounting for 48.11% of all unwanted ad incidents. This tactic often involves tricking users into subscribing to push notifications that lead to spammy or harmful sites.
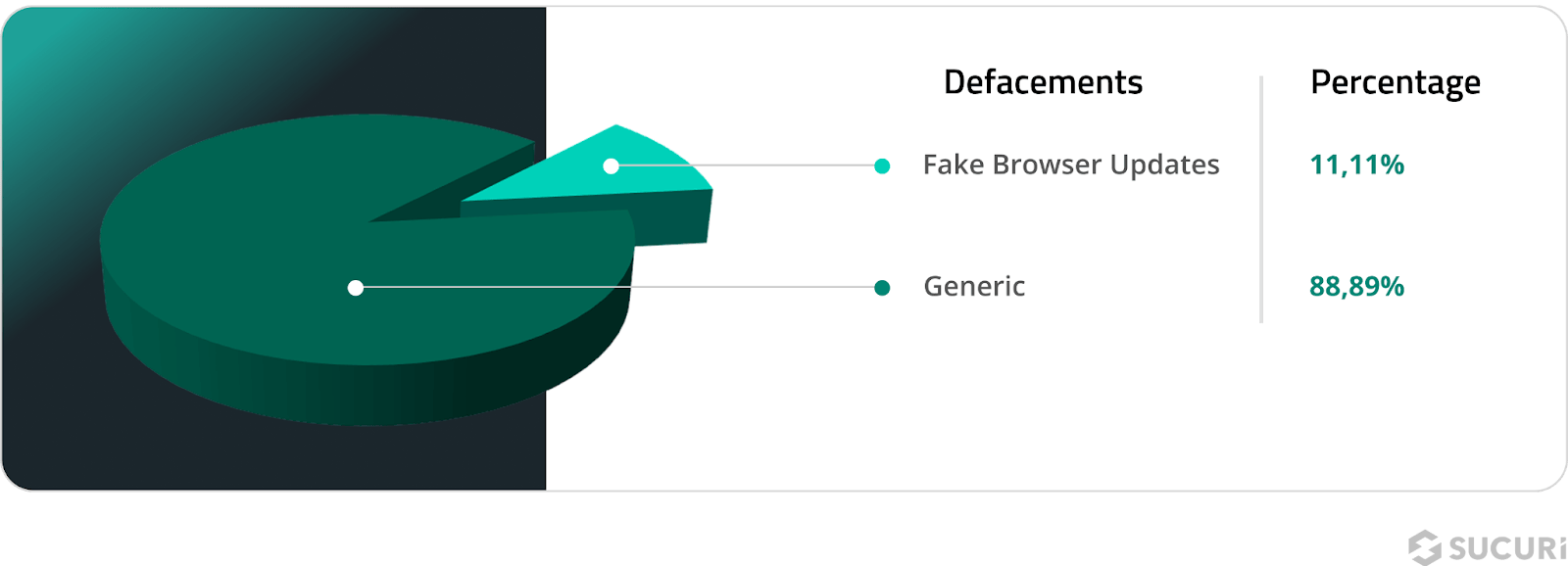
Website defacements
These attacks involve unauthorized modifications to a website's appearance or content, often to display messages, images, or propaganda chosen by the bad actor.
Sucuri’s analysis detected a total of 8,452 defacement incidents. Generic Defacements accounted for 88.89% of these incidents. These attacks typically involve altering the homepage or other visible areas of a site.
WordPress security needs new strategies
Relying on updates is not enough to be safe
We commonly see people give the advice that to keep your website secure all you need to do is update plugins.
While only using necessary plugins and enabling auto-updates may indeed keep you out of trouble for a while, the data shows that it’s not enough.
In 2024, 33% of vulnerabilities were not fixed in time for public disclosure. Many of the vulnerabilities were disclosed in abandoned plugins and will likely never receive a patch. Most of them still have active installations; these insecure plugins remain installed and active across the web.
It’s also common that the auto updates are turned off as website developers want to ensure that the new releases don’t include any breaking changes. That immediately increases the risk factor as it’s common for vulnerabilities to become exploited in a matter of hours after public disclosure. This happened in early 2024 with a Remote Code Execution vulnerability found in Bricks Builder.
Generic WAF solutions fail to address WordPress attacks
A security researcher from the Patchstack Alliance reported a vulnerability in Bricks Builder. We coordinated the disclosure with the Bricks Builder team and deployed virtual patching rules to our affected customers’ websites before the vulnerability was made public.
A few hours after the vulnerability was disclosed, multiple IP addresses ran scripted mass exploitation campaigns to gain access to vulnerable websites and plant malware. Patchstack customers received automatic protection from the exploitation but as we monitored the attacks across our network we received reports that all of the popular WAF solutions used by hosting companies failed to prevent the Bricks attacks.
This was caused by the lack of threat intelligence and visibility into the WordPress applications and sessions. Generic WAF solutions deployed via DNS/CDN (e.g. network-level firewalls such as Cloudflare) don’t have visibility into the application components, which plugins are installed, which users are authenticated and what kind of authorization they have.
Similar limitations are present in server-level WAF solutions such as ModSec. With server access, you can deploy custom rules based on installed plugin versions, but accuracy is limited due to an inability to see into WordPress sessions, which in the case of the aforementioned Remote Code Execution (RCE) vulnerability in Bricks Builder caused severe false-positives.
Most solutions rely on generic pattern-based rulesets, which are optimized to balance effectiveness with the number of false positives. This means that many WordPress-specific vulnerabilities go undetected as the providers don’t focus on WordPress, don’t keep up with WordPress threat intelligence, and therefore lack the technical capability to deploy vulnerability-specific rules.
WordPress malware-scanning plugins get bypassed by malware
When attackers successfully exploit a website they try to make sure they are not kicked out. Hackers often hide malware inside the compromised website so they can later use it to launch attacks on other websites as part of a botnet.
It’s widely known that popular security plugins used for malware scanning are disabled, bypassed and even completely removed by malware. In 2023, the security company WeWatchYourWebsite identified 58,848 malware-infected WordPress websites that had Wordfence installed prior to infection and in 14% of the cases malware tampered with the Wordfence files to stay hidden.
The same happens with other popular plugins that provide malware scanning capabilities; this has become more common in 2024. This type of malware is now common and was used, for example, in the Bricks Builder RCE vulnerability attacks mentioned above.
We actively discourage the use of any plugin-based malware scanners and recommend selecting a hosting provider who runs malware scans on a deeper level as part of their service.
Vulnerability management & virtual patching is essential
Not only is vulnerability management, mitigation and reporting (like SBOMs) required by different existing and upcoming regulations - it has also proven to be the most effective way to prevent nearly half of the malware infections that affect WordPress websites. What we need is a combination of deep understanding of emerging threats, and an ability to act on them before hackers do.
This is where Patchstack really excels. As the leading threat intelligence provider for the WordPress ecosystem, and having a complete visibility into the WordPress application (including sessions), we can automatically and precisely deploy the correct virtual patching rules to mitigate the vulnerabilities present on the website - including the 33% of which don’t have official patches available. All of that without any changes to code, performance disruption or false-positives. To date Patchstack has virtual patches for more than 10,000 vulnerabilities, and we’re making new ones available every day. This is by far, the largest and most complete collection of any kind of WordPress specific security rules available on the market.
“Patchstack is like CrowdStrike, but for websites!”
Get Patchstack
Lack of security processes increases risk and exposure
The risk of abandoned plugins and lack of security procedures
Unpatched and abandoned plugins have become a more significant security risk in WordPress. Abandoned plugins are not flagged for users even when they are removed from the WordPress.org repository for security reasons. This leaves many users unwittingly exposed (an issue we have raised since 2023).
Last year, a total of 1,614 plugins and themes were removed from the WordPress repository for unpatched security issues. Of these, the vast majority (1,450) had High and Medium priority vulnerabilities:
The flowchart highlights another problem: low quality reports of vulnerabilities that pose no real threat. In 2024, Patchstack has helped plugin developers filter out more than 1500 of these kinds of reports. Our threat intelligence & vulnerability triage team is equipped for this kind of work, but it can be a significant undertaking for any plugin developer who does not have a dedicated security team.
It is easy for plugin developers to get overwhelmed with vulnerability reports and, with beg bounties in the mix, real vulnerabilities can go unnoticed. To keep users protected and trust intact, it is crucial to filter out noise and reach to real vulnerabilities as fast as possible.
To address this problem, in September 2024, with the support of the European Commission, Patchstack launched a free vulnerability disclosure platform (mVDP) to enable WordPress plugin developers to set up a streamlined and secure vulnerability reporting system and become compliant with the European Cyber Resilience Act.

Free security tooling for plugins
The Patchstack Alliance’s impact
It takes a village to find vulnerabilities. In this section we’ll look in depth at the contributions made by the security researchers in our bug bounty program. In 2024, we received 4,853 valid vulnerability reports from 179 security researchers, almost twice the number of reports received in 2023.
428 of those reports were for plugins in Patchstack’s mVDP. For these reports, security researchers earn higher rewards and Patchstack helps the plugin developer to quickly release a high-quality patch and coordinate the disclosure.
97% of the vulnerabilities were uncovered in plugins hosted by WordPress.org. Vulnerabilities were also reported in plugins exclusively hosted in Github and we received vulnerability reports for more than 100 WordPress products sold on the Envato marketplace.
The reports also led to the closure of a whopping 1,614 abandoned plugins. These were removed from the WordPress.org repository after attempts to contact the respective developers to fix the security issues.
In August 2024, we also set the record for the highest bounty ever paid in the WordPress ecosystem for a single vulnerability; $16,400 for John Blackbourn's discovery of a critical zero-day privilege escalation vulnerability in the Litespeed Cache plugin.
Later, in October we set another record during our special WordPress security cleanup event for the Cybersecurity Month, resulting in 1,000+ plugins temporarily removed from the repository due to unpatched security issues.
Patchstack Alliance is an open community for everyone interested in open source security. Security researchers can participate in our ongoing bug bounty program in which rewards are paid for the discovery of new vulnerabilities that are then responsibly reported to the software developers. This helps make our ecosystem more secure.
2025 and beyond
The end of 2024 introduced a lot of uncertainty into the WordPress ecosystem. The dispute between Automattic and WP Engine became public in September 2024 and is having a profound effect on WordPress businesses and the community as a whole.
Trust in WordPress.org has been broken as project norms and implicit agreements have been undermined. WP Engine-hosted sites were disconnected from WordPress.org updates, presenting a major security issue for all WP Engine customers as well as the company itself. Plugin developers became aware of the precarious standing of their plugins within the repository when WP Engine’s Advanced Custom Fields was replaced by WordPress.org’s Secure Custom Fields, signaling that any plugin could be replaced by WordPress.org at any time.
Public criticism of these and other actions has led to prominent contributors being banned from WordPress.org and from the Make WordPress Slack. Businesses have been rejected from WordCamps as sponsors, speakers, and as attendees. This has led to instability in the WordPress community and amongst its contributors. Many remain silent in order to keep jobs that rely on access to WordPress.org or to ensure the plugins that power their small businesses remain hosted in the repository. Amongst those who are speaking up, the community is fragmenting with new initiatives such as unofficial WordPress conferences, repository mirrors and even forks.
In 2025, security concerns within WordPress extend beyond code. Businesses that rely upon WordPress, along with many community members, see governance and instability within the community as one of the project’s main security issues. Organizations that prioritize security are concerned about the integrity of the supply chain controls that hold the keys to nearly half of the global web.
Meanwhile, the full implementation of the Cyber Resilience Act (CRA) is coming upon us fast. This change is coming and cannot be ignored. The WordPress Foundation is considered a software steward by the CRA and that comes with requirements on both governance and security.
The same applies to software companies who build WordPress plugins. As long as they have users in the EU, they will be considered a manufacturer under the CRA and must follow the security requirements set by the regulation. This starts with vulnerability disclosure programs in 2026.
AI & WordPress Security
It’s impossible to ignore artificial intelligence. AI-powered tools are already actively used in the WordPress ecosystem, introducing new risks and opportunities. GenAI is a powerful new technology which makes building products easier but, exactly like humans, it can and will make mistakes.
We predict four main areas where AI will have an impact on WordPress security:
- AI-generated code will introduce new vulnerabilities
- It will become easier to find new vulnerabilities
- Vulnerabilities will become exploited faster
- AI will make previously low priority vulnerabilities easier to exploit
2024 saw a significant uptick in AI generated code, particularly in plugins. We have uncovered security vulnerabilities in AI-generated plugins where the author was either not careful enough or who was too trusting of the code. With GenAI, shipping functional software does not require any coding experience. When the author lacks coding skills there is no one to validate the code quality and security before it is released to the public.
AI can not only generate code, it can analyze it for specific use cases, such as finding security mistakes. The Patchstack AI/ML team has been working on an AI vulnerability scanner since 2023. In 2024, Patchstack was invited to the Google AI/Cybersecurity program where we received support to build a tool that is capable of generating deep understanding about the entire codebase and has independently discovered CVEs in popular WordPress plugins. While work to make this accessible to all plugin developers, we must accept the reality that it’s a matter of time until similar tools become accessible to cyber criminals as well.
In addition to finding vulnerabilities, AI agents are capable of exploiting them. The most successful attacks happen when software does not yet have a patch for a vulnerability or when the majority of users are not yet up-to-date. Using AI to generate exploitation scripts can significantly reduce the time it takes to weaponise a vulnerability. After exploitation, AI is also an ideal tool to create polymorphic malware, which can stay undetected by most pattern based scanners.
Regulations and supply chain security
The number of times regulations are mentioned in this whitepaper is a dead giveaway that we’re from Europe. Jokes aside, software security processes and supply chain security is something WordPress ecosystem needs to pay attention to in 2025. At a minimum, everyone needs to stay compliant with new regulations, but we hope that businesses and developers strive to take security seriously and be trustworthy in the eyes of users.
The current community distrust towards WordPress.org - the only mechanism to access WordPress core, plugin, and theme updates - has ignited projects which either provide a back-up as a mirror of the official WordPress plugin repository or allow updates to be pulled directly from Github if the plugin is hosted there (such as git-updater that has now over 3.2K stars). There are also initiatives such as AspirePress which is working on a distributed package repository for WordPress with code signing and authenticity checking.
Apart from regulations, there's a growing demand for improved supply chain security within the community. This signals that security won’t just be approached as a box-ticking exercise, but to actually improve the WordPress ecosystem for the better.
References
https://digital-strategy.ec.europa.eu/en/policies/cyber-resilience-act
https://patchstack.com/articles/patchstack-introducing-patchstack-priority/
https://patchstack.com/articles/virtual-patching/
https://patchstack.com/database/
https://patchstack.com/articles/cheese-cake-and-cybersecurity-protecting-your-wordpress-website/
https://patchstack.com/articles/critical-rce-patched-in-bricks-builder-theme/
https://patchstack.com/articles/interview-with-john-blackbourn/
https://patchstack.com/articles/nearly-1000-plugins-closed-during-wordpress-security-cleanup/
https://wewatchyourwebsite.com/how-we-identified-nearly-150k-hacked-wordpress-sites-in-60-days
https://gist.github.com/lynt-smitka/1eef476aed934fd3bc0be0813ea82f39
https://sucuri.net
https://wordpress.tv/2023/09/30/state-of-wordpress-security-insights-from-2022/

Francesca Marano
Enterprise sales & partnerships





Patchstack works with all popular webhosts





Manage & mitigate vulnerabilities in your WordPress, Drupal & Joomla sites

Easily mitigate vulnerabilities at scale with the fastest intel on the market

Join our Discord Community and get help, recommendations, and solutions for WordPress security from fellow community members.